GIAC GCFA Exam Practice Questions (P. 2)
- Full Access (318 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
Which of the following encryption methods uses AES technology?
send
light_mode
delete
Question #12
Mark works as a security manager for SofTech Inc. He is using a technique for monitoring what the employees are doing with corporate resources. Which of the following techniques is being used by Mark to gather evidence of an ongoing computer crime if a member of the staff is e-mailing company's secrets to an opponent?
- AElectronic surveillance
- BCivil investigation
- CPhysical surveillance
- DCriminal investigation
Correct Answer:
A
A
send
light_mode
delete
Question #13
Which of the following is the first computer virus that was used to infect the boot sector of storage media formatted with the DOS File Allocation Table (FAT) file system?
send
light_mode
delete
Question #14
Which of the following attacks saturates network resources and disrupts services to a specific computer?
- ATeardrop attack
- BPolymorphic shell code attack
- CDenial-of-Service (DoS) attack
- DReplay attack
Correct Answer:
C
C
send
light_mode
delete
Question #15
Peter works as a Technical Representative in a CSIRT for SecureEnet Inc. His team is called to investigate the computer of an employee, who is suspected for classified data theft. Suspect's computer runs on Windows operating system. Peter wants to collect data and evidences for further analysis. He knows that in
Windows operating system, the data is searched in pre-defined steps for proper and efficient analysis. Which of the following is the correct order for searching data on a Windows based system?
Windows operating system, the data is searched in pre-defined steps for proper and efficient analysis. Which of the following is the correct order for searching data on a Windows based system?
- AVolatile data, file slack, registry, memory dumps, file system, system state backup, internet traces
- BVolatile data, file slack, registry, system state backup, internet traces, file system, memory dumps
- CVolatile data, file slack, internet traces, registry, memory dumps, system state backup, file system
- DVolatile data, file slack, file system, registry, memory dumps, system state backup, internet traces
Correct Answer:
D
D
send
light_mode
delete
Question #16
Adam works as a Security Administrator for Umbrella Inc. He is responsible for securing all 15 servers of the company. To successfully accomplish the task, he enables the hardware and software firewalls and disables all unnecessary services on all the servers. Sales manager of the company asks Adam to run emulation software on one of the servers that requires the telnet service to function properly. Adam is concerned about the security of the server, as telnet can be a very large security risk in an organization. Adam decides to perform some footprinting, scanning, and penetration testing on the server to checkon the server to check the security. Adam telnets into the server and writes the following command:
HEAD / HTTP/1.0 -
After pressing enter twice, Adam gets the following results:
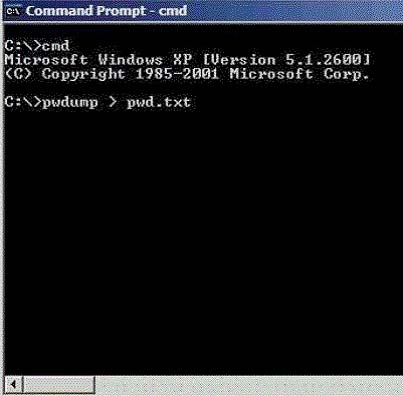
Which of the following tasks has Adam just accomplished?
HEAD / HTTP/1.0 -
After pressing enter twice, Adam gets the following results:

Which of the following tasks has Adam just accomplished?
- APoisoned the local DNS cache of the server.
- BSubmitted a remote command to crash the server.
- CGrabbed the banner.
- DDownloaded a file to his local computer.
Correct Answer:
C
C
send
light_mode
delete
Question #17
The MBR of a hard disk is a collection of boot records that contain disk information such as disk architecture, cluster size, and so on. The main work of the MBR is to locate and run necessary operating system files that are required to run a hard disk. In the context of the operating system, MBR is also known as the boot loader. Which of the following viruses can infect the MBR of a hard disk?
Each correct answer represents a complete solution. Choose two.
Each correct answer represents a complete solution. Choose two.
send
light_mode
delete
Question #18
You work as a professional Computer Hacking Forensic Investigator for DataEnet Inc. You want to investigate e-mail information of an employee of the company.
The suspected employee is using an online e-mail system such as Hotmail or Yahoo. Which of the following folders on the local computer will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
The suspected employee is using an online e-mail system such as Hotmail or Yahoo. Which of the following folders on the local computer will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
- AHistory folder
- BTemporary Internet Folder
- CDownload folder
- DCookies folder
Correct Answer:
ABD
ABD
send
light_mode
delete
Question #19
Which of the following methods is used by forensic investigators to acquire an image over the network in a secure manner?
- ADOS boot disk
- BLinux Live CD
- CSecure Authentication for EnCase (SAFE)
- DEnCase with a hardware write blocker
Correct Answer:
C
C
send
light_mode
delete
Question #20
You company suspects an employee of sending unauthorized emails to competitors. These emails are alleged to contain confidential company data. Which of the following is the most important step for you to take in preserving the chain of custody?
- APreserve the email server including all logs.
- BMake copies of that employee's email.
- CSeize the employee's PC.
- DPlace spyware on the employee's PC to confirm these activities.
Correct Answer:
A
A
send
light_mode
delete
All Pages
