Cisco® 350-201 Exam Practice Questions (P. 3)
- Full Access (139 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
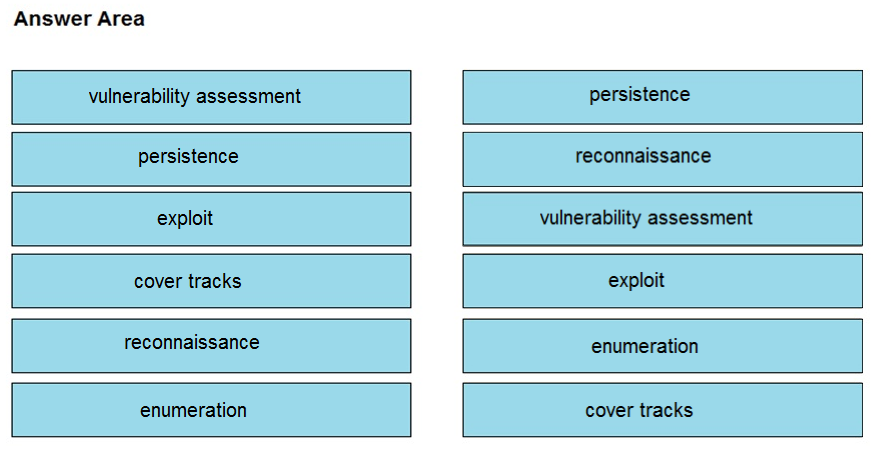
DRAG DROP -
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.
Select and Place:
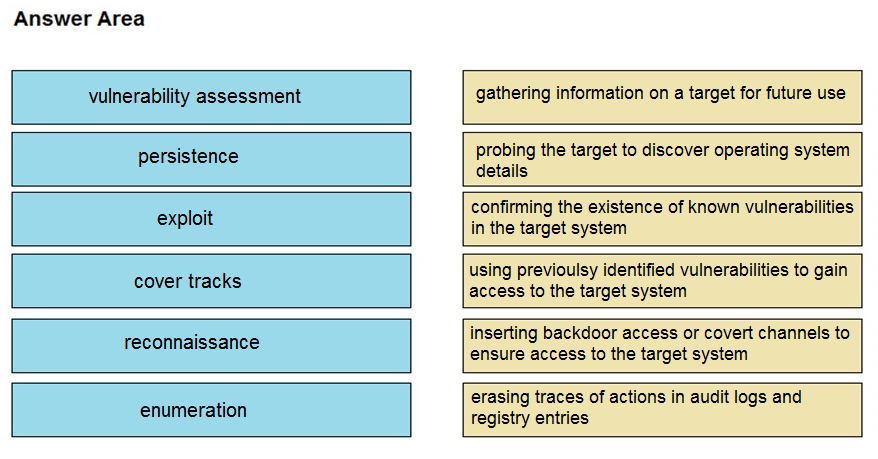
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.
Select and Place:

send
light_mode
delete
Question #12
According to GDPR, what should be done with data to ensure its confidentiality, integrity, and availability?
- APerform a vulnerability assessment
- BConduct a data protection impact assessmentMost Voted
- CConduct penetration testing
- DPerform awareness testing
Correct Answer:
B
Reference:
https://apdcat.gencat.cat/web/.content/03-documentacio/Reglament_general_de_proteccio_de_dades/documents/DPIA-Guide.pdf
B
Reference:
https://apdcat.gencat.cat/web/.content/03-documentacio/Reglament_general_de_proteccio_de_dades/documents/DPIA-Guide.pdf
send
light_mode
delete
Question #13
A payroll administrator noticed unexpected changes within a piece of software and reported the incident to the incident response team. Which actions should be taken at this step in the incident response workflow?
- AClassify the criticality of the information, research the attacker's motives, and identify missing patches
- BDetermine the damage to the business, extract reports, and save evidence according to a chain of custodyMost Voted
- CClassify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
- DDetermine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation plan
Correct Answer:
B
B
send
light_mode
delete
Question #14
A company recently completed an internal audit and discovered that there is CSRF vulnerability in 20 of its hosted applications. Based on the audit, which recommendation should an engineer make for patching?
- AIdentify the business applications running on the assets
- BUpdate software to patch third-party software
- CValidate CSRF by executing exploits within Metasploit
- DFix applications according to the risk scoresMost Voted
Correct Answer:
D
D
send
light_mode
delete
Question #15
An engineer is analyzing a possible compromise that happened a week ago when the company database servers unexpectedly went down. The analysis reveals that attackers tampered with Microsoft SQL Server Resolution Protocol and launched a DDoS attack. The engineer must act quickly to ensure that all systems are protected. Which two tools should be used to detect and mitigate this type of future attack? (Choose two.)
send
light_mode
delete
All Pages