Cisco® 300-915 Exam Practice Questions (P. 2)
- Full Access (59 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #6
When constructing a Python script for data extraction using GMM APIs on a Cisco Kinetic Cloud platform, how should the API authentication be implemented?
- AGenerate the API keys once and edit the permissions as needed.
- BGenerate and use the API keys for the required access level from the Kinetic Cloud application.
- CUse a complex username and password with 128-bit encryption.
- DUse a complex username with an auto-generated password from the Kinetic Cloud application.
Correct Answer:
B
B
send
light_mode
delete
Question #7
An IoT engineer is responsible for security at an organization. Humans and machines need to be allowed to access services like database or compute on AWS.
The engineer decides to implement dynamic secrets.
Which method helps to get this implementation accurate from a security point of view?
The engineer decides to implement dynamic secrets.
Which method helps to get this implementation accurate from a security point of view?
- ACreate a central secret system for humans and machine to obtain very short-lived dynamic secrets to access any service.
- BHumans cannot be trusted, and each time they authenticate they should be issued with dynamic secrets. Machines can be trusted, and they can be issued with static credentials.
- CMaintain a different service associated to secret systems to issue access.
- DAfter a user is authenticated by any trusted system, the user can be trusted to use any service.
Correct Answer:
A
A
send
light_mode
delete
Question #8
Which statement explains the correct position of a PLC within the CPwE architecture?
- APLCs are always part of Level 0 "" process control.
- BPLCs are part of Level 4 "" site business planning.
- CPLCs are part of Level 1 "" basic control.
- DPLCs are placed at Level 2 "" area supervisory control.
Correct Answer:
C
C
send
light_mode
delete
Question #9
A sensor reads potentially critical data from an industrial device, but most of the data from the sensor is not critical information and does not change unless a critical event happens.
Which data work flow is appropriate for how the critical and non-critical data is processed?
Which data work flow is appropriate for how the critical and non-critical data is processed?
- A1. Acquire sensor data. 2. Filter non-actionable data. 3. Perform action on data. 4. Send critical data and action performed on data to cloud for storing.
- B1. Acquire sensor data. 2. Send data to cloud for processing and to determine action. 3. Send required action back to edge for action completion. 4. Perform action on data.
- C1. Acquire sensor data. 2. Filter non-actionable data. 3. Perform action on data.
- D1. Acquire sensor data. 2. Perform action on data. 3. Send data and action performed on data to cloud for recording.
Correct Answer:
D
D
send
light_mode
delete
Question #10
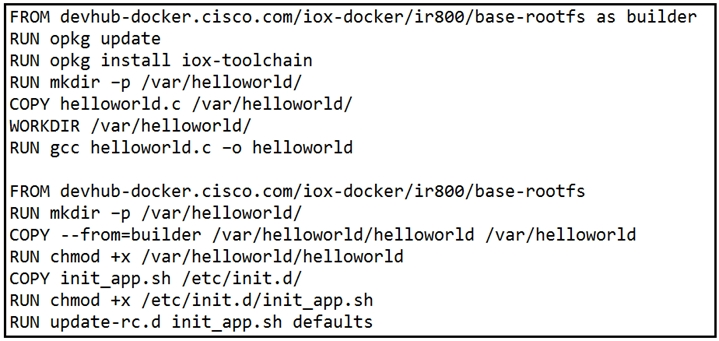
Refer to the exhibit. When a Docker image is built using this Dockerfile, which two statements are valid on Cisco IOx 1.8 and before? (Choose two.)
- AIt builds an image that can be executed on all Cisco platforms.
- BIt builds a Docker image that cannot be used directly on Cisco IOx.
- CIt compiles a "hello world" program in C.
- DIt creates two separate images.
- EIt builds an IOx package that can be deployed directly.
Correct Answer:
BC
BC
send
light_mode
delete
All Pages
