GIAC GCFA Exam Practice Questions (P. 4)
- Full Access (318 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
Adam works as a professional Penetration tester. A project has been assigned to him to employ penetration testing on the network of Umbrella Inc. He is running the test from home and had downloaded every security scanner from the Internet. Despite knowing the IP range of all of the systems, and the exact network configuration, Adam is unable to get any useful results.
Which of the following is the most like cause of this problem?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is the most like cause of this problem?
Each correct answer represents a complete solution. Choose all that apply.
- ASecurity scanners are only as smart as their database and cannot find unpublished vulnerabilities.
- BSecurity scanners cannot perform vulnerability linkage.
- CSecurity scanners are smart as their database and can find unpublished vulnerabilities.
- DSecurity scanners are not designed to do testing through a firewall.
Correct Answer:
ABD
ABD
send
light_mode
delete
Question #32
An organization monitors the hard disks of its employees' computers from time to time. Which policy does this pertain to?
- ANetwork security policy
- BUser password policy
- CPrivacy policy
- DBackup policy
Correct Answer:
C
C
send
light_mode
delete
Question #33
You work as a Network Administrator for Net World International. You have configured the hard disk drive of your computer as shown in the image below:
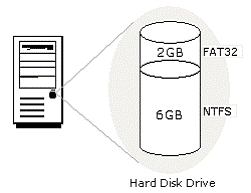
The computer is configured to dual-boot with Windows 2000 Server and Windows 98. While working on Windows 2000 Server, you save a file on the 6GB partition. You are unable to find the file while working on Windows 98. You are not even able to access the partition on which the file is saved. What is the most likely cause?

The computer is configured to dual-boot with Windows 2000 Server and Windows 98. While working on Windows 2000 Server, you save a file on the 6GB partition. You are unable to find the file while working on Windows 98. You are not even able to access the partition on which the file is saved. What is the most likely cause?
- AThe file is corrupt.
- BThe 6GB partition is corrupt.
- CWindows 98 does not support the NTFS file system.
- DFiles saved in Windows 98 are not supported by Windows 2000.
Correct Answer:
C
C
send
light_mode
delete
Question #34
Peter works as a Computer Hacking Forensic Investigator. He has been called by an organization to conduct a seminar to give necessary information related to sexual harassment within the work place. Peter started with the definition and types of sexual harassment. He then wants to convey that it is important that records of the sexual harassment incidents should be maintained, which helps in further legal prosecution. Which of the following data should be recorded in this documentation?
Each correct answer represents a complete solution. Choose all that apply.
Each correct answer represents a complete solution. Choose all that apply.
- ANames of the victims
- BDate and time of incident
- CNature of harassment
- DLocation of each incident
Correct Answer:
ABD
ABD
send
light_mode
delete
Question #35
Which of the following types of computers is used for attracting potential intruders?
send
light_mode
delete
Question #36
Which of the following standard file formats is used by Apple's iPod to store contact information?
send
light_mode
delete
Question #37
Which of the following file systems cannot be used to install an operating system on the hard disk drive?
Each correct answer represents a complete solution. Choose two.
Each correct answer represents a complete solution. Choose two.
- AWindows NT file system (NTFS)
- BHigh Performance File System (HPFS)
- CLog-structured file system (LFS)
- DCompact Disc File System (CDFS)
- ENovell Storage Services (NSS)
Correct Answer:
CD
CD
send
light_mode
delete
Question #38
Which of the following types of evidence proves or disproves a specific act through oral testimony based on information gathered through the witness's five senses?
- AConclusive evidence
- BBest evidence
- CHearsay evidence
- DDirect evidence
Correct Answer:
D
D
send
light_mode
delete
Question #39
Which of the following two cryptography methods are used by NTFS Encrypting File System (EFS) to encrypt the data stored on a disk on a file-by-file basis?
send
light_mode
delete
Question #40
Which of the following sections of an investigative report covers the background and summary of the report including the outcome of the case and the list of allegations?
send
light_mode
delete
All Pages
