Juniper JN0-696 Exam Practice Questions (P. 3)
- Full Access (71 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
You recently configured the antivirus feature profile on your Junos device. The security policy is sending traffic for antivirus scanning. However, the traffic is being blocked and you repeatedly receive the system log message that the scan engine is not ready. You must not allow the traffic to be dropped when the scan engine is not ready.
Which action will resolve this problem?
Which action will resolve this problem?
- AConfigure antivirus trickling to prevent the scan engine from timing out.
- BConfigure an antivirus file scanning extension list to reduce the number of files for scanning.
- CConfigure an antivirus fallback option to permit the traffic when the scan engine is not ready.
- DConfigure an antivirus content size limit to minimize the scanning of large files.
Correct Answer:
C
Configure a fallback so that no traffic gets dropped when you are scanning a lot or big files for instance.
The size of the files that can be scanned can also be configured.
References:
http://www.juniper.net/documentation/en_US/junos12.1/topics/reference/configuration-statement/security-edit-engine-not-ready-sophos-engine.html
C
Configure a fallback so that no traffic gets dropped when you are scanning a lot or big files for instance.
The size of the files that can be scanned can also be configured.
References:
http://www.juniper.net/documentation/en_US/junos12.1/topics/reference/configuration-statement/security-edit-engine-not-ready-sophos-engine.html
send
light_mode
delete
Question #12
You are troubleshooting a problem on your Junos device where the antispam SBL server is no longer filtering known spam hosts. You notice that local list antispam filtering is still working for known spam hosts.
What would cause this problem?
What would cause this problem?
- AYou have configured the sbl-default-server parameter in the antispam feature profile.
- BDNS has stopped working on your Junos device.
- CThe antispam license has expired on your Junos device.
- DThe default spam-action parameter has been set to permit.
Correct Answer:
C
When it stops working remotely but still works locally it is normally due to the license expiring unless something else has changed in your configuration.
References:
http://www.juniper.net/documentation/en_US/junos12.1/topics/concept/utm-antispam-filter-server-based-understanding.html
C
When it stops working remotely but still works locally it is normally due to the license expiring unless something else has changed in your configuration.
References:
http://www.juniper.net/documentation/en_US/junos12.1/topics/concept/utm-antispam-filter-server-based-understanding.html
send
light_mode
delete
Question #13
In preparation for future expansion, a user decides to configure a stand-alone SRX Series device for chassis-clustering mode. The user enters the command set chassis cluster cluster-id 0 node 0 reboot on the device. After the device reboots, the user sees this output: user@host> show chassis cluster status error: Chassis cluster is not enabled. user@host>
The device does not enter chassis-clustering mode.
What is the problem?
The device does not enter chassis-clustering mode.
What is the problem?
- AAn SRX Series device will not enter chassis-clustering mode unless the fxp0 and fxp1 interfaces are defined in the configuration.
- BAn SRX Series device will only enter chassis-clustering mode when it finds a peer that is also configured for chassis-clustering mode.
- CCluster ID 0 is not valid for a chassis cluster.
- DNode ID 0 is not valid for a chassis cluster.
Correct Answer:
C
Cluster-id numbering can range from 1-15. Configuring a cluster-id of 0 is equivalent to disabling chassis cluster.
References:
https://www.juniper.net/documentation/en_US/junos12.3×48/topics/reference/command-summary/set-chassis-cluster-clusterid-node-reboot.html
C
Cluster-id numbering can range from 1-15. Configuring a cluster-id of 0 is equivalent to disabling chassis cluster.
References:
https://www.juniper.net/documentation/en_US/junos12.3×48/topics/reference/command-summary/set-chassis-cluster-clusterid-node-reboot.html
send
light_mode
delete
Question #14
-- Exhibit ""
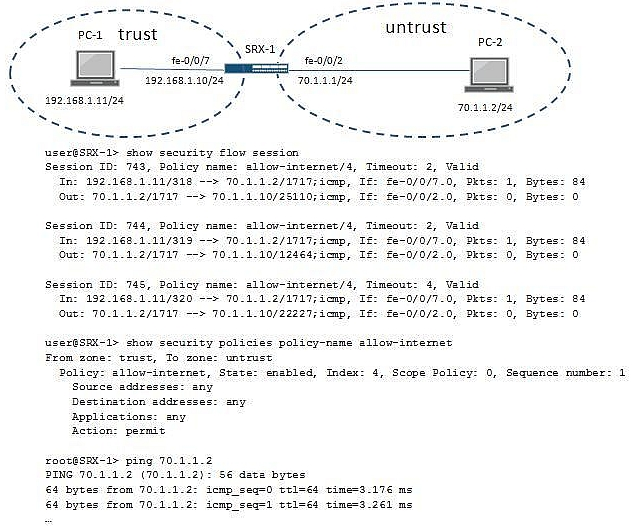
-- Exhibit --
Click the Exhibit button.
You are troubleshooting a communication problem between a trust zone and an untrust zone in the network, where PC-1 cannot ping PC-2.
Referring to the exhibit, which configuration change on SRX-1 would resolve this problem?

-- Exhibit --
Click the Exhibit button.
You are troubleshooting a communication problem between a trust zone and an untrust zone in the network, where PC-1 cannot ping PC-2.
Referring to the exhibit, which configuration change on SRX-1 would resolve this problem?
- AConfigure proxy-arp under the [edit security nat] hierarchy.
- BAdd a security policy to allow ICMP traffic from the trust zone to the untrust zone.
- CAdd an address book entry for address 70.1.1.2.
- DAdd a security policy to allow ICMP traffic from the untrust zone to the trust zone.
Correct Answer:
A
Incorrect:
B: This has already been done by permitting any source, any dest and any app.
C: No address book is used in the policy, so no need for an address book entry.
D: Add a security policy to allow ICMP from untrust to trust; this one is not valid, as session is initiated from trust zone.
A
Incorrect:
B: This has already been done by permitting any source, any dest and any app.
C: No address book is used in the policy, so no need for an address book entry.
D: Add a security policy to allow ICMP from untrust to trust; this one is not valid, as session is initiated from trust zone.
send
light_mode
delete
Question #15
-- Exhibit ""
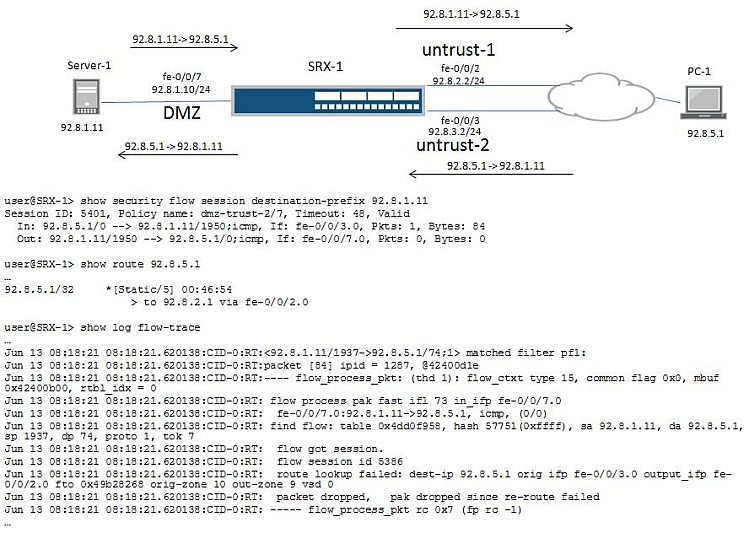
-- Exhibit --
Click the Exhibit button.
Referring to the exhibit, PC-1 is unable to ping Server-1. Traffic from PC-1 to Server-1 arrives on interface fe-0/0/3 but return traffic from Server-1 to PC-1 should be sent out from interface fe-0/0/2.
What would you change on SRX-1 to resolve this problem?

-- Exhibit --
Click the Exhibit button.
Referring to the exhibit, PC-1 is unable to ping Server-1. Traffic from PC-1 to Server-1 arrives on interface fe-0/0/3 but return traffic from Server-1 to PC-1 should be sent out from interface fe-0/0/2.
What would you change on SRX-1 to resolve this problem?
- AConfigure a security policy to allow traffic from the DMZ zone to the untrust-1 zone.
- BConfigure a security policy to allow traffic from the DMZ zone to the untrust-2 zone.
- CMove both interface fe-0/0/2 and fe-0/0/3 to the same security zone.
- DDisable TCP SYN check and TCP sequence check.
Correct Answer:
C
C
send
light_mode
delete
All Pages
