Cisco® 300-375 Exam Practice Questions (P. 3)
- Full Access (53 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
After receiving an alert regarding a rogue AP, a network engineer logs into Cisco Prime and looks at the floor map where the AP that detected the rogue is located.
The map is synchronized with a mobility services engine that determines the rogue device is actually inside the campus. The engineer determines the rogue to be a security threat and decides to stop it from broadcasting inside the enterprise wireless network. What is the fastest way to disable the rogue?
The map is synchronized with a mobility services engine that determines the rogue device is actually inside the campus. The engineer determines the rogue to be a security threat and decides to stop it from broadcasting inside the enterprise wireless network. What is the fastest way to disable the rogue?
- AGo to the location the rogue device is indicated to be and disable the power.Most Voted
- BCreate an SSID on the WLAN controller resembling the SSID of the rogue to spoof it and disable clients from connecting to it.
- CClassify the rogue as malicious in Cisco Prime.
- DUpdate the status of the rogue in Cisco Prime to contained.
Correct Answer:
C
Please refer to the step 10 of the topic "Configuring Rouge Detection" of the reference link.
Reference: http://www.cisco.com/c/en/us/td/docs/wireless/controller/7-4/configuration/guides/consolidated/b_cg74_CONSOLIDATED/ b_cg74_CONSOLIDATED_chapter_0111101.pdf
C
Please refer to the step 10 of the topic "Configuring Rouge Detection" of the reference link.
Reference: http://www.cisco.com/c/en/us/td/docs/wireless/controller/7-4/configuration/guides/consolidated/b_cg74_CONSOLIDATED/ b_cg74_CONSOLIDATED_chapter_0111101.pdf
send
light_mode
delete
Question #12
An engineer is configuring client MFP. What WLAN Layer 2 security must be selected to use client MFP?
- AStatic WEP
- BCKIP
- CWPA + WPA2
- D802.1x
Correct Answer:
C
In 802.11, management frames such as (de)authentication, (dis)association, beacons, and probes are always unauthenticated and unencrypted. In other words, 802.11 management frames are always sent in an unsecured manner, unlike the data traffic, which are encrypted with protocols such as WPA,
WPA2, or, at least, WEP, and so forth.
Reference: http://www.cisco.com/c/en/us/support/docs/wireless-mobility/wlan-security/82196-mfp.html#climfp
C
In 802.11, management frames such as (de)authentication, (dis)association, beacons, and probes are always unauthenticated and unencrypted. In other words, 802.11 management frames are always sent in an unsecured manner, unlike the data traffic, which are encrypted with protocols such as WPA,
WPA2, or, at least, WEP, and so forth.
Reference: http://www.cisco.com/c/en/us/support/docs/wireless-mobility/wlan-security/82196-mfp.html#climfp
send
light_mode
delete
Question #13
Which two events are possible outcomes of a successful RF jamming attack? (Choose two.)
- Aunauthentication association
- Bdeauthentication multicast
- Cdeauthentication broadcast
- Ddisruption of WLAN services
- Ephysical damage to AP hardware
Correct Answer:
DE
WLAN reliability and efficiency depend on the quality of the radio frequency (RF) media. Each RF is susceptible to RF noise impact. An attacker using this WLAN vulnerability can perform two types of DoS attacks:
Disrupt WLAN service At the 2.4 GHz unlicensed spectrum, the attack may be unintentional. A cordless phone, Bluetooth devices, microwave, wireless surveillance video camera, or baby monitor can all emit RF energy to disrupt WLAN service. Malicious attacks can manipulate the RF power at 2.4 GHz or 5 GHz spectrum with a high-gain directional antenna to amplify the attack impact from a distance. With free-space and indoor attenuation, a 1-kW jammer 300 feet away from a building can jam 50 to 100 feet into the office area. The same 1-kW jammer located inside a building can jam 180 feet into the office area. During the attack, WLAN devices in the target area are out of wireless service.
Physically damage AP hardware An attacker using a high-output transmitter with directional high gain antenna 30 yards away from an access point can pulse enough RF power to damage electronics in the access point putting it being permanently out of service. Such High Energy RF (HERF) guns are effective and are inexpensive to build.
Reference: http://www.cisco.com/c/en/us/td/docs/wireless/mse/3350/5-2/wIPS/configuration/guide/msecg_wIPS/msecg_appA_wIPS.html
DE
WLAN reliability and efficiency depend on the quality of the radio frequency (RF) media. Each RF is susceptible to RF noise impact. An attacker using this WLAN vulnerability can perform two types of DoS attacks:
Disrupt WLAN service At the 2.4 GHz unlicensed spectrum, the attack may be unintentional. A cordless phone, Bluetooth devices, microwave, wireless surveillance video camera, or baby monitor can all emit RF energy to disrupt WLAN service. Malicious attacks can manipulate the RF power at 2.4 GHz or 5 GHz spectrum with a high-gain directional antenna to amplify the attack impact from a distance. With free-space and indoor attenuation, a 1-kW jammer 300 feet away from a building can jam 50 to 100 feet into the office area. The same 1-kW jammer located inside a building can jam 180 feet into the office area. During the attack, WLAN devices in the target area are out of wireless service.
Physically damage AP hardware An attacker using a high-output transmitter with directional high gain antenna 30 yards away from an access point can pulse enough RF power to damage electronics in the access point putting it being permanently out of service. Such High Energy RF (HERF) guns are effective and are inexpensive to build.
Reference: http://www.cisco.com/c/en/us/td/docs/wireless/mse/3350/5-2/wIPS/configuration/guide/msecg_wIPS/msecg_appA_wIPS.html
send
light_mode
delete
Question #14
Which CLI command do you use on Cisco IOS XE Software to put the AP named Floor1_AP1 back in the default AP group?
- Aap Floor1_AP1 ap-groupname default-group
- Bap name Floor1_AP1 apgroup default-group
- Cap name Floor1_AP1 ap-groupname default-group
- Dap name Floor1_AP1 ap-groupname default
Correct Answer:
C
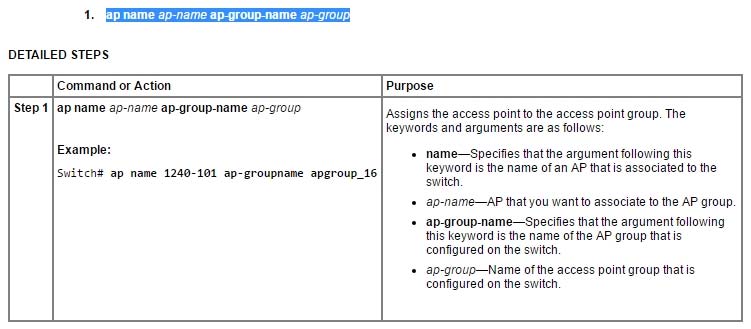
Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst3850/software/release/3.2_0_se/multibook/configuration_guide/ b_multibook_config_guide_wireless_3850_chapter_0110.html
C

Reference: http://www.cisco.com/en/US/docs/switches/lan/catalyst3850/software/release/3.2_0_se/multibook/configuration_guide/ b_multibook_config_guide_wireless_3850_chapter_0110.html
send
light_mode
delete
Question #15
An engineer is configuring a new mobility anchor for a WLAN on the CLI with the config wlan mobility anchor add 3 10.10.10.10 command, but the command is failing. Which two conditions must be met to be able to enter this command? (Choose two.)
- AThe anchor controller IP address must be within the management interface subnet.
- BThe anchor controller must be in the same mobility group.
- CThe WLAN ID must be enabled.
- DThe mobility group keepalive must be configured.
- EThe indicated WLAN ID must be present on the controller.
Correct Answer:
AB
AB
send
light_mode
delete
All Pages
