Microsoft 70-346 Exam Practice Questions (P. 4)
- Full Access (282 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
HOTSPOT -
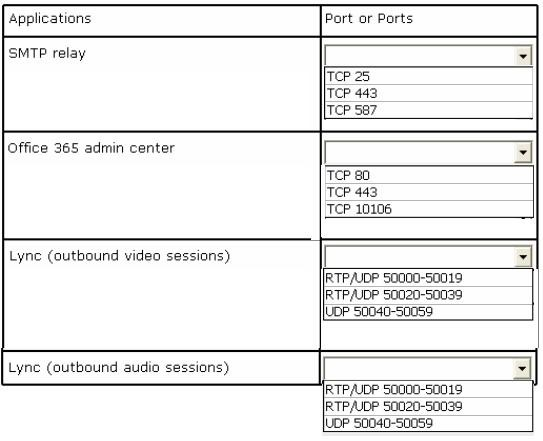
A company plans to deploy an Office 365 tenant.
You have the following requirements:
✑ Administrators must be able to access the Office 365 admin center.
✑ Microsoft Exchange Online must be used as a Simple Mail Transfer Protocol (SMTP) relay for a line-of-business application that sends email messages to remote domains.
All users must be able to use the audio and video capabilities in Microsoft Skype for Business.

You need to configure the ports for the firewall.
Which port should you use for each application? Select the correct answer from each list in the answer area.
Hot Area:
A company plans to deploy an Office 365 tenant.
You have the following requirements:
✑ Administrators must be able to access the Office 365 admin center.
✑ Microsoft Exchange Online must be used as a Simple Mail Transfer Protocol (SMTP) relay for a line-of-business application that sends email messages to remote domains.
All users must be able to use the audio and video capabilities in Microsoft Skype for Business.

You need to configure the ports for the firewall.
Which port should you use for each application? Select the correct answer from each list in the answer area.
Hot Area:

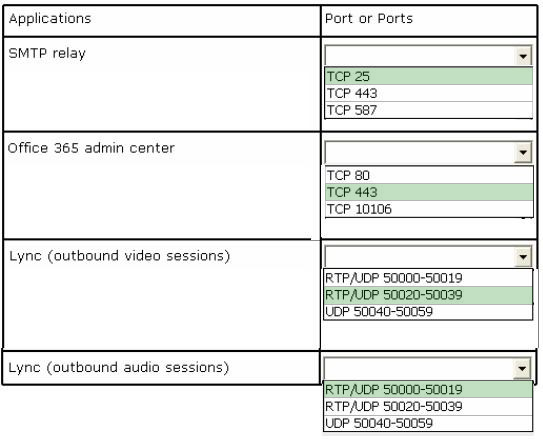
Correct Answer:
Transport Control Protocol(TCP), User Datagram Protocol (UDP) ports, and Protocol Numbers are important to TCP/IP networking, intranets, and the Internet.
Ports and protocol numbers provide access to a host computer. However, they also create a security hazard by allowing uninvited access. Therefore, knowing which port to allow or disable increases a network's security. If the wrong ports or protocol numbers are disabled on a firewall, router, or proxy server as a security measure, essential services might become unavailable.
TCP port 25 is used for simple mail transfer protocol which is used to e-mail routing between mail servers.
TCP port 443 is used for Audio, video and application sharing sessions as well as data sharing sessions.
RTP/UDP port 50020-50039 must be used for outbound video sessions.
RTP/UDP port 50000-50019must be used for outbound audio sessions.

Transport Control Protocol(TCP), User Datagram Protocol (UDP) ports, and Protocol Numbers are important to TCP/IP networking, intranets, and the Internet.
Ports and protocol numbers provide access to a host computer. However, they also create a security hazard by allowing uninvited access. Therefore, knowing which port to allow or disable increases a network's security. If the wrong ports or protocol numbers are disabled on a firewall, router, or proxy server as a security measure, essential services might become unavailable.
TCP port 25 is used for simple mail transfer protocol which is used to e-mail routing between mail servers.
TCP port 443 is used for Audio, video and application sharing sessions as well as data sharing sessions.
RTP/UDP port 50020-50039 must be used for outbound video sessions.
RTP/UDP port 50000-50019must be used for outbound audio sessions.
send
light_mode
delete
Question #17
Your company has a subscription to Office 365 for midsize business and enterprises. The company uses Microsoft Skype for Business Online.
You need to open ports on the network firewall to enable all of the features of Skype for Business Online.
Which port or ports should you open? (Each correct answer presents part of the solution. Choose all that apply.)
You need to open ports on the network firewall to enable all of the features of Skype for Business Online.
Which port or ports should you open? (Each correct answer presents part of the solution. Choose all that apply.)
- Ainbound TCP443
- Boutbound TCP 5061
- Coutbound UDP 3478
- Doutbound TCP 443
- Eoutbound UDP 50000 to outbound UDP 59999
- Finbound TCP 8080
Correct Answer:
ACDE
A: inbound TCP 443 is the port for the Skype for Business for Business client service.
C: outbound UDP 3478 is the UDP port for Skype for Business audio and video sessions.
D: outbound TCP 443 is the port for the Skype for Business data sharing sessions as well as the Video and Audio and application sharing sessions.
E: outbound UDP 50000 to outbound UDP 59999 is the port for Skype for Business audio and video sessions.
References:
https://adam-hand.com/cloud-technologies/firewall-ports-for-office-365/
ACDE
A: inbound TCP 443 is the port for the Skype for Business for Business client service.
C: outbound UDP 3478 is the UDP port for Skype for Business audio and video sessions.
D: outbound TCP 443 is the port for the Skype for Business data sharing sessions as well as the Video and Audio and application sharing sessions.
E: outbound UDP 50000 to outbound UDP 59999 is the port for Skype for Business audio and video sessions.
References:
https://adam-hand.com/cloud-technologies/firewall-ports-for-office-365/
send
light_mode
delete
Question #18
An organization plans to migrate to Office 365.
You need to estimate the post-migration network traffic.
Which tool should you use?
You need to estimate the post-migration network traffic.
Which tool should you use?
- AMicrosoft Online Services Diagnostics and Logging (MOSDAL) Support Kit
- BMicrosoft Network Monitor
- CSkype for Business Bandwidth Calculator
- DMicrosoft Remote Connectivity Analyzer
Correct Answer:
C
There are calculators available to assist you with estimating network bandwidth requirements. These calculators work for on-premises as well as Office 365 deployments. You can use the Exchange client network bandwidth calculator to estimate the bandwidth required for a specific set of Outlook, Outlook Web App, and mobile device users in your Office 365 deployment. With the Skype for Business bandwidth calculator, you enter information about users and the Skype for
Business features you want to deploy, and the calculator helps you determine bandwidth requirements.
Skype for Business Bandwidth Calculator - A Microsoft Excel spreadsheet that calculates WAN bandwidth requirements for a Skype for Business Server deployment based on administrator-specified user profiles and network information.
C
There are calculators available to assist you with estimating network bandwidth requirements. These calculators work for on-premises as well as Office 365 deployments. You can use the Exchange client network bandwidth calculator to estimate the bandwidth required for a specific set of Outlook, Outlook Web App, and mobile device users in your Office 365 deployment. With the Skype for Business bandwidth calculator, you enter information about users and the Skype for
Business features you want to deploy, and the calculator helps you determine bandwidth requirements.
Skype for Business Bandwidth Calculator - A Microsoft Excel spreadsheet that calculates WAN bandwidth requirements for a Skype for Business Server deployment based on administrator-specified user profiles and network information.
send
light_mode
delete
Question #19
DRAG DROP -
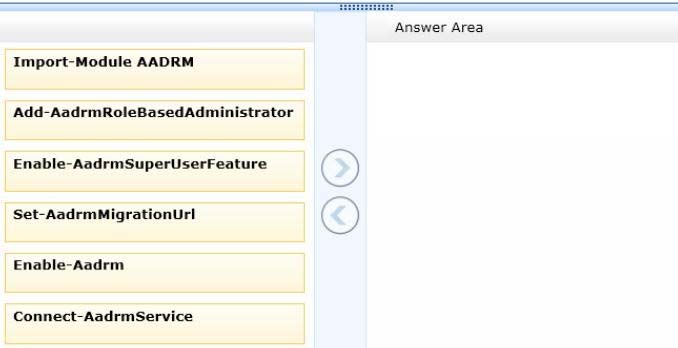
You are the Office 365 administrator for your company.
You need to ensure that trusted applications can decrypt rights-protected content.
Which four Windows PowerShell cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
Select and Place:
You are the Office 365 administrator for your company.
You need to ensure that trusted applications can decrypt rights-protected content.
Which four Windows PowerShell cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
Microsoft Azure Rights Management (previously known as Windows Azure Active Directory Rights Management). To be able to decrypt rights protected documents you need to make sure that Microsoft Azure Rights Management is set up. Also you will need to enable a SuperUser account because The Active
Directory Rights Management Services (AD RMS) super users group is a special group that has full control over all rights-protected content managed by the cluster. Its members are granted full owner rights in all use licenses that are issued by the AD RMS cluster on which the super users group is configured. This means that members of this group can decrypt any rights-protected content file and remove rights-protection from it.
The super users group is not enabled and is not assigned a group by default.
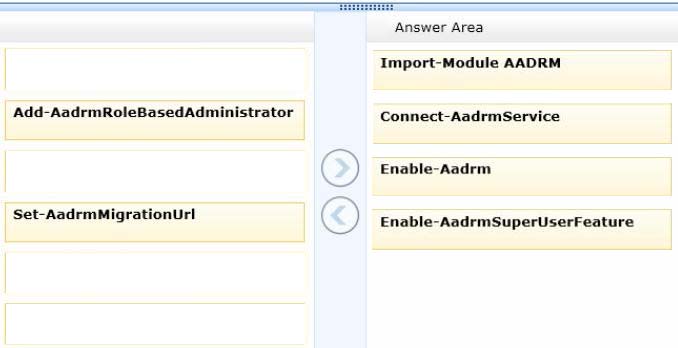
This can be done by running the appropriate commands in sequence which are:
1. Import-Module AADRM
2. Connect-AADRMService
3. Enable-AADRM
4. Enable-AADRMSuperUserFeature
References:
https://technet.microsoft.com/en-us/library/dn569291.aspx
https://technet.microsoft.com/en-us/library/dn151475%28v=exchg.150%29.aspx

Microsoft Azure Rights Management (previously known as Windows Azure Active Directory Rights Management). To be able to decrypt rights protected documents you need to make sure that Microsoft Azure Rights Management is set up. Also you will need to enable a SuperUser account because The Active
Directory Rights Management Services (AD RMS) super users group is a special group that has full control over all rights-protected content managed by the cluster. Its members are granted full owner rights in all use licenses that are issued by the AD RMS cluster on which the super users group is configured. This means that members of this group can decrypt any rights-protected content file and remove rights-protection from it.
The super users group is not enabled and is not assigned a group by default.
This can be done by running the appropriate commands in sequence which are:
1. Import-Module AADRM
2. Connect-AADRMService
3. Enable-AADRM
4. Enable-AADRMSuperUserFeature
References:
https://technet.microsoft.com/en-us/library/dn569291.aspx
https://technet.microsoft.com/en-us/library/dn151475%28v=exchg.150%29.aspx
send
light_mode
delete
Question #20
Your company has an Office 365 subscription. You create a new retention policy that contains several retention tags. A user named Test5 has a client computer that runs Microsoft Office Outlook 2007. You install Microsoft Outlook 2010 on the client computer of Test5. Test5 reports that the new retention tags are unavailable from Outlook 2010.
You verify that other users can use the new retention tags. You need to ensure that the new retention tags are available to Test5 from Outlook 2010.
What should you do?
You verify that other users can use the new retention tags. You need to ensure that the new retention tags are available to Test5 from Outlook 2010.
What should you do?
- AInstruct Test5 to repair the Outlook profile.
- BModify the retention policy tags.
- CRun the Set-Mailbox cmdlet.
- DForce directory synchronization.
Correct Answer:
A
When deploying retention policies it is part of the procedure to create the tags and add it to the retention policies prior to the deployment. Also part of the procedure is to determine which Microsoft Outlook client versions are in use. In this case the Test5version has been changed and Test5 will then have to repair his/her Outlook profile accordingly.
A
When deploying retention policies it is part of the procedure to create the tags and add it to the retention policies prior to the deployment. Also part of the procedure is to determine which Microsoft Outlook client versions are in use. In this case the Test5version has been changed and Test5 will then have to repair his/her Outlook profile accordingly.
send
light_mode
delete
All Pages
