IBM C2150-620 Exam Practice Questions (P. 4)
- Full Access (60 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
The System Administrator has configured the XGS devices shown in the following topology diagram. Outbound SSL inspection is configured on XGS1. All XGS devices are licensed for SSL inspection, Identity and Application Control, and IP Reputation.
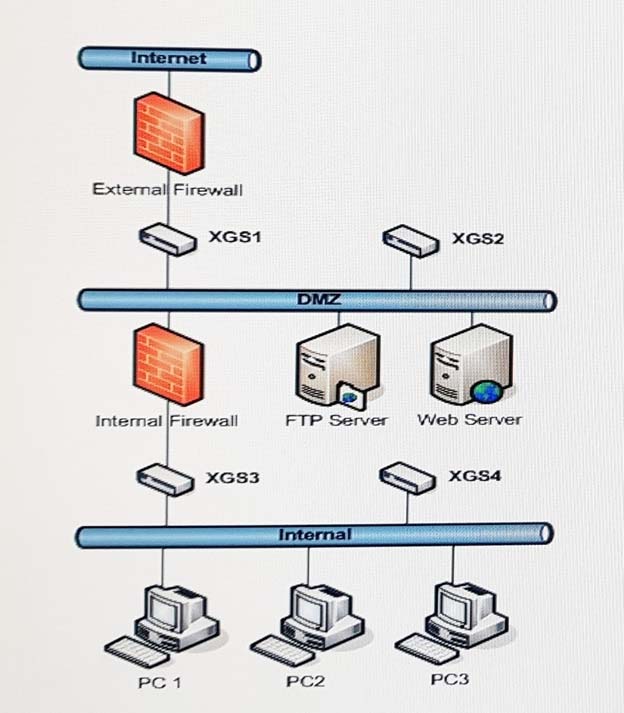
Which of the XGS devices will block PC1 from accessing a known malware web site via SSL?

Which of the XGS devices will block PC1 from accessing a known malware web site via SSL?
- AXGS1 in protection mode
- BXGS2 connected to s read-only tap port
- CXGS3 in protection mode
- DXGS4 connected to a read-only tap port
Correct Answer:
A
A
send
light_mode
delete
Question #17
A System Administrator sees a lot of Ping_Sweep events reported as blocked on the network. However, because the Ping_Sweep signature only blocks the ping packet that triggers the event, most of the ping packets are allowed through the XGS.
How can these suspicious packets be effectively blocked from the network?
How can these suspicious packets be effectively blocked from the network?
- AAdd a quarantine response to the Ping_Sweep event.
- BAdd a Network Access policy rule to reject ICMP traffic.
- CAdd a catch-all rule to the bottom of the NAP that rejects all traffic.
- DEnable the Ping_Sweep event in the default IPS policy with the Block option.
Correct Answer:
A
Question -
Why are some events allowed after setting a block response?
Cause -
Most network attacks are carried out in a single packet or in several packets that are reconstructed into a single "session." For these attacks, the Block response in the XGS Intrusion Prevention policy is appropriate to use, and is translated into a block packet response and/or into a block connection response.
Certain events, however, are classified as "non-sequitur." Non-sequitur events are events that require a succession of packets to occur before the signature is triggered. For example, a port scan signature may require a succession of ten port probes before the signature would trigger. In this case, many of the offending
"packets" would have already passed through the system.
Answer -
For these types of signatures, you must set the Quarantine response in addition to the Block response under the Default Repository > Shared Objects > Intrusion
Prevention > select signature > Edit > enable the quarantine response under the Quarantine tab > Save. The quarantine response blocks the offending IP for a period of time, ensuring that the remaining probes do not get through. The standard block packet or drop connection responses (set by the Block response) are ineffective in stopping this kind of activity when not used in conjunction with Quarantine.
List of non-sequitur events include SSH_Brute_Force.
References:
http://www-01.ibm.com/support/docview.wss?uid=swg21687475
A
Question -
Why are some events allowed after setting a block response?
Cause -
Most network attacks are carried out in a single packet or in several packets that are reconstructed into a single "session." For these attacks, the Block response in the XGS Intrusion Prevention policy is appropriate to use, and is translated into a block packet response and/or into a block connection response.
Certain events, however, are classified as "non-sequitur." Non-sequitur events are events that require a succession of packets to occur before the signature is triggered. For example, a port scan signature may require a succession of ten port probes before the signature would trigger. In this case, many of the offending
"packets" would have already passed through the system.
Answer -
For these types of signatures, you must set the Quarantine response in addition to the Block response under the Default Repository > Shared Objects > Intrusion
Prevention > select signature > Edit > enable the quarantine response under the Quarantine tab > Save. The quarantine response blocks the offending IP for a period of time, ensuring that the remaining probes do not get through. The standard block packet or drop connection responses (set by the Block response) are ineffective in stopping this kind of activity when not used in conjunction with Quarantine.
List of non-sequitur events include SSH_Brute_Force.
References:
http://www-01.ibm.com/support/docview.wss?uid=swg21687475
send
light_mode
delete
Question #18
After making changes, the System Administrator wants to verify the appliance was registered with the SiteProtector system and that current policies were synchronized with SiteProtector.
Which two methods can be used to accomplish this? (Choose two.)
Which two methods can be used to accomplish this? (Choose two.)
- AIn the SiteProtector console, select Asset view and check health status.
- BIn the SiteProtector console, check the health summary in the agent properties.
- CCreate a snapshot of the policies from SiteProtector and compare with the devices policies.
- DConnect to the device using SSH and issue service iss-spa status command to verify if it is running.
- EIn the SiteProtector, select Agent view and check the last contact column to see whether the device is Active.
Correct Answer:
DE
E: Verify that the appliance is registered with the SiteProtector System by using the SiteProtector System console.
Procedure -
1. Open the SiteProtector System console.
2. In the left pane, select the group in which you added the appliance.
3. Select the Sensor or Agent tab. The appliance is displayed in the list with a status of Active.
References:
https://www.ibm.com/support/knowledgecenter/en/SSB2MG_4.6.2/com.ibm.ips.doc/tasks/verifyingsuccessfulregistration.htm
DE
E: Verify that the appliance is registered with the SiteProtector System by using the SiteProtector System console.
Procedure -
1. Open the SiteProtector System console.
2. In the left pane, select the group in which you added the appliance.
3. Select the Sensor or Agent tab. The appliance is displayed in the list with a status of Active.
References:
https://www.ibm.com/support/knowledgecenter/en/SSB2MG_4.6.2/com.ibm.ips.doc/tasks/verifyingsuccessfulregistration.htm
send
light_mode
delete
Question #19
Security Policies of an organization demand that no network traffic should be allowed by XGS without inspection in case of XGS power failure or traffic beyond
XGS capabilities.
What should be the settings for built-in Hardware Bypass and Unanalyzed Policy?
XGS capabilities.
What should be the settings for built-in Hardware Bypass and Unanalyzed Policy?
- AHardware Bypass Mode= Fail Open; Unanalyzed Policy= Drop
- BHardware Bypass Mode= Fail Open; Unanalyzed Policy = Forward
- CHardware Bypass Mode= Fail Closed; Unanalyzed Policy= Drop
- DHardware Bypass Mode= Fail Closed; Unanalyzed Policy= Forward
Correct Answer:
B
Fail Open. Allows all network traffic to pass through the appliance.
Incorrect Answers:
C, D: Fail Closed. Closes the links for the interface pair and prevents any network traffic from passing through the appliance.
References:
https://www.ibm.com/support/knowledgecenter/en/SSHLHV_5.3.3/com.ibm.alps.doc/tasks/alps_configuring_protection_ports.htm
Note:
Hardware Bypass ModeSelect the mode to allow or to prevent traffic if the appliance fails or is powered off:
Auto. In non-HA modes, all traffic is allowed to pass through the appliance (fail open). In HA mode, interface links are closed and traffic is prevented from passing through the appliance (fail closed).
Fail Open. Allows all network traffic to pass through the appliance.
Fail Closed. Closes the links for the interface pair and prevents any network traffic from passing through the appliance.
B
Fail Open. Allows all network traffic to pass through the appliance.
Incorrect Answers:
C, D: Fail Closed. Closes the links for the interface pair and prevents any network traffic from passing through the appliance.
References:
https://www.ibm.com/support/knowledgecenter/en/SSHLHV_5.3.3/com.ibm.alps.doc/tasks/alps_configuring_protection_ports.htm
Note:
Hardware Bypass ModeSelect the mode to allow or to prevent traffic if the appliance fails or is powered off:
Auto. In non-HA modes, all traffic is allowed to pass through the appliance (fail open). In HA mode, interface links are closed and traffic is prevented from passing through the appliance (fail closed).
Fail Open. Allows all network traffic to pass through the appliance.
Fail Closed. Closes the links for the interface pair and prevents any network traffic from passing through the appliance.
send
light_mode
delete
Question #20
The System Administrator of a financial company wants to control the network traffic during office hours, for example, social networking or streaming media traffic are forbidden during business hours (08:00-19:00) but are permitted after 19:00 from Monday to Friday. The consultant from an IBM business partner suggested that the Schedule Object in Network Access Policy could be used to fulfill this objective.
Which three parameters are required to create this Schedule Object? (Choose three.)
Which three parameters are required to create this Schedule Object? (Choose three.)
- ADaily
- BComment
- CEnd Time
- DStart Time
- EExpiration Date
- FActivation Date
Correct Answer:
ACD
ACD
send
light_mode
delete
All Pages
