Cisco® 350-201 Exam Practice Questions (P. 2)
- Full Access (139 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #6
The physical security department received a report that an unauthorized person followed an authorized individual to enter a secured premise. The incident was documented and given to a security specialist to analyze. Which step should be taken at this stage?
- ADetermine the assets to which the attacker has access
- BIdentify assets the attacker handled or acquired
- CChange access controls to high risk assets in the enterprise
- DIdentify movement of the attacker in the enterpriseMost Voted
Correct Answer:
D
D
send
light_mode
delete
Question #7
A new malware variant is discovered hidden in pirated software that is distributed on the Internet. Executives have asked for an organizational risk assessment.
The security officer is given a list of all assets. According to NIST, which two elements are missing to calculate the risk assessment? (Choose two.)
The security officer is given a list of all assets. According to NIST, which two elements are missing to calculate the risk assessment? (Choose two.)
- Aincident response playbooks
- Basset vulnerability assessmentMost Voted
- Creport of staff members with asset relations
- Dkey assets and executives
- Emalware analysis reportMost Voted
Correct Answer:
BE
Reference:
https://cloudogre.com/risk-assessment/
BE
Reference:
https://cloudogre.com/risk-assessment/
send
light_mode
delete
Question #8

Refer to the exhibit. At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
- Aexploitation
- Bactions on objectives
- CdeliveryMost Voted
- Dreconnaissance
Correct Answer:
C
Reference:
https://www2.deloitte.com/content/dam/Deloitte/sg/Documents/risk/sea-risk-cyber-101-july2017.pdf
C
Reference:
https://www2.deloitte.com/content/dam/Deloitte/sg/Documents/risk/sea-risk-cyber-101-july2017.pdf
send
light_mode
delete
Question #9
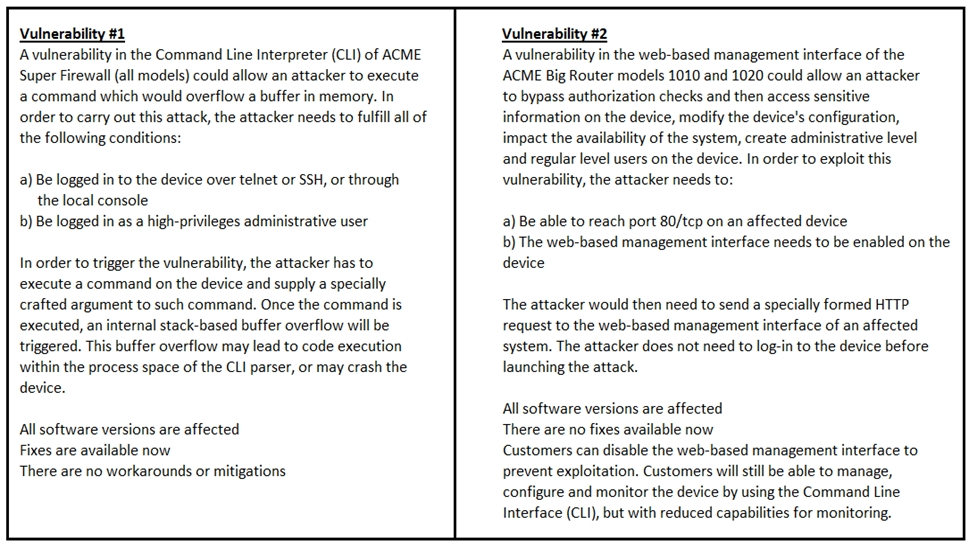
Refer to the exhibit. How must these advisories be prioritized for handling?
- AThe highest priority for handling depends on the type of institution deploying the devices
- BVulnerability #2 is the highest priority for every type of institutionMost Voted
- CVulnerability #1 and vulnerability #2 have the same priority
- DVulnerability #1 is the highest priority for every type of institution
Correct Answer:
D
D
send
light_mode
delete
Question #10
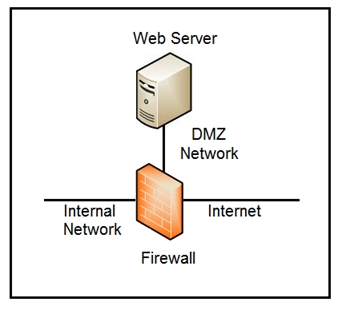
Refer to the exhibit. Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
- ACreate an ACL on the firewall to allow only TLS 1.3Most Voted
- BImplement a reverse server in the DMZ networkMost Voted
- CCreate an ACL on the firewall to allow only external connections
- DMove the webserver to the internal network
- EMove the webserver to the external network
Correct Answer:
BD
BD
send
light_mode
delete
All Pages
