Cisco® 300-915 Exam Practice Questions (P. 5)
- Full Access (59 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
An IoT application has been built into the application CI/CD pipeline. The application needs credentials to access other applications, APIs, and cloud resources.
When should the credentials be inserted into the application using the CI/CD process?
When should the credentials be inserted into the application using the CI/CD process?
- Ahard coded into your application code base
- Bduring application runtime
- Cafter application testing
- Dduring application build time
Correct Answer:
A
A
send
light_mode
delete
Question #22
Which two statements about how to provision and manage data originators in a cloud environment are true? (Choose two.)
- AThe provisioning of digital identities is the responsibility of the data originators.
- BCloud providers offer services for automated device provisioning, which allows the lifecycle of the cloud-representation for data originators to be managed.
- CCloud providers offer application programming interfaces, which allow a programmatic provisioning of data originators.
- DThere is no need to provision and manage access for data originators in the cloud.
- EThe access to public clouds must be configured and managed manually.
Correct Answer:
CE
CE
send
light_mode
delete
Question #23
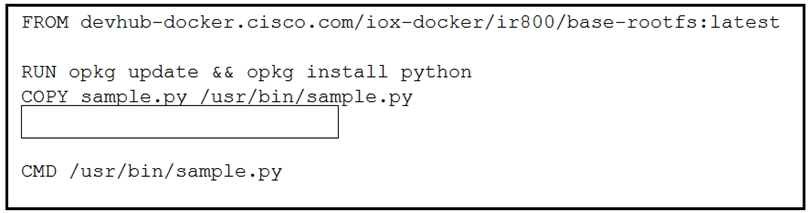
Refer to the exhibit. Which line of code completes the Dockerfile?
- ARUN chmod 777 /usr/bin/sample.py
- BRUN chown root:root /usr/bin/sample.py
- CWORKDIR /usr/bin
- DUSER root
Correct Answer:
A
A
send
light_mode
delete
Question #24
A network is being configured for an Ethernet-connected sensor. The sensor fails to send data to the configured destination. The IP address of the sensor can be pinged from a laptop on the same subnet. When a different subnet is used, the sensor cannot be reached, but other clients on the same subnet are still accessible.
What are two reasons for the connectivity problem? (Choose two.)
What are two reasons for the connectivity problem? (Choose two.)
- Awrong DNS server on the sensor
- Bwrong subnet mask on your laptop
- Cwrong default gateway on the sensor
- Dwrong default gateway on your laptop
- Ewrong subnet mask on the sensor
Correct Answer:
CE
CE
send
light_mode
delete
Question #25
As part of an IoT project, an organization is developing an application that will share multiple clients using a REST API.
Based on the software development process, what are two valid technical activities that can be suggested to secure the REST API that is developed during the development of the software? (Choose two.)
Based on the software development process, what are two valid technical activities that can be suggested to secure the REST API that is developed during the development of the software? (Choose two.)
- ARespond to request failures in detail to allow users for easier troubleshooting.
- BImplement HTTP whitelisting to only methods that are allowed.
- CImplement and review audit logs for security-related events.
- DReject HTTP methods that are invalid with an error code 404.
- EImplement physical firewalling and access control to the resources.
Correct Answer:
BD
BD
send
light_mode
delete
All Pages
