Microsoft 70-465 Exam Practice Questions (P. 4)
- Full Access (64 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
DRAG DROP -
You plan to deploy SQL Server 2014.
Your company identifies the following monitoring requirements:
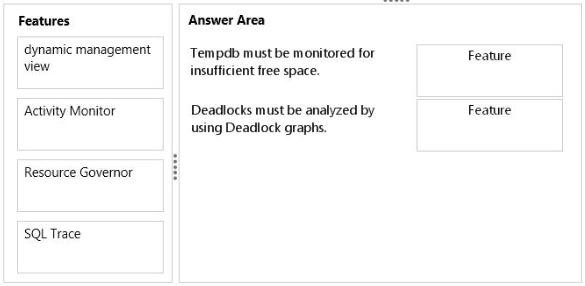
✑ Tempdb must be monitored for insufficient free space.
Deadlocks must be analyzed by using Deadlock graphs.

You need to identify which feature meets each monitoring requirement.
Which features should you identify?
To answer, drag the appropriate feature to the correct monitoring requirement in the answer area.
Select and Place:
You plan to deploy SQL Server 2014.
Your company identifies the following monitoring requirements:
✑ Tempdb must be monitored for insufficient free space.
Deadlocks must be analyzed by using Deadlock graphs.

You need to identify which feature meets each monitoring requirement.
Which features should you identify?
To answer, drag the appropriate feature to the correct monitoring requirement in the answer area.
Select and Place:

Correct Answer:
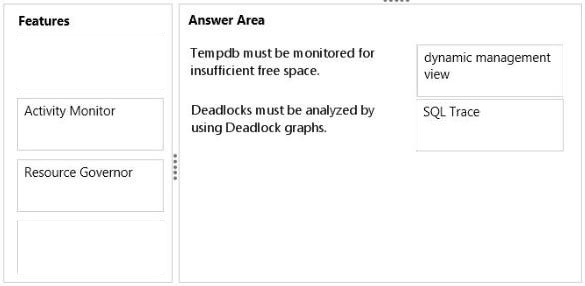
* You can use the sys.dm_db_file_space_usage dynamic management view to monitor the disk space used by the user objects, internal objects, and version stores in the tempdb files. Additionally, to monitor the page allocation or deallocation activity in tempdb at the session or task level, you can use the sys.dm_db_session_space_usage and sys.dm_db_task_space_usage dynamic management views. These views can be used to identify large queries, temporary tables, or table variables that are using a large amount of tempdb disk space.
*
/ Use SQL Server Profiler to identify the cause of a deadlock. A deadlock occurs when there is a cyclic dependency between two or more threads, or processes, for some set of resources within SQL Server. Using SQL Server Profiler, you can create a trace that records, replays, and displays deadlock events for analysis.
/ SQL Server Profiler and SQL Server Management Studio use a deadlock wait-for graph to describe a deadlock. The deadlock wait-for graph contains process nodes, resource nodes, and edges representing the relationships between the processes and the resources.
Reference:
Troubleshooting Insufficient Disk Space in tempdb
Reference:
Analyze Deadlocks with SQL Server Profiler

* You can use the sys.dm_db_file_space_usage dynamic management view to monitor the disk space used by the user objects, internal objects, and version stores in the tempdb files. Additionally, to monitor the page allocation or deallocation activity in tempdb at the session or task level, you can use the sys.dm_db_session_space_usage and sys.dm_db_task_space_usage dynamic management views. These views can be used to identify large queries, temporary tables, or table variables that are using a large amount of tempdb disk space.
*
/ Use SQL Server Profiler to identify the cause of a deadlock. A deadlock occurs when there is a cyclic dependency between two or more threads, or processes, for some set of resources within SQL Server. Using SQL Server Profiler, you can create a trace that records, replays, and displays deadlock events for analysis.
/ SQL Server Profiler and SQL Server Management Studio use a deadlock wait-for graph to describe a deadlock. The deadlock wait-for graph contains process nodes, resource nodes, and edges representing the relationships between the processes and the resources.
Reference:
Troubleshooting Insufficient Disk Space in tempdb
Reference:
Analyze Deadlocks with SQL Server Profiler
send
light_mode
delete
Question #17
DRAG DROP -
You plan to deploy three highly available SQL Server environments that will use SQL Server 2014.
You identify the following specifications for each environment as shown following table.
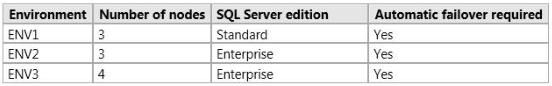
You need to recommend which high-availability feature is required for each environment.
Which features should you identify?
To answer, drag the appropriate feature to the correct requirement in the answer area.
Select and Place:
You plan to deploy three highly available SQL Server environments that will use SQL Server 2014.
You identify the following specifications for each environment as shown following table.

You need to recommend which high-availability feature is required for each environment.
Which features should you identify?
To answer, drag the appropriate feature to the correct requirement in the answer area.
Select and Place:

Correct Answer:
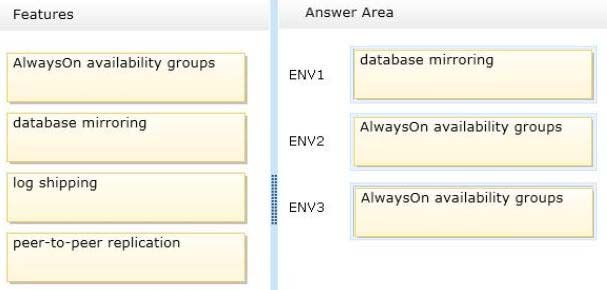
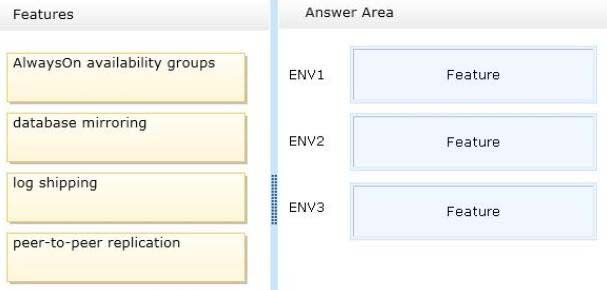
* Always on availability groups
The AlwaysOn Availability Groups feature is a high-availability and disaster-recovery solution that provides an enterprise-level alternative to database mirroring.
Introduced in SQL Server 2012, AlwaysOn Availability Groups maximizes the availability of a set of user databases for an enterprise.
Deploying AlwaysOn Availability Groups requires a Windows Server Failover Clustering (WSFC) cluster.
References:
AlwaysOn Availability Groups (SQL Server)
Features Supported by the Editions of SQL Server 2014

* Always on availability groups
The AlwaysOn Availability Groups feature is a high-availability and disaster-recovery solution that provides an enterprise-level alternative to database mirroring.
Introduced in SQL Server 2012, AlwaysOn Availability Groups maximizes the availability of a set of user databases for an enterprise.
Deploying AlwaysOn Availability Groups requires a Windows Server Failover Clustering (WSFC) cluster.
References:
AlwaysOn Availability Groups (SQL Server)
Features Supported by the Editions of SQL Server 2014
send
light_mode
delete
Question #18
DRAG DROP -
You plan to deploy a database by using SQL Server 2014.
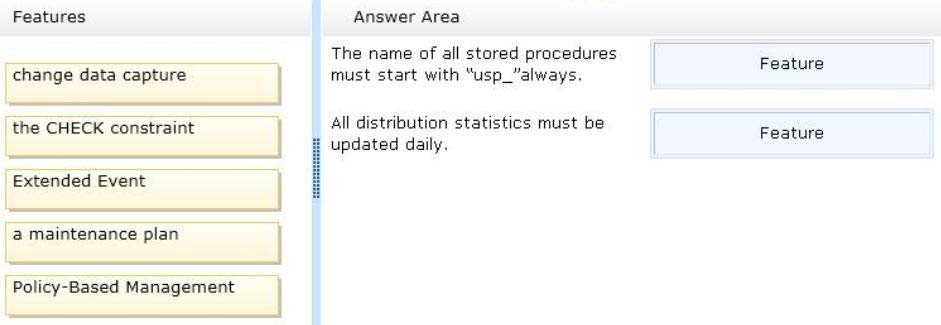
Your company identifies the following requirements for the database:
✑ The name of all stored procedures must start with "usp_"always.
All distribution statistics must be updated daily.

You need to identify which feature must be used to meet each database requirement.
Which features should you identify?
To answer, drag the appropriate feature to the correct database requirement in the answer area.
Select and Place:
You plan to deploy a database by using SQL Server 2014.
Your company identifies the following requirements for the database:
✑ The name of all stored procedures must start with "usp_"always.
All distribution statistics must be updated daily.

You need to identify which feature must be used to meet each database requirement.
Which features should you identify?
To answer, drag the appropriate feature to the correct database requirement in the answer area.
Select and Place:

Correct Answer:
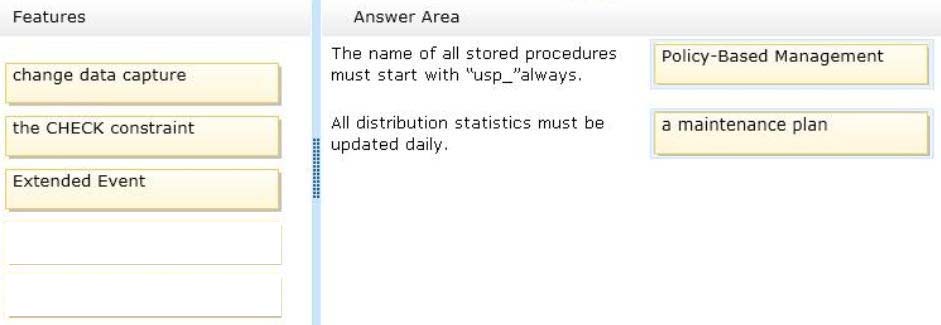
* Policy-Based Management
Each Stored Procedure that are created and that will be created has to have prefix "USP_".
* Maintenance plans create a workflow of the tasks required to make sure that your database is optimized, regularly backed up, and free of inconsistencies.
References:
How to: Create and Configure a Policy-Based Management Policy
Maintenance Plans

* Policy-Based Management
Each Stored Procedure that are created and that will be created has to have prefix "USP_".
* Maintenance plans create a workflow of the tasks required to make sure that your database is optimized, regularly backed up, and free of inconsistencies.
References:
How to: Create and Configure a Policy-Based Management Policy
Maintenance Plans
send
light_mode
delete
Question #19
You are troubleshooting an application that runs a query. The application frequently causes deadlocks.
You need to identify which transaction causes the deadlock.
What should you do?
More than one answer choice may achieve the goal. Select the BEST answer.
You need to identify which transaction causes the deadlock.
What should you do?
More than one answer choice may achieve the goal. Select the BEST answer.
- AQuery the sys.dm_exec_sessions dynamic management view.
- BQuery the sys.dm_exec_requests dynamic management view.
- CCreate a trace in SQL Server Profiler that contains the Deadlock graph event
- DCreate an extended events session to capture deadlock information.
Correct Answer:
D
Troubleshooting deadlocks -
You have been receiving reports from users indicating that certain applications are returning deadlock errors. To maximize the effectiveness of troubleshooting these problems, you decide to focus on the deadlocks that are hit most frequently. You create an Extended Events session that:
/ Configures deadlock event tracking for the session.
/ Specifies a target that aggregates based on an identifier for the deadlock.
You run the Extended Events session, and after additional deadlocks are reported you are able to obtain aggregated deadlock information, along with the complete XML deadlock graph for each source. Using this information you are able to pin point the most common deadlocks and start working on a solution.
Create an Extended Events Session
View Event Session Data
D
Troubleshooting deadlocks -
You have been receiving reports from users indicating that certain applications are returning deadlock errors. To maximize the effectiveness of troubleshooting these problems, you decide to focus on the deadlocks that are hit most frequently. You create an Extended Events session that:
/ Configures deadlock event tracking for the session.
/ Specifies a target that aggregates based on an identifier for the deadlock.
You run the Extended Events session, and after additional deadlocks are reported you are able to obtain aggregated deadlock information, along with the complete XML deadlock graph for each source. Using this information you are able to pin point the most common deadlocks and start working on a solution.
Create an Extended Events Session
View Event Session Data
send
light_mode
delete
Question #20
DRAG DROP -
You plan to deploy SQL Server 2014.
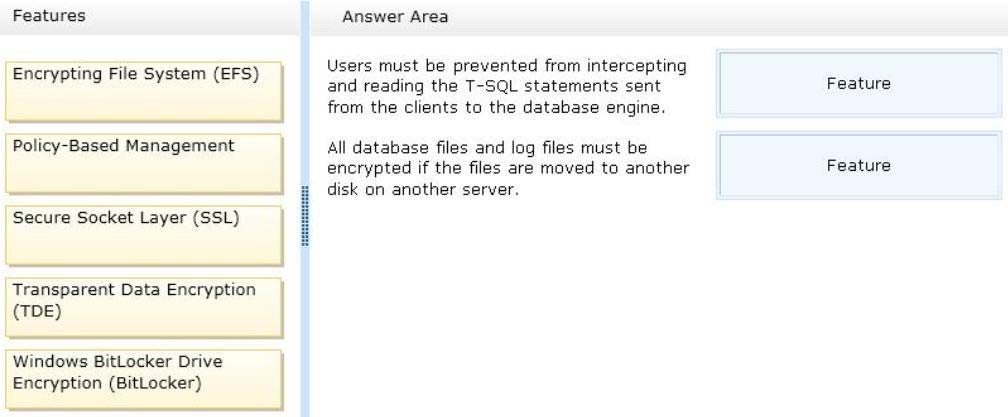
You identify the following security requirements for the deployment:
✑ Users must be prevented from intercepting and reading the T-SQL statements sent from the clients to the database engine.
✑ All database files and log files must be encrypted if the files are moved to another disk on another server.
You need to identify which feature meets each security requirement. The solution must minimize processor overhead.
Which features should you identify?
To answer, drag the appropriate feature to the correct requirement in the answer area.
Select and Place:
You plan to deploy SQL Server 2014.
You identify the following security requirements for the deployment:
✑ Users must be prevented from intercepting and reading the T-SQL statements sent from the clients to the database engine.
✑ All database files and log files must be encrypted if the files are moved to another disk on another server.
You need to identify which feature meets each security requirement. The solution must minimize processor overhead.
Which features should you identify?
To answer, drag the appropriate feature to the correct requirement in the answer area.
Select and Place:

Correct Answer:
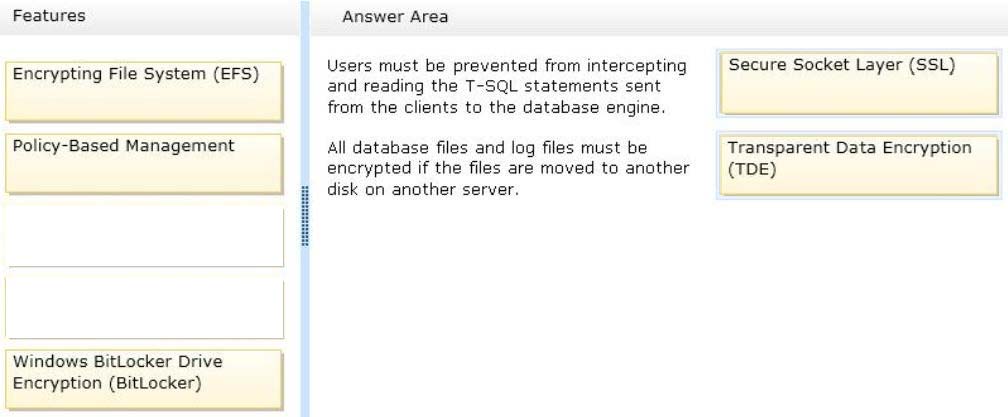
* Secure Sockets Layer (SSL) encryption enables transmitting encrypted data across the network between an instance of SQL Server and a client application.
* Transparent data encryption (TDE) performs real-time I/O encryption and decryption of the data and log files.
References:
Authentication in Reporting Services
Transparent Data Encryption (TDE)

* Secure Sockets Layer (SSL) encryption enables transmitting encrypted data across the network between an instance of SQL Server and a client application.
* Transparent data encryption (TDE) performs real-time I/O encryption and decryption of the data and log files.
References:
Authentication in Reporting Services
Transparent Data Encryption (TDE)
send
light_mode
delete
All Pages
