IBM C2150-620 Exam Practice Questions (P. 5)
- Full Access (60 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
A System Administrator has heard that many shopping web sites are infected due to a new vulnerability affecting shopping cart modules used by many open source e-Commerce platforms. The vulnerability only affects shopping sites using SSL.
At the System Administrator's organization, all web-based shopping applications are blocked as required by company policy. Rule 1 was already in place to accomplish this. Outbound SSL inspection was also enabled. The System Administrator has added Rule2 in an attempt to optimize inspection and better enforce company requirements.
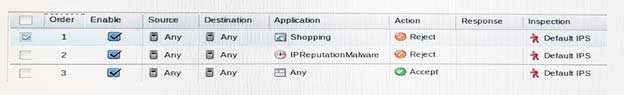
Which analysis of this Network Access Policy is correct with regard to packet inspection optimization?
At the System Administrator's organization, all web-based shopping applications are blocked as required by company policy. Rule 1 was already in place to accomplish this. Outbound SSL inspection was also enabled. The System Administrator has added Rule2 in an attempt to optimize inspection and better enforce company requirements.

Which analysis of this Network Access Policy is correct with regard to packet inspection optimization?
- ARule2 is not required, because Rule1 is already more efficient.
- BRule1 is no longer required. Rule 2 protects from infected web sites.
- CRule1 is more efficient than Rule2, but Rule2 adds a second layer protection.
- DRule2 is more efficient than Rule1, so the order of Rule1 and Rule2 should be reversed.
Correct Answer:
B
B
send
light_mode
delete
Question #22
A System Administrator wants to configure an XGS to send all IPS security event alerts to a remote system using Syslog.
How should the System Administrator configure the XGS?
How should the System Administrator configure the XGS?
- AConfigure "˜System Alerts' with "˜Remote Syslog' response objects.
- BEdit the IPS Policy object and add a "˜Remote Syslog' response object.
- CEdit the Network Access policy object and add a "˜Remote Syslog' response object.
- DEdit the signatures inside the IPS Policy object and add a "˜Remote Syslog' response object.
Correct Answer:
C
You can configure remote syslog for the IPS objects in both, the SiteProtector Console and the LMI, from the Network Access Policy (NAP) or the Shared Objects one.
SiteProtector Network Access Policy configuration:
1. Log in the SiteProtector Console and change to the Agent view.
2. Right click on the XGS entry in the SiteProtector Console Agent view and select Manage to open the Policy tab.
3. Right click on the Network Access Policy and select Open, edit the IPS object you want to enable remote syslog for and go to Response tab.
4. If a remote syslog object rule is not present, you can create a new one by selecting New > Remote Syslog.
References:
http://www-01.ibm.com/support/docview.wss?uid=swg21662575
C
You can configure remote syslog for the IPS objects in both, the SiteProtector Console and the LMI, from the Network Access Policy (NAP) or the Shared Objects one.
SiteProtector Network Access Policy configuration:
1. Log in the SiteProtector Console and change to the Agent view.
2. Right click on the XGS entry in the SiteProtector Console Agent view and select Manage to open the Policy tab.
3. Right click on the Network Access Policy and select Open, edit the IPS object you want to enable remote syslog for and go to Response tab.
4. If a remote syslog object rule is not present, you can create a new one by selecting New > Remote Syslog.
References:
http://www-01.ibm.com/support/docview.wss?uid=swg21662575
send
light_mode
delete
Question #23
The System Administrator has configured the Advanced Tuning Parameter alpsd.ssl.inverse=1 (Man-in-the-Middle (MitM) approach) to allow Diffie-Hellman key exchange usage so traffic to their internal web portal can be decrypted.
Which additional steps need to be taken to configure the XGS?
Which additional steps need to be taken to configure the XGS?
- AConfigure Inbound SSL Certificates and Inbound SSL Inspection Policy.
- BConfigure Inbound SSL Certificates and Outbound SSL Inspection Policy.
- CConfigure Outbound SSL Certificates and Inbound SSL Inspection Policy.
- DConfigure Outbound SSL Certificates and Outbound SSL Inspection Policy.
Correct Answer:
D
For outbound SSL inspection, the XGS appliance acts as the "Man-in-the-middle" and intercepts the SSL handshake between the client and server, and inserts itself and its own SSL keys into the key exchange process. From this point forward, it acts as a server to the original client and as a client to the original server. In a typical deployment, neither client nor server are aware of the SSL decryption by the appliance. In order to accomplish this, the administrator must separately deploy the certificate used by the XGS appliance into the trusted certificate list of all the clients in the enterprise.
Note: The IBM Security Network Protection appliance is acting as the "man in the middle" when outbound inspection is properly configured. The appliance is in between the server and the client.
Incorrect Answers:
A, C: For inbound SSL inspection, when a packet matches a rule to be inspected by the XGS, the XGS decrypts the packet that uses the registered certificate and private key added in the "Inbound SSL Certificates" section of the policy.
References:
http://www-01.ibm.com/support/docview.wss?uid=swg21666241
D
For outbound SSL inspection, the XGS appliance acts as the "Man-in-the-middle" and intercepts the SSL handshake between the client and server, and inserts itself and its own SSL keys into the key exchange process. From this point forward, it acts as a server to the original client and as a client to the original server. In a typical deployment, neither client nor server are aware of the SSL decryption by the appliance. In order to accomplish this, the administrator must separately deploy the certificate used by the XGS appliance into the trusted certificate list of all the clients in the enterprise.
Note: The IBM Security Network Protection appliance is acting as the "man in the middle" when outbound inspection is properly configured. The appliance is in between the server and the client.
Incorrect Answers:
A, C: For inbound SSL inspection, when a packet matches a rule to be inspected by the XGS, the XGS decrypts the packet that uses the registered certificate and private key added in the "Inbound SSL Certificates" section of the policy.
References:
http://www-01.ibm.com/support/docview.wss?uid=swg21666241
send
light_mode
delete
Question #24
A System Administrator discovered the XGS appliance is unstable after upgrading firmware to the newest version.
How should the device be restored to the previous stable state?
How should the device be restored to the previous stable state?
- ARe-image the device.
- BUse the Rollback command in the CLI.
- CSwap the inactive and active partitions.
- DRestore configuration from a snapshot.
Correct Answer:
C
Is it possible to rollback the firmware update?
Yes, it is possible to rollback the update from the LMI. Go to Manage System Settings > Firmware Settings and click the Set Active option to set your Inactive partition as Active. This will restore the device to the state it was in just prior to the update.
References:
http://www-01.ibm.com/support/docview.wss?uid=swg21965396
C
Is it possible to rollback the firmware update?
Yes, it is possible to rollback the update from the LMI. Go to Manage System Settings > Firmware Settings and click the Set Active option to set your Inactive partition as Active. This will restore the device to the state it was in just prior to the update.
References:
http://www-01.ibm.com/support/docview.wss?uid=swg21965396
send
light_mode
delete
Question #25
A System Administrator has an XGS 4100 appliance that has a single 8-port RJ-45 copper Network Interface Module (NIM) installed.
What is the maximum number of in-line network segments, of any media type, that could be protected?
What is the maximum number of in-line network segments, of any media type, that could be protected?
send
light_mode
delete
All Pages
