Juniper JN0-696 Exam Practice Questions (P. 5)
- Full Access (71 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
-- Exhibit ""
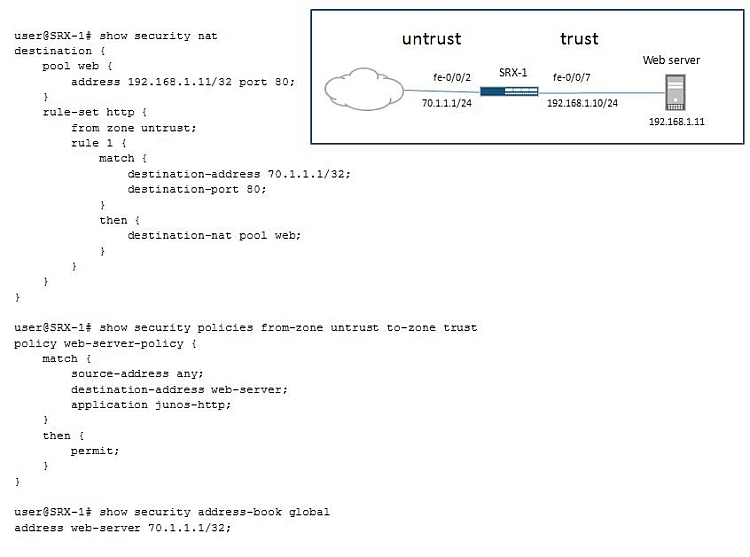
-- Exhibit --
Click the Exhibit button.
Your company has a Web server in the trust zone. You configure a NAT rule to allow Internet users from the untrust zone to access this Web server. Internet users use the public IP address 70.1.1.1 to access this Web server, but they report that the server is not accessible.
Referring to the exhibit, which configuration change would resolve this problem?

-- Exhibit --
Click the Exhibit button.
Your company has a Web server in the trust zone. You configure a NAT rule to allow Internet users from the untrust zone to access this Web server. Internet users use the public IP address 70.1.1.1 to access this Web server, but they report that the server is not accessible.
Referring to the exhibit, which configuration change would resolve this problem?
- Aset security nat proxy-arp interface fe-0/0/2 address 70.1.1.0/24
- Bset security zones security-zone untrust host-inbound-traffic system-services http
- Cset security nat destination rule-set http rule 1 match source-address 0.0.0.0/0
- Dset security address-book global address web-server 192.168.1.11/32
Correct Answer:
D
DNAT is first, followed by Policy look-up.
D
DNAT is first, followed by Policy look-up.
send
light_mode
delete
Question #22
-- Exhibit --
user@host> show log flow.log
Jun 12 20:00:45 host clear-log[ ]: logfile cleared
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:172.23.1.20/2526->10.3.202.56/443;6> matched filter to_https:
...
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: fe-0/0/6.0:172.23.1.20/2526->10.3.202.56/443, tcp, flag 2 syn
...
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:check self-traffic on fe-0/0/6.0, in_tunnel 0x0
...
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_first_rule_dst_xlate: DST xlate: 10.3.202.56(443) to 10.25.0.3(443), rule/pool id 2/2.
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_first_routing: vr_id 0, call flow_route_lookup(): src_ip 172.23.1.20, x_dst_ip 10.25.0.3, in ifp fe-0/0/6.0, out ifp N/A sp 2526, dp 443, ip_proto 6, tos 0
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:Doing DESTINATION addr route-lookup
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: routed (x_dst_ip 10.25.0.3) from managed (fe-0/0/6.0 in 0) to ge-0/0/1.4093, Next-hop: 10.25.0.3
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_first_policy_search: policy search from zone managed-> zone trust (0x110,0x9de01bb,0x1bb)
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: app 58, timeout 1800s, curr ageout 20s
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: permitted by policy default-policy-00(2)
...
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_xlate_pak
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: post addr xlation: 172.23.1.20->10.25.0.3.
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: post addr xlation: 172.23.1.20->10.25.0.3.
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:skip pre-frag: is_tunnel_if- 0, is_if_mtu_configured- 0
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:mbuf 0x42344180, exit nh 0xb00010
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: ----- flow_process_pkt rc 0x0 (fp rc 0)
-- Exhibit --
Click the Exhibit button.
You want to allow Web-based management of your SRX Series device through fe-0/0/6.0. This interface belongs to the managed zone with an IP address of
10.3.202.56. You are unable to open an HTTPS connection and have enabled traceoptions to troubleshoot the problem.
Referring to the exhibit, what is causing this problem?
user@host> show log flow.log
Jun 12 20:00:45 host clear-log[ ]: logfile cleared
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:172.23.1.20/2526->10.3.202.56/443;6> matched filter to_https:
...
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: fe-0/0/6.0:172.23.1.20/2526->10.3.202.56/443, tcp, flag 2 syn
...
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:check self-traffic on fe-0/0/6.0, in_tunnel 0x0
...
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_first_rule_dst_xlate: DST xlate: 10.3.202.56(443) to 10.25.0.3(443), rule/pool id 2/2.
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_first_routing: vr_id 0, call flow_route_lookup(): src_ip 172.23.1.20, x_dst_ip 10.25.0.3, in ifp fe-0/0/6.0, out ifp N/A sp 2526, dp 443, ip_proto 6, tos 0
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:Doing DESTINATION addr route-lookup
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: routed (x_dst_ip 10.25.0.3) from managed (fe-0/0/6.0 in 0) to ge-0/0/1.4093, Next-hop: 10.25.0.3
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_first_policy_search: policy search from zone managed-> zone trust (0x110,0x9de01bb,0x1bb)
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: app 58, timeout 1800s, curr ageout 20s
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: permitted by policy default-policy-00(2)
...
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_xlate_pak
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: post addr xlation: 172.23.1.20->10.25.0.3.
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: post addr xlation: 172.23.1.20->10.25.0.3.
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:skip pre-frag: is_tunnel_if- 0, is_if_mtu_configured- 0
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:mbuf 0x42344180, exit nh 0xb00010
Jun 12 20:01:10 20:01:10.412643:CID-0:RT: ----- flow_process_pkt rc 0x0 (fp rc 0)
-- Exhibit --
Click the Exhibit button.
You want to allow Web-based management of your SRX Series device through fe-0/0/6.0. This interface belongs to the managed zone with an IP address of
10.3.202.56. You are unable to open an HTTPS connection and have enabled traceoptions to troubleshoot the problem.
Referring to the exhibit, what is causing this problem?
- AThe HTTPS protocol is not enabled in the managed zone.
- BThe HTTPS protocol is not enabled in the trust zone.
- CThe lo0 interface is not configured in the managed zone.
- DThe packet was diverted to the wrong zone.
Correct Answer:
D
See:
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_first_policy_search: policy search from zone managed-> zone trust (0x110,0x9de01bb,0x1bb)
D
See:
Jun 12 20:01:10 20:01:10.412643:CID-0:RT:flow_first_policy_search: policy search from zone managed-> zone trust (0x110,0x9de01bb,0x1bb)
send
light_mode
delete
Question #23
-- Exhibit --
user@R1> show security ike security-associations
user@R1> show security zones
Security zone: trust -
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes -
Interfaces bounD. 3 -
Interfaces:
ge-0/0/0.0
ge-0/0/6.0
lo0.0
Security zone: untrust -
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes -
Interfaces bounD. 1 -
Interfaces:
ge-0/0/1.0
Security zone: junos-host -
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes -
Interfaces bounD. 0 -
Interfaces:
user@R1> show interfaces st0
Physical interface: st0, Enabled, Physical link is Up
Interface index: 130, SNMP ifIndex: 503
Type: Secure-Tunnel, Link-level type: Secure-Tunnel, MTU: 9192
Device flags : Present Running
Interface flags: Point-To-Point -
Input rate : 0 bps (0 pps)
Output rate : 0 bps (0 pps)
Logical interface st0.0 (Index 72) (SNMP ifIndex 546)
Flags: Link-Layer-Down Point-To-Point SNMP-Traps
Encapsulation: Secure-Tunnel -
Input packets : 3 -
Output packets: 3 -
Security: Zone: Null -
Protocol inet, MTU: 9192 -
Flags: Sendbcast-pkt-to-re -
Addresses, Flags: Dest-route-down Is-Preferred Is-Primary
Destination: 172.19.0.0/30, Local: 172.19.0.1
user@R1> show interfaces ge-0/0/1
Physical interface: ge-0/0/1, Enabled, Physical link is Up
Interface index: 135, SNMP ifIndex: 508
Link-level type: Ethernet, MTU: 1514, Link-mode: Full-duplex, SpeeD. 1000mbps,
BPDU Error: None, MAC-REWRITE Error: None, Loopback: Disabled,
Source filtering: Disabled, Flow control: Enabled, Auto-negotiation: Enabled,
Remote fault: Online -
Device flags : Present Running
Interface flags: SNMP-Traps Internal: 0x0
Link flags : None -
CoS queues : 8 supported, 8 maximum usable queues
Current address: b0:c6:9a:73:27:81, Hardware address: b0:c6:9a:73:27:81
Last flapped : 2013-06-12 15:22:48 UTC (00:59:41 ago)
Input rate : 0 bps (0 pps)
Output rate : 0 bps (0 pps)
Active alarms : None -
Active defects : None -
Interface transmit statistics: Disabled
Logical interface ge-0/0/1.0 (Index 71) (SNMP ifIndex 541)
Flags: SNMP-Traps 0x0 Encapsulation: ENET2
Input packets : 40 -
Output packets: 27 -
Security: Zone: untrust -
Allowed host-inbound traffic : ping
Protocol inet, MTU: 1500 -
Flags: Sendbcast-pkt-to-re -
Addresses, Flags: Is-Preferred Is-Primary
Destination: 184.0.15.0/30, Local: 184.0.15.1, Broadcast: 184.0.15.3 user@R1> show log ipsec-trace | match "500|drop"
Jun 12 16:32:10 16:32:10.680034:CID-0:RT:ageout 71,184.0.15.2/500->184.0.15.1/500,17, (0/0)
Jun 12 16:32:51 16:32:51.874191:CID-0:RT:184.0.15.2/500->184.0.15.1/500;17> :
Jun 12 16:32:51 16:32:51.874191:CID-0:RT: ge-0/0/1.0:184.0.15.2/500->184.0.15.1/500, udp
Jun 12 16:32:51 16:32:51.874191:CID-0:RT: find flow: table 0x4f160b38, hash 8769(0xffff), sa 184.0.15.2, da 184.0.15.1, sp 500, dp 500, proto 17, tok 8
Jun 12 16:32:51 16:32:51.874191:CID-0:RT:pak_for_self : proto 17, dst port 500, action 0x0
Jun 12 16:32:51 16:32:51.874191:CID-0:RT: flow_first_in_dst_nat: in 0/1.0>, out A> dst_adr 184.0.15.1, sp 500, dp 500
Jun 12 16:32:51 16:32:51.874555:CID-0:RT: packet droppeD. for self but not interested
Jun 12 16:32:51 16:32:51.874555:CID-0:RT: packet dropped, packet droppeD. for self but not interested.
Jun 12 16:32:54 16:32:54.680399:CID-0:RT:ageout 71,184.0.15.2/500->184.0.15.1/500,17, (0/0)
Jun 12 16:32:56 16:32:56.888094:CID-0:RT:184.0.15.2/500->184.0.15.1/500;17> :
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: ge-0/0/1.0:184.0.15.2/500->184.0.15.1/500, udp
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: find flow: table 0x4f160b38, hash 8769(0xffff), sa 184.0.15.2, da 184.0.15.1, sp 500, dp 500, proto 17, tok 8
Jun 12 16:32:56 16:32:56.888094:CID-0:RT:pak_for_self : proto 17, dst port 500, action 0x0
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: flow_first_in_dst_nat: in 0/1.0>, out A> dst_adr 184.0.15.1, sp 500, dp 500
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: packet droppeD. for self but not interested
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: packet dropped, packet droppeD. for self but not interested.
Jun 12 16:33:00 16:33:00.680794:CID-0:RT:ageout 71,184.0.15.2/500->184.0.15.1/500,17, (0/0)
Jun 12 16:33:07 16:33:06.902220:CID-0:RT:184.0.15.2/500->184.0.15.1/500;17> :
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: ge-0/0/1.0:184.0.15.2/500->184.0.15.1/500, udp
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: find flow: table 0x4f160b38, hash 8769(0xffff), sa 184.0.15.2, da 184.0.15.1, sp 500, dp 500, proto 17, tok 8
Jun 12 16:33:07 16:33:06.902220:CID-0:RT:pak_for_self : proto 17, dst port 500, action 0x0
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: flow_first_in_dst_nat: in 0/1.0>, out A> dst_adr 184.0.15.1, sp 500, dp 500
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: packet droppeD. for self but not interested
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: packet dropped, packet droppeD. for self but not interested.
-- Exhibit --
Click the Exhibit button.
You are asked to troubleshoot a new IPsec tunnel that is not establishing between R1 and R2. The remote team has verified that R2's configuration is correct.
Referring to the exhibit, which two actions are required to resolve the problem? (Choose two.)
user@R1> show security ike security-associations
user@R1> show security zones
Security zone: trust -
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes -
Interfaces bounD. 3 -
Interfaces:
ge-0/0/0.0
ge-0/0/6.0
lo0.0
Security zone: untrust -
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes -
Interfaces bounD. 1 -
Interfaces:
ge-0/0/1.0
Security zone: junos-host -
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes -
Interfaces bounD. 0 -
Interfaces:
user@R1> show interfaces st0
Physical interface: st0, Enabled, Physical link is Up
Interface index: 130, SNMP ifIndex: 503
Type: Secure-Tunnel, Link-level type: Secure-Tunnel, MTU: 9192
Device flags : Present Running
Interface flags: Point-To-Point -
Input rate : 0 bps (0 pps)
Output rate : 0 bps (0 pps)
Logical interface st0.0 (Index 72) (SNMP ifIndex 546)
Flags: Link-Layer-Down Point-To-Point SNMP-Traps
Encapsulation: Secure-Tunnel -
Input packets : 3 -
Output packets: 3 -
Security: Zone: Null -
Protocol inet, MTU: 9192 -
Flags: Sendbcast-pkt-to-re -
Addresses, Flags: Dest-route-down Is-Preferred Is-Primary
Destination: 172.19.0.0/30, Local: 172.19.0.1
user@R1> show interfaces ge-0/0/1
Physical interface: ge-0/0/1, Enabled, Physical link is Up
Interface index: 135, SNMP ifIndex: 508
Link-level type: Ethernet, MTU: 1514, Link-mode: Full-duplex, SpeeD. 1000mbps,
BPDU Error: None, MAC-REWRITE Error: None, Loopback: Disabled,
Source filtering: Disabled, Flow control: Enabled, Auto-negotiation: Enabled,
Remote fault: Online -
Device flags : Present Running
Interface flags: SNMP-Traps Internal: 0x0
Link flags : None -
CoS queues : 8 supported, 8 maximum usable queues
Current address: b0:c6:9a:73:27:81, Hardware address: b0:c6:9a:73:27:81
Last flapped : 2013-06-12 15:22:48 UTC (00:59:41 ago)
Input rate : 0 bps (0 pps)
Output rate : 0 bps (0 pps)
Active alarms : None -
Active defects : None -
Interface transmit statistics: Disabled
Logical interface ge-0/0/1.0 (Index 71) (SNMP ifIndex 541)
Flags: SNMP-Traps 0x0 Encapsulation: ENET2
Input packets : 40 -
Output packets: 27 -
Security: Zone: untrust -
Allowed host-inbound traffic : ping
Protocol inet, MTU: 1500 -
Flags: Sendbcast-pkt-to-re -
Addresses, Flags: Is-Preferred Is-Primary
Destination: 184.0.15.0/30, Local: 184.0.15.1, Broadcast: 184.0.15.3 user@R1> show log ipsec-trace | match "500|drop"
Jun 12 16:32:10 16:32:10.680034:CID-0:RT:ageout 71,184.0.15.2/500->184.0.15.1/500,17, (0/0)
Jun 12 16:32:51 16:32:51.874191:CID-0:RT:184.0.15.2/500->184.0.15.1/500;17> :
Jun 12 16:32:51 16:32:51.874191:CID-0:RT: ge-0/0/1.0:184.0.15.2/500->184.0.15.1/500, udp
Jun 12 16:32:51 16:32:51.874191:CID-0:RT: find flow: table 0x4f160b38, hash 8769(0xffff), sa 184.0.15.2, da 184.0.15.1, sp 500, dp 500, proto 17, tok 8
Jun 12 16:32:51 16:32:51.874191:CID-0:RT:pak_for_self : proto 17, dst port 500, action 0x0
Jun 12 16:32:51 16:32:51.874191:CID-0:RT: flow_first_in_dst_nat: in 0/1.0>, out A> dst_adr 184.0.15.1, sp 500, dp 500
Jun 12 16:32:51 16:32:51.874555:CID-0:RT: packet droppeD. for self but not interested
Jun 12 16:32:51 16:32:51.874555:CID-0:RT: packet dropped, packet droppeD. for self but not interested.
Jun 12 16:32:54 16:32:54.680399:CID-0:RT:ageout 71,184.0.15.2/500->184.0.15.1/500,17, (0/0)
Jun 12 16:32:56 16:32:56.888094:CID-0:RT:184.0.15.2/500->184.0.15.1/500;17> :
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: ge-0/0/1.0:184.0.15.2/500->184.0.15.1/500, udp
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: find flow: table 0x4f160b38, hash 8769(0xffff), sa 184.0.15.2, da 184.0.15.1, sp 500, dp 500, proto 17, tok 8
Jun 12 16:32:56 16:32:56.888094:CID-0:RT:pak_for_self : proto 17, dst port 500, action 0x0
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: flow_first_in_dst_nat: in 0/1.0>, out A> dst_adr 184.0.15.1, sp 500, dp 500
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: packet droppeD. for self but not interested
Jun 12 16:32:56 16:32:56.888094:CID-0:RT: packet dropped, packet droppeD. for self but not interested.
Jun 12 16:33:00 16:33:00.680794:CID-0:RT:ageout 71,184.0.15.2/500->184.0.15.1/500,17, (0/0)
Jun 12 16:33:07 16:33:06.902220:CID-0:RT:184.0.15.2/500->184.0.15.1/500;17> :
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: ge-0/0/1.0:184.0.15.2/500->184.0.15.1/500, udp
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: find flow: table 0x4f160b38, hash 8769(0xffff), sa 184.0.15.2, da 184.0.15.1, sp 500, dp 500, proto 17, tok 8
Jun 12 16:33:07 16:33:06.902220:CID-0:RT:pak_for_self : proto 17, dst port 500, action 0x0
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: flow_first_in_dst_nat: in 0/1.0>, out A> dst_adr 184.0.15.1, sp 500, dp 500
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: packet droppeD. for self but not interested
Jun 12 16:33:07 16:33:06.902220:CID-0:RT: packet dropped, packet droppeD. for self but not interested.
-- Exhibit --
Click the Exhibit button.
You are asked to troubleshoot a new IPsec tunnel that is not establishing between R1 and R2. The remote team has verified that R2's configuration is correct.
Referring to the exhibit, which two actions are required to resolve the problem? (Choose two.)
- AAdd the st0.0 interface to a security zone.
- BChange the st0.0 interface MTU to 1400.
- CEnable IKE for host inbound traffic in the untrust zone.
- DEnable IKE for host inbound traffic in the trust zone.
Correct Answer:
AC
AC
send
light_mode
delete
Question #24
-- Exhibit --
user@R1> show log ike-trace
Jun 13 07:45:10 ikev2_packet_v1_start: Passing IKE v1.0 packet to IKEv1 library
Jun 13 07:45:10 ike_get_sA. Start, SA = { 7fd86fbe 8a99c1f6 - 00000000 00000000 } / 00000000, remote = 184.0.15.2:500
Jun 13 07:45:10 ike_sa_allocate: Start, SA = { 7fd86fbe 8a99c1f6 - a1bc3f1d e2a45308 }
Jun 13 07:45:10 ike_init_isakmp_sA. Start, remote = 184.0.15.2:500, initiator = 0
Jun 13 07:45:10 ike_decode_packet: Start
Jun 13 07:45:10 ike_decode_packet: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733} / 00000000, nego = -1
Jun 13 07:45:10 ike_decode_payload_sA. Start
Jun 13 07:45:10 ike_decode_payload_t: Start, # trans = 1
Jun 13 07:45:10 ike_decode_payload_t: Start, # trans = 1
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = afcad713 68a1f1c9 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 27bab5dc 01ea0760 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 6105c422 e76847e4 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 4485152d 18b6bbcd ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = cd604643 35df21f8 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 90cb8091 3ebb696e ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 7d9419a6 5310ca6f ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 4a131c81 07035845 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..28] = 69936922 8741c6d4 ...
Jun 13 07:45:10 ike_st_i_sa_proposal: Start
Jun 13 07:45:10 P1 SA payload match failed for sa-cfg to-R2. Abortingnegotiation for tunnel type 2 local:184.0.15.1 remote:184.0.15.2 IKEv1.
Jun 13 07:45:10 iked_pm_ike_spd_select_ike_sa failed. rc 1, error_code: No proposal chosen
Jun 13 07:45:10 ikev2_fb_spd_select_sa_cB. IKEv2 SA select failed with error No proposal chosen (neg a7e800)
Jun 13 07:45:10 ike_isakmp_sa_reply: Start
Jun 13 07:45:10 ike_state_restart_packet: Start, restart packet SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = -1
Jun 13 07:45:10 ike_st_i_sa_proposal: Start
Jun 13 07:45:10 ike_st_i_cr: Start
Jun 13 07:45:10 ike_st_i_cert: Start
Jun 13 07:45:10 ike_st_i_private: Start
Jun 13 07:45:10 ike_st_o_sa_values: Start
Jun 13 07:45:10 184.0.15.1:500 (Responder) -> 184.0.15.2:500 { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733 [-1] / 0x00000000 } IP; Error = No proposal chosen (14)
Jun 13 07:45:10 ike_alloc_negotiation: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}
Jun 13 07:45:10 ike_encode_packet: Start, SA = { 0x7fd86fbe 8a99c1f6 - b8f95b2e f92ca733 } / b20d590c, nego = 0
Jun 13 07:45:10 ike_send_packet: Start, send SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = 0, dst = 184.0.15.2:500, routing table id = 0
Jun 13 07:45:10 ike_delete_negotiation: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = 0
Jun 13 07:45:10 ike_free_negotiation_info: Start, nego = 0
Jun 13 07:45:10 ike_free_negotiation: Start, nego = 0
Jun 13 07:45:10 IKE negotiation fail for local:184.0.15.1, remote:184.0.15.2 IKEv1 with status: No proposal chosen
Jun 13 07:45:10 IKEv1 Error : No proposal chosen
Jun 13 07:45:40 P1 SA 3770105 timer expiry. ref cnt 1, timer reason Force delete timer expired (1), flags 0x330.
Jun 13 07:45:40 iked_pm_ike_sa_delete_done_cB. For p1 sa index 3770105, ref cnt 1, status: Error ok
Jun 13 07:45:40 ike_remove_callback: Start, delete SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = -1
Jun 13 07:45:40 ike_delete_negotiation: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = -1
Jun 13 07:45:40 ssh_ike_tunnel_table_entry_delete: Deleting tunnel_iD. 0 from IKE tunnel table
Jun 13 07:45:40 ssh_ike_tunnel_table_entry_delete: The tunnel iD. 0 doesn't exist in IKE tunnel table
Jun 13 07:45:40 ike_sa_delete: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733 }
Jun 13 07:45:40 ike_free_negotiation_isakmp: Start, nego = -1
Jun 13 07:45:40 ike_free_negotiation: Start, nego = -1
Jun 13 07:45:40 IKE SA delete called for p1 sa 3770105 (ref cnt 1) local:184.0.15.1, remote:184.0.15.2, IKEv1
Jun 13 07:45:40 iked_pm_p1_sa_destroy: p1 sa 3770105 (ref cnt 0), waiting_for_del 0x0
Jun 13 07:45:40 ike_free_sA. Start
-- Exhibit --
Click the Exhibit button.
You are asked to troubleshoot a new IPsec VPN between R1 and R2 that is not coming up. You have captured the traceoptions output shown in the exhibit.
What is the reason for the problem?
user@R1> show log ike-trace
Jun 13 07:45:10 ikev2_packet_v1_start: Passing IKE v1.0 packet to IKEv1 library
Jun 13 07:45:10 ike_get_sA. Start, SA = { 7fd86fbe 8a99c1f6 - 00000000 00000000 } / 00000000, remote = 184.0.15.2:500
Jun 13 07:45:10 ike_sa_allocate: Start, SA = { 7fd86fbe 8a99c1f6 - a1bc3f1d e2a45308 }
Jun 13 07:45:10 ike_init_isakmp_sA. Start, remote = 184.0.15.2:500, initiator = 0
Jun 13 07:45:10 ike_decode_packet: Start
Jun 13 07:45:10 ike_decode_packet: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733} / 00000000, nego = -1
Jun 13 07:45:10 ike_decode_payload_sA. Start
Jun 13 07:45:10 ike_decode_payload_t: Start, # trans = 1
Jun 13 07:45:10 ike_decode_payload_t: Start, # trans = 1
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = afcad713 68a1f1c9 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 27bab5dc 01ea0760 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 6105c422 e76847e4 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 4485152d 18b6bbcd ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = cd604643 35df21f8 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 90cb8091 3ebb696e ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 7d9419a6 5310ca6f ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..16] = 4a131c81 07035845 ...
Jun 13 07:45:10 ike_st_i_viD. VID[0..28] = 69936922 8741c6d4 ...
Jun 13 07:45:10 ike_st_i_sa_proposal: Start
Jun 13 07:45:10 P1 SA payload match failed for sa-cfg to-R2. Abortingnegotiation for tunnel type 2 local:184.0.15.1 remote:184.0.15.2 IKEv1.
Jun 13 07:45:10 iked_pm_ike_spd_select_ike_sa failed. rc 1, error_code: No proposal chosen
Jun 13 07:45:10 ikev2_fb_spd_select_sa_cB. IKEv2 SA select failed with error No proposal chosen (neg a7e800)
Jun 13 07:45:10 ike_isakmp_sa_reply: Start
Jun 13 07:45:10 ike_state_restart_packet: Start, restart packet SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = -1
Jun 13 07:45:10 ike_st_i_sa_proposal: Start
Jun 13 07:45:10 ike_st_i_cr: Start
Jun 13 07:45:10 ike_st_i_cert: Start
Jun 13 07:45:10 ike_st_i_private: Start
Jun 13 07:45:10 ike_st_o_sa_values: Start
Jun 13 07:45:10 184.0.15.1:500 (Responder) -> 184.0.15.2:500 { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733 [-1] / 0x00000000 } IP; Error = No proposal chosen (14)
Jun 13 07:45:10 ike_alloc_negotiation: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}
Jun 13 07:45:10 ike_encode_packet: Start, SA = { 0x7fd86fbe 8a99c1f6 - b8f95b2e f92ca733 } / b20d590c, nego = 0
Jun 13 07:45:10 ike_send_packet: Start, send SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = 0, dst = 184.0.15.2:500, routing table id = 0
Jun 13 07:45:10 ike_delete_negotiation: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = 0
Jun 13 07:45:10 ike_free_negotiation_info: Start, nego = 0
Jun 13 07:45:10 ike_free_negotiation: Start, nego = 0
Jun 13 07:45:10 IKE negotiation fail for local:184.0.15.1, remote:184.0.15.2 IKEv1 with status: No proposal chosen
Jun 13 07:45:10 IKEv1 Error : No proposal chosen
Jun 13 07:45:40 P1 SA 3770105 timer expiry. ref cnt 1, timer reason Force delete timer expired (1), flags 0x330.
Jun 13 07:45:40 iked_pm_ike_sa_delete_done_cB. For p1 sa index 3770105, ref cnt 1, status: Error ok
Jun 13 07:45:40 ike_remove_callback: Start, delete SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = -1
Jun 13 07:45:40 ike_delete_negotiation: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733}, nego = -1
Jun 13 07:45:40 ssh_ike_tunnel_table_entry_delete: Deleting tunnel_iD. 0 from IKE tunnel table
Jun 13 07:45:40 ssh_ike_tunnel_table_entry_delete: The tunnel iD. 0 doesn't exist in IKE tunnel table
Jun 13 07:45:40 ike_sa_delete: Start, SA = { 7fd86fbe 8a99c1f6 - b8f95b2e f92ca733 }
Jun 13 07:45:40 ike_free_negotiation_isakmp: Start, nego = -1
Jun 13 07:45:40 ike_free_negotiation: Start, nego = -1
Jun 13 07:45:40 IKE SA delete called for p1 sa 3770105 (ref cnt 1) local:184.0.15.1, remote:184.0.15.2, IKEv1
Jun 13 07:45:40 iked_pm_p1_sa_destroy: p1 sa 3770105 (ref cnt 0), waiting_for_del 0x0
Jun 13 07:45:40 ike_free_sA. Start
-- Exhibit --
Click the Exhibit button.
You are asked to troubleshoot a new IPsec VPN between R1 and R2 that is not coming up. You have captured the traceoptions output shown in the exhibit.
What is the reason for the problem?
- AIKE Phase 2 proposal mismatch
- BIKE preshared key mismatch
- CIKE Phase 1 proposal mismatch
- DIKE Phase 1 mode mismatch
Correct Answer:
C
C
send
light_mode
delete
Question #25
-- Exhibit --
user@SRX-1> show configuration security ike
traceoptions {
file ike-trace;
flag all;
}
policy juniper {
proposal-set standard;
pre-shared-key ascii-text "$ $ znCO hKMXtuMX - gTz "; ## SECRET-DATA
}
gateway juniper {
ike-policy juniper;
address 192.168.1.11;
external-interface fe-0/0/7;
}
user@SRX-1> show configuration security ipsec
traceoptions {
flag all;
}
policy juniper {
proposal-set standard;
}
vpn juniper {
bind-interface st0.0;
ike {
gateway juniper;
ipsec-policy juniper;
}
}
user@SRX-1> show security ike security-associations
user@SRX-1> show security ipsec security-associations
Total active tunnels: 0 -
user@SRX-1> show log ike-trace
...
Jun 13 16:21:33 ike_st_o_all_done: MESSAGE: Phase 1 { 0x3f669946 90eba0c7 - 0x76bdffab f8770040 } / 00000000, version = 1.0, xchg = Identity protect, auth_method = Pre shared keys, Responder, cipher = 3des-cbc, hash = sha1, prf = hmac-sha1, life = 0 kB / 28800 sec, key l
Jun 13 16:21:33 192.168.1.10:500 (Responder) -> 192.168.1.11:500 { 3f669946 90eba0c7 - 76bdffab f8770040 [-1] / 0x00000000 } IP; MESSAGE: Phase 1 version = 1.0, auth_method = Pre shared keys, cipher = 3des-cbc, hash = sha1, prf = hmac-sha1, life = 0 kB / 28800 sec, key
Jun 13 16:21:33 ike_encode_packet: Start, SA = { 0x3f669946 90eba0c7 - 76bdffab f8770040 } / 00000000, nego = -1
Jun 13 16:21:33 ike_send_packet: Start, send SA = { 3f669946 90eba0c7 - 76bdffab f8770040}, nego = -1, dst = 192.168.1.11:500, routing table id = 0
Jun 13 16:21:33 ike_send_notify: Connected, SA = { 3f669946 90eba0c7 - 76bdffab f8770040}, nego = -1
Jun 13 16:21:33 iked_pm_ike_sa_done: local:192.168.1.10, remote:192.168.1.11 IKEv1
Jun 13 16:21:33 iked_pm_id_validate id NOT matched.
Jun 13 16:21:33 P1 SA 3075313 timer expiry. ref cnt 1, timer reason Defer delete timer expired (3), flags 0x331.
Jun 13 16:21:33 iked_pm_ike_sa_delete_notify_done_cB. For p1 sa index 3075313, ref cnt 1, status: Error ok
Jun 13 16:21:33 ike_expire_callback: Start, expire SA = { 3f669946 90eba0c7 - 76bdffab f8770040}, nego = -1
Jun 13 16:21:33 ike_alloc_negotiation: Start, SA = { 3f669946 90eba0c7 - 76bdffab f8770040}
...
-- Exhibit --
Click the Exhibit button.
You are troubleshooting a new IPsec VPN that is not establishing between SRX-1 and a remote end device.
Referring to the exhibit, what is causing the problem?
user@SRX-1> show configuration security ike
traceoptions {
file ike-trace;
flag all;
}
policy juniper {
proposal-set standard;
pre-shared-key ascii-text "$ $ znCO hKMXtuMX - gTz "; ## SECRET-DATA
}
gateway juniper {
ike-policy juniper;
address 192.168.1.11;
external-interface fe-0/0/7;
}
user@SRX-1> show configuration security ipsec
traceoptions {
flag all;
}
policy juniper {
proposal-set standard;
}
vpn juniper {
bind-interface st0.0;
ike {
gateway juniper;
ipsec-policy juniper;
}
}
user@SRX-1> show security ike security-associations
user@SRX-1> show security ipsec security-associations
Total active tunnels: 0 -
user@SRX-1> show log ike-trace
...
Jun 13 16:21:33 ike_st_o_all_done: MESSAGE: Phase 1 { 0x3f669946 90eba0c7 - 0x76bdffab f8770040 } / 00000000, version = 1.0, xchg = Identity protect, auth_method = Pre shared keys, Responder, cipher = 3des-cbc, hash = sha1, prf = hmac-sha1, life = 0 kB / 28800 sec, key l
Jun 13 16:21:33 192.168.1.10:500 (Responder) -> 192.168.1.11:500 { 3f669946 90eba0c7 - 76bdffab f8770040 [-1] / 0x00000000 } IP; MESSAGE: Phase 1 version = 1.0, auth_method = Pre shared keys, cipher = 3des-cbc, hash = sha1, prf = hmac-sha1, life = 0 kB / 28800 sec, key
Jun 13 16:21:33 ike_encode_packet: Start, SA = { 0x3f669946 90eba0c7 - 76bdffab f8770040 } / 00000000, nego = -1
Jun 13 16:21:33 ike_send_packet: Start, send SA = { 3f669946 90eba0c7 - 76bdffab f8770040}, nego = -1, dst = 192.168.1.11:500, routing table id = 0
Jun 13 16:21:33 ike_send_notify: Connected, SA = { 3f669946 90eba0c7 - 76bdffab f8770040}, nego = -1
Jun 13 16:21:33 iked_pm_ike_sa_done: local:192.168.1.10, remote:192.168.1.11 IKEv1
Jun 13 16:21:33 iked_pm_id_validate id NOT matched.
Jun 13 16:21:33 P1 SA 3075313 timer expiry. ref cnt 1, timer reason Defer delete timer expired (3), flags 0x331.
Jun 13 16:21:33 iked_pm_ike_sa_delete_notify_done_cB. For p1 sa index 3075313, ref cnt 1, status: Error ok
Jun 13 16:21:33 ike_expire_callback: Start, expire SA = { 3f669946 90eba0c7 - 76bdffab f8770040}, nego = -1
Jun 13 16:21:33 ike_alloc_negotiation: Start, SA = { 3f669946 90eba0c7 - 76bdffab f8770040}
...
-- Exhibit --
Click the Exhibit button.
You are troubleshooting a new IPsec VPN that is not establishing between SRX-1 and a remote end device.
Referring to the exhibit, what is causing the problem?
- APre-shared key mismatch
- BIKE Phase 1 proposals mismatch
- CIKE Phase 1 IKE ID mismatch
- DIKE Phase 2 proxy ID mismatch
Correct Answer:
C
See line:
Jun 13 16:21:33 iked_pm_id_validate id NOT matched.
C
See line:
Jun 13 16:21:33 iked_pm_id_validate id NOT matched.
send
light_mode
delete
All Pages
