Cisco® 642-885 Exam Practice Questions (P. 2)
- Full Access (131 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #6
Refer to the topology diagram shown in the exhibit and the partial configurations shown below.
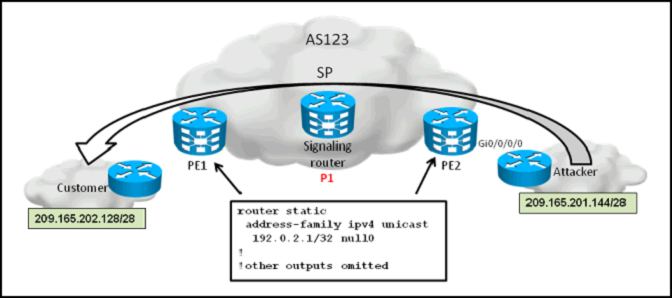
Once the attack from 209.165.201.144/28 to 209.165.202.128/28 has been detected, which additional configurations are required on the P1 IOS-XR router to implement source-based remote-triggered black hole filtering?
!
router bgp 123
address-family ipv4 unicast
redistribute static route-policy test
!

Once the attack from 209.165.201.144/28 to 209.165.202.128/28 has been detected, which additional configurations are required on the P1 IOS-XR router to implement source-based remote-triggered black hole filtering?
!
router bgp 123
address-family ipv4 unicast
redistribute static route-policy test
!
- Arouter staticaddress-family ipv4 unicast209.165.202.128/28 null0 tag 666192.0.2.1/32 null0 tag 667!route-policy testif tag is 666 thenset next-hop 192.0.2.1endifif tag is 667 thenset community (no-export)endifend-policy!
- Brouter staticaddress-family ipv4 unicast209.165.201.144/28 null0 tag 666192.0.2.1/32 null0 tag 667!route-policy testif tag is 666 thenset next-hop 192.0.2.1endifif tag is 667 thenset community (no-export)endifend-policy!
- Crouter staticaddress-family ipv4 unicast209.165.201.144/28 null0 tag 666192.0.2.1/32 null0!route-policy testif tag is 666 thenset next-hop 192.0.2.1set community (no-export)endifend-policy
- Drouter staticaddress-family ipv4 unicast209.165.202.128/28 null0 tag 666192.0.2.1/32 null0!route-policy testif tag is 666 thenset next-hop 192.0.2.1set community (no-export)endifend-policy!
Correct Answer:
C
Source-Based RTBH Filtering -
With destination-based black holing, all traffic to a specific destination is dropped after the black hole has been activated, regardless of where it is coming from.
Obviously, this could include legitimate traffic destined for the target. Source-based black holes provide the ability to drop traffic at the network edge based on a specific source address or range of source addresses.
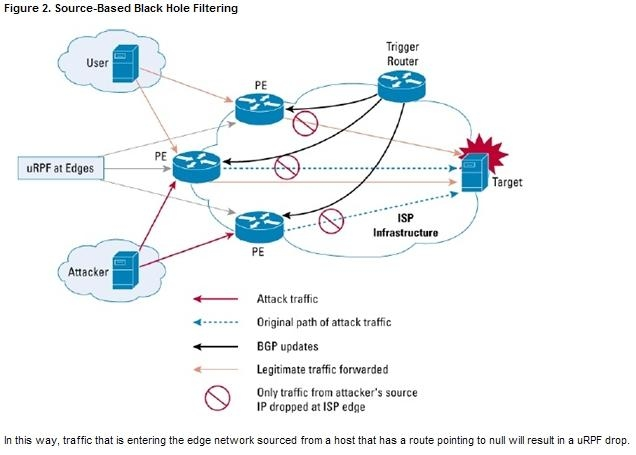
If the source address (or range of addresses) of the attack can be identified (spoofed or not), it would be better to drop all traffic at the edge based on the source address, regardless of the destination address. This would permit legitimate traffic from other sources to reach the target. Implementation of source-based black hole filtering depends on Unicast Reverse Path Forwarding (uRPF), most often loose mode uRPF. Loose mode uRPF checks the packet and forwards it if there is a route entry for the source IP of the incoming packet in the router forwarding information base (FIB). If the router does not have an FIB entry for the source
IP address, or if the entry points to a null interface, the Reverse Path Forwarding (RPF) check fails and the packet is dropped, as shown in Figure 2. Because uRPF validates a source IP address against its FIB entry, dropping traffic from specific source addresses is accomplished by configuring loose mode uRPF on the external interface and ensuring the RPF check fails by inserting a route to the source with a next hop of Null0. This can be done by using a trigger device to send
IBGP updates. These updates set the next hop for the source IP to an unused IP address that has a static entry at the edge, setting it to null as shown in Figure 2.
C
Source-Based RTBH Filtering -
With destination-based black holing, all traffic to a specific destination is dropped after the black hole has been activated, regardless of where it is coming from.
Obviously, this could include legitimate traffic destined for the target. Source-based black holes provide the ability to drop traffic at the network edge based on a specific source address or range of source addresses.
If the source address (or range of addresses) of the attack can be identified (spoofed or not), it would be better to drop all traffic at the edge based on the source address, regardless of the destination address. This would permit legitimate traffic from other sources to reach the target. Implementation of source-based black hole filtering depends on Unicast Reverse Path Forwarding (uRPF), most often loose mode uRPF. Loose mode uRPF checks the packet and forwards it if there is a route entry for the source IP of the incoming packet in the router forwarding information base (FIB). If the router does not have an FIB entry for the source
IP address, or if the entry points to a null interface, the Reverse Path Forwarding (RPF) check fails and the packet is dropped, as shown in Figure 2. Because uRPF validates a source IP address against its FIB entry, dropping traffic from specific source addresses is accomplished by configuring loose mode uRPF on the external interface and ensuring the RPF check fails by inserting a route to the source with a next hop of Null0. This can be done by using a trigger device to send
IBGP updates. These updates set the next hop for the source IP to an unused IP address that has a static entry at the edge, setting it to null as shown in Figure 2.

send
light_mode
delete
Question #7
In Cisco IOS-XR, the maximum-prefix command, to control the number of prefixes that can be installed from a BGP neighbor, is configured under which configuration mode?
- ARP/0/RSP0/CPU0:P2(config-bgp)#
- BRP/0/RSP0/CPU0:P2(config-bgp-af)#
- CRP/0/RSP0/CPU0:P2(config-bgp-nbr)#
- DRP/0/RSP0/CPU0:P2(config-bgp-nbr-af)#
Correct Answer:
D
http://www.cisco.com/en/US/tech/tk365/technologies_configuration_example09186a008010a28a.shtml
D
http://www.cisco.com/en/US/tech/tk365/technologies_configuration_example09186a008010a28a.shtml
send
light_mode
delete
Question #8
In Cisco IOS-XR, the ttl-security command is configured under which configuration mode?
- ARP/0/RSP0/CPU0:P2(config)#
- BRP/0/RSP0/CPU0:P2(config-bgp)#
- CRP/0/RSP0/CPU0:P2(config-bgp-nbr)#
- DRP/0/RSP0/CPU0:P2(config-bgp-af)#
- ERP/0/RSP0/CPU0:P2(config-bgp-nbr-af)#
Correct Answer:
C
http://packetlife.net/blog/2009/nov/23/understanding-bgp-ttl-security/
C
http://packetlife.net/blog/2009/nov/23/understanding-bgp-ttl-security/
send
light_mode
delete
Question #9
Refer to the exhibit.
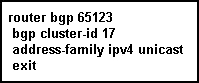
Given the partial BGP configuration, which configuration correctly completes the Cisco IOS-XR route reflector configuration where both the 1.1.1.1 and 2.2.2.2 routers are the clients and the 3.3.3.3 router is a non-client IBGP peer?

Given the partial BGP configuration, which configuration correctly completes the Cisco IOS-XR route reflector configuration where both the 1.1.1.1 and 2.2.2.2 routers are the clients and the 3.3.3.3 router is a non-client IBGP peer?
- Aneighbor 1.1.1.1remote-as 65123route-reflector-clientneighbor 2.2.2.2remote-as 65123route-reflector-clientneighbor 3.3.3.3remote-as 65123
- Bneighbor 1.1.1.1address-family ipv4 unicastremote-as 65123route-reflector-clientneighbor 2.2.2.2address-family ipv4 unicastremote-as 65123route-reflector- clientneighbor 3.3.3.3address-family ipv4 unicastremote-as 65123
- Cneighbor 1.1.1.1remote-as 65123address-family ipv4 unicastroute-reflector-clientneighbor 2.2.2.2remote-as 65123address-family ipv4 unicastroute-reflector- clientneighbor 3.3.3.3remote-as 65123
- Dneighbor 1.1.1.1 remote-as 65123neighbor 1.1.1.1 route-reflector-clientneighbor 2.2.2.2 remote-as 65123neighbor 2.2.2.2 route-reflector-clientneighbor 3.3.3.3
Correct Answer:
C
C
send
light_mode
delete
Question #10
Which three methods can be used to reduce the full-mesh IBGP requirement in a service provider core network? (Choose three.)
- AImplement route reflectors
- BEnable multi-protocol BGP sessions between all the PE routers
- CImplement confederations
- DImplement MPLS (LDP) in the core network on all the PE and P routers
- EEnable BGP synchronization
- FDisable the IBGP split-horizon rule
Correct Answer:
ACD
ACD
send
light_mode
delete
All Pages
