Cisco® 300-101 Exam Practice Questions (P. 5)
- Full Access (1468 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
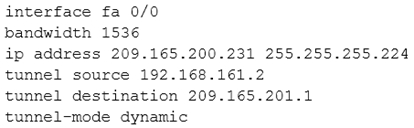
Question #41
A company has just opened two remote branch offices that need to be connected to the corporate network. Which interface configuration output can be applied to the corporate router to allow communication to the remote sites?
A.
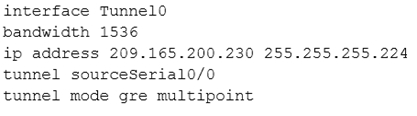
B.
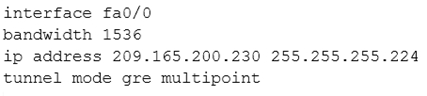
C.

D.
A.

B.

C.

D.

Correct Answer:
A
The configuration of mGRE allows a tunnel to have multiple destinations. The configuration of mGRE on one side of a tunnel does not have any relation to the tunnel properties that might exist at the exit points. This means that an mGRE tunnel on the hub may connect to a p2p tunnel on the branch. Conversely, a p2p
GRE tunnel may connect to an mGRE tunnel. The distinguishing feature between an mGRE interface and a p2p GRE interface is the tunnel destination. An mGRE interface does not have a configured destination. Instead the GRE tunnel is configured with the command tunnel mode gre multipoint. This command is used instead of the tunnel destination x.x.x.x found with p2p GRE tunnels. Besides allowing for multiple destinations, an mGRE tunnel requires NHRP to resolve the tunnel endpoints. Note, tunnel interfaces by default are point-to-point (p-p) using GRE encapsulation, effectively they have the tunnel mode gre command, which is not seen in the configuration because it is the default.
The mGRE configuration is as follows:
!
interface Tunnel0
bandwidth 1536
ip address 10.62.1.10 255.255.255.0
tunnel source Serial0/0
tunnel mode gre multipoint
Reference:
http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/WAN_and_MAN/DMVPDG/DMVPN_2_Phase2.html
A
The configuration of mGRE allows a tunnel to have multiple destinations. The configuration of mGRE on one side of a tunnel does not have any relation to the tunnel properties that might exist at the exit points. This means that an mGRE tunnel on the hub may connect to a p2p tunnel on the branch. Conversely, a p2p
GRE tunnel may connect to an mGRE tunnel. The distinguishing feature between an mGRE interface and a p2p GRE interface is the tunnel destination. An mGRE interface does not have a configured destination. Instead the GRE tunnel is configured with the command tunnel mode gre multipoint. This command is used instead of the tunnel destination x.x.x.x found with p2p GRE tunnels. Besides allowing for multiple destinations, an mGRE tunnel requires NHRP to resolve the tunnel endpoints. Note, tunnel interfaces by default are point-to-point (p-p) using GRE encapsulation, effectively they have the tunnel mode gre command, which is not seen in the configuration because it is the default.
The mGRE configuration is as follows:
!
interface Tunnel0
bandwidth 1536
ip address 10.62.1.10 255.255.255.0
tunnel source Serial0/0
tunnel mode gre multipoint
Reference:
http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/WAN_and_MAN/DMVPDG/DMVPN_2_Phase2.html
send
light_mode
delete
Question #42
A network engineer executes the show crypto ipsec sa command. Which three pieces of information are displayed in the output? (Choose three.)
- Ainbound crypto map
- Bremaining key lifetime
- Cpath MTU
- Dtagged packets
- Euntagged packets
- Finvalid identity packets ABC
Correct Answer:
Explanation
show crypto ipsec sa
This command shows IPsec SAs built between peers. The encrypted tunnel is built between 12.1.1.1 and 12.1.1.2 for traffic that goes between networks 20.1.1.0 and 10.1.1.0. You can see the two Encapsulating Security Payload (ESP) SAs built inbound and outbound. Authentication Header (AH) is not used since there are no AH SAs.
This output shows an example of the show crypto ipsec sa command (bolded ones found in answers for this question). interface: FastEthernet0
Crypto map tag: test, local addr. 12.1.1.1
local ident (addr/mask/prot/port): (20.1.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0) current_peer: 12.1.1.2
PERMIT, flags={origin_is_acl,}
#pkts encaps: 7767918, #pkts encrypt: 7767918, #pkts digest 7767918
#pkts decaps: 7760382, #pkts decrypt: 7760382, #pkts verify 7760382
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0,
#pkts decompress failed: 0, #send errors 1, #Recv errors 0
local crypto endpt.: 12.1.1.1, remote crypto endpt.: 12.1.1.2 path mtu 1500, media mtu 1500 current outbound spi: 3D3 inbound esp sas: spi: 0x136A010F(325714191) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } slot: 0, conn id: 3442, flow_id: 1443, crypto map: test sa timing: remaining key lifetime (k/sec): (4608000/52)
IV size: 8 bytes -
replay detection support: Y
inbound ah sas:
inbound pcp sas:
inbound pcp sas:
outbound esp sas:
spi: 0x3D3(979)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 3443, flow_id: 1444, crypto map: test
sa timing: remaining key lifetime (k/sec): (4608000/52)
IV size: 8 bytes -
replay detection support: Y
outbound ah sas:
outbound pcp sas:
Reference:
http://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-negotiation-ike-protocols/5409-ipsec-debug-00.html
Explanation
show crypto ipsec sa
This command shows IPsec SAs built between peers. The encrypted tunnel is built between 12.1.1.1 and 12.1.1.2 for traffic that goes between networks 20.1.1.0 and 10.1.1.0. You can see the two Encapsulating Security Payload (ESP) SAs built inbound and outbound. Authentication Header (AH) is not used since there are no AH SAs.
This output shows an example of the show crypto ipsec sa command (bolded ones found in answers for this question). interface: FastEthernet0
Crypto map tag: test, local addr. 12.1.1.1
local ident (addr/mask/prot/port): (20.1.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0) current_peer: 12.1.1.2
PERMIT, flags={origin_is_acl,}
#pkts encaps: 7767918, #pkts encrypt: 7767918, #pkts digest 7767918
#pkts decaps: 7760382, #pkts decrypt: 7760382, #pkts verify 7760382
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0,
#pkts decompress failed: 0, #send errors 1, #Recv errors 0
local crypto endpt.: 12.1.1.1, remote crypto endpt.: 12.1.1.2 path mtu 1500, media mtu 1500 current outbound spi: 3D3 inbound esp sas: spi: 0x136A010F(325714191) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } slot: 0, conn id: 3442, flow_id: 1443, crypto map: test sa timing: remaining key lifetime (k/sec): (4608000/52)
IV size: 8 bytes -
replay detection support: Y
inbound ah sas:
inbound pcp sas:
inbound pcp sas:
outbound esp sas:
spi: 0x3D3(979)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 3443, flow_id: 1444, crypto map: test
sa timing: remaining key lifetime (k/sec): (4608000/52)
IV size: 8 bytes -
replay detection support: Y
outbound ah sas:
outbound pcp sas:
Reference:
http://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-negotiation-ike-protocols/5409-ipsec-debug-00.html
send
light_mode
delete
Question #43
Refer to the following output:
Router#show ip nhrp detail -
10.1.1.2/8 via 10.2.1.2, Tunnel1 created 00:00:12, expire 01:59:47
TypE. Dynamic, Flags: authoritative unique nat registered used
NBMA address: 10.12.1.2 -
What does the authoritative flag mean in regards to the NHRP information?
Router#show ip nhrp detail -
10.1.1.2/8 via 10.2.1.2, Tunnel1 created 00:00:12, expire 01:59:47
TypE. Dynamic, Flags: authoritative unique nat registered used
NBMA address: 10.12.1.2 -
What does the authoritative flag mean in regards to the NHRP information?
- AIt was obtained directly from the next-hop server.
- BData packets are process switches for this mapping entry.
- CNHRP mapping is for networks that are local to this router.
- DThe mapping entry was created in response to an NHRP registration request.
- EThe NHRP mapping entry cannot be overwritten.
Correct Answer:
A
Show NHRP: Examples -
The following is sample output from the show ip nhrp command:
Router# show ip nhrp -
10.0.0.2 255.255.255.255, tunnel 100 created 0:00:43 expire 1:59:16
Type: dynamic Flags: authoritative
NBMA address: 10.1111.1111.1111.1111.1111.1111.1111.1111.1111.11
10.0.0.1 255.255.255.255, Tunnel0 created 0:10:03 expire 1:49:56
Type: static Flags: authoritative
NBMA address: 10.1.1.2 -
The fields in the sample display are as follows:
✑ The IP address and its network mask in the IP-to-NBMA address cache. The mask is always 255.255.255.255 because Cisco does not support aggregation of
NBMA information through NHRP.
✑ The interface type and number and how long ago it was created (hours:minutes:seconds).
✑ The time in which the positive and negative authoritative NBMA address will expire (hours:minutes:seconds). This value is based on the ip nhrp holdtime command.
✑ Type of interface:
"" dynamic "" NBMA address was obtained from the NHRP Request packet. "" static "" NBMA address was statically configured.
✑ Flags:
"" authoritative "" Indicates that the NHRP information was obtained from the Next Hop Server or router that maintains the NBMA-to-IP address mapping for a particular destination.
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipaddr_nhrp/configuration/xe-16/nhrp-xe-16-book/config-nhrp.html
A
Show NHRP: Examples -
The following is sample output from the show ip nhrp command:
Router# show ip nhrp -
10.0.0.2 255.255.255.255, tunnel 100 created 0:00:43 expire 1:59:16
Type: dynamic Flags: authoritative
NBMA address: 10.1111.1111.1111.1111.1111.1111.1111.1111.1111.11
10.0.0.1 255.255.255.255, Tunnel0 created 0:10:03 expire 1:49:56
Type: static Flags: authoritative
NBMA address: 10.1.1.2 -
The fields in the sample display are as follows:
✑ The IP address and its network mask in the IP-to-NBMA address cache. The mask is always 255.255.255.255 because Cisco does not support aggregation of
NBMA information through NHRP.
✑ The interface type and number and how long ago it was created (hours:minutes:seconds).
✑ The time in which the positive and negative authoritative NBMA address will expire (hours:minutes:seconds). This value is based on the ip nhrp holdtime command.
✑ Type of interface:
"" dynamic "" NBMA address was obtained from the NHRP Request packet. "" static "" NBMA address was statically configured.
✑ Flags:
"" authoritative "" Indicates that the NHRP information was obtained from the Next Hop Server or router that maintains the NBMA-to-IP address mapping for a particular destination.
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipaddr_nhrp/configuration/xe-16/nhrp-xe-16-book/config-nhrp.html
send
light_mode
delete
Question #44
Which common issue causes intermittent DMVPN tunnel flaps?
- Aa routing neighbor reachability issue
- Ba suboptimal routing table
- Cinterface bandwidth congestion
- Dthat the GRE tunnel to hub router is not encrypted
Correct Answer:
A
DMVPN Tunnel Flaps Intermittently
Problem -
DMVPN tunnel flaps intermittently.
Solution -
When DMVPN tunnels flap, check the neighborship between the routers as issues with neighborship formation between routers may cause the DMVPN tunnel to flap. In order to resolve this problem, make sure the neighborship between the routers is always up.
Reference:
http://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-negotiation-ike-protocols/29240-dcmvpn.html#Prblm1
A
DMVPN Tunnel Flaps Intermittently
Problem -
DMVPN tunnel flaps intermittently.
Solution -
When DMVPN tunnels flap, check the neighborship between the routers as issues with neighborship formation between routers may cause the DMVPN tunnel to flap. In order to resolve this problem, make sure the neighborship between the routers is always up.
Reference:
http://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-negotiation-ike-protocols/29240-dcmvpn.html#Prblm1
send
light_mode
delete
Question #45
Which encapsulation supports an interface that is configured for an EVN trunk?
- A802.1Q
- BISL
- CPPP
- DFrame Relay
- EMPLS
- FHDLC A
Correct Answer:
Explanation
Restrictions for EVN -
✑ An EVN trunk is allowed on any interface that supports 802.1q encapsulation, such as Fast Ethernet, Gigabit Ethernet, and port channels.
✑ A single IP infrastructure can be virtualized to provide up to 32 virtual networks end-to-end.
✑ If an EVN trunk is configured on an interface, you cannot configure VRF-Lite on the same interface.
✑ OSPFv3 is not supported; OSPFv2 is supported.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/evn/configuration/xe-3s/evn-xe-3s-book/evn-overview.pdf
Explanation
Restrictions for EVN -
✑ An EVN trunk is allowed on any interface that supports 802.1q encapsulation, such as Fast Ethernet, Gigabit Ethernet, and port channels.
✑ A single IP infrastructure can be virtualized to provide up to 32 virtual networks end-to-end.
✑ If an EVN trunk is configured on an interface, you cannot configure VRF-Lite on the same interface.
✑ OSPFv3 is not supported; OSPFv2 is supported.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/evn/configuration/xe-3s/evn-xe-3s-book/evn-overview.pdf
send
light_mode
delete
Question #46
Which three characteristics are shared by subinterfaces and associated EVNs? (Choose three.)
- AIP address
- Brouting table
- Cforwarding table
- Daccess control lists
- ENetFlow configuration
Correct Answer:
ABC
A trunk interface can carry traffic for multiple EVNs. To simplify the configuration process, all the subinterfaces and associated EVNs have the same IP address assigned. In other words, the trunk interface is identified by the same IP address in different EVN contexts. This is accomplished as a result of each EVN having a unique routing and forwarding table, thereby enabling support for overlapping IP addresses across multiple EVNs.
Reference:
http://www.cisco.com/en/US/docs/ios-xml/ios/evn/configuration/xe-3sg/evn-overview.pdf
ABC
A trunk interface can carry traffic for multiple EVNs. To simplify the configuration process, all the subinterfaces and associated EVNs have the same IP address assigned. In other words, the trunk interface is identified by the same IP address in different EVN contexts. This is accomplished as a result of each EVN having a unique routing and forwarding table, thereby enabling support for overlapping IP addresses across multiple EVNs.
Reference:
http://www.cisco.com/en/US/docs/ios-xml/ios/evn/configuration/xe-3sg/evn-overview.pdf
send
light_mode
delete
Question #47
A user is having issues accessing file shares on a network. The network engineer advises the user to open a web browser, input a prescribed IP address, and follow the instructions. After doing this, the user is able to access company shares. Which type of remote access did the engineer enable?
- AEZVPN
- BIpsec VPN client access
- CVPDN client access
- DSSL VPN client access
Correct Answer:
D
The Cisco AnyConnect VPN Client provides secure SSL connections to the security appliance for remote users. Without a previously installed client, remote users enter the IP address in their browser of an interface configured to accept SSL VPN connections. Unless the security appliance is configured to redirect http:// requests to https://, users must enter the URL in the form https://<address>.
After entering the URL, the browser connects to that interface and displays the login screen. If the user satisfies the login and authentication, and the security appliance identifies the user as requiring the client, it downloads the client that matches the operating system of the remote computer. After downloading, the client installs and configures itself, establishes a secure SSL connection and either remains or uninstalls itself (depending on the security appliance configuration) when the connection terminates.
Reference:
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/100936-asa8x-split-tunnel-anyconnect-config.html
D
The Cisco AnyConnect VPN Client provides secure SSL connections to the security appliance for remote users. Without a previously installed client, remote users enter the IP address in their browser of an interface configured to accept SSL VPN connections. Unless the security appliance is configured to redirect http:// requests to https://, users must enter the URL in the form https://<address>.
After entering the URL, the browser connects to that interface and displays the login screen. If the user satisfies the login and authentication, and the security appliance identifies the user as requiring the client, it downloads the client that matches the operating system of the remote computer. After downloading, the client installs and configures itself, establishes a secure SSL connection and either remains or uninstalls itself (depending on the security appliance configuration) when the connection terminates.
Reference:
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/100936-asa8x-split-tunnel-anyconnect-config.html
send
light_mode
delete
Question #48
Which Cisco IOS VPN technology leverages Ipsec, mGRE, dynamic routing protocol, NHRP, and Cisco Express Forwarding?
- AFlexVPN
- BDMVPN
- CGETVPN
- DCisco Easy VPN
Correct Answer:
B
Dynamic Multipoint Virtual Private Network (DMVPN) is a dynamic tunneling form of a virtual private network (VPN) supported on Cisco IOS-based routers and
Unix-like Operating Systems based on the standard protocols, GRE, NHRP and Ipsec. This DMVPN provides the capability for creating a dynamic-mesh VPN network without having to pre-configure (static) all possible tunnel end-point peers, including Ipsec (Internet Protocol Security) and ISAKMP (Internet Security
Association and Key Management Protocol) peers. DMVPN is initially configured to build out a hub-and-spoke network by statically configuring the hubs (VPN headends) on the spokes, no change in the configuration on the hub is required to accept new spokes. Using this initial hub-and-spoke network, tunnels between spokes can be dynamically built on demand (dynamic-mesh) without additional configuration on the hubs or spokes. This dynamic-mesh capability alleviates the need for any load on the hub to route data between the spoke networks.
DMVPN is combination of the following technologies:
✑ Multipoint GRE (mGRE)
✑ Next-Hop Resolution Protocol (NHRP)
✑ Dynamic Routing Protocol (EIGRP, RIP, OSPF, BGP)
✑ Dynamic Ipsec encryption
✑ Cisco Express Forwarding (CEF)
Reference:
http://en.wikipedia.org/wiki/Dynamic_Multipoint_Virtual_Private_Network
B
Dynamic Multipoint Virtual Private Network (DMVPN) is a dynamic tunneling form of a virtual private network (VPN) supported on Cisco IOS-based routers and
Unix-like Operating Systems based on the standard protocols, GRE, NHRP and Ipsec. This DMVPN provides the capability for creating a dynamic-mesh VPN network without having to pre-configure (static) all possible tunnel end-point peers, including Ipsec (Internet Protocol Security) and ISAKMP (Internet Security
Association and Key Management Protocol) peers. DMVPN is initially configured to build out a hub-and-spoke network by statically configuring the hubs (VPN headends) on the spokes, no change in the configuration on the hub is required to accept new spokes. Using this initial hub-and-spoke network, tunnels between spokes can be dynamically built on demand (dynamic-mesh) without additional configuration on the hubs or spokes. This dynamic-mesh capability alleviates the need for any load on the hub to route data between the spoke networks.
DMVPN is combination of the following technologies:
✑ Multipoint GRE (mGRE)
✑ Next-Hop Resolution Protocol (NHRP)
✑ Dynamic Routing Protocol (EIGRP, RIP, OSPF, BGP)
✑ Dynamic Ipsec encryption
✑ Cisco Express Forwarding (CEF)
Reference:
http://en.wikipedia.org/wiki/Dynamic_Multipoint_Virtual_Private_Network
send
light_mode
delete
Question #49
Which traffic does the following configuration allow?
Ipv6 access-list cisco -
permit ipv6 host 2001:DB8:0:4::32 any eq ssh
line vty 0 4
ipv6 access-class cisco in
Ipv6 access-list cisco -
permit ipv6 host 2001:DB8:0:4::32 any eq ssh
line vty 0 4
ipv6 access-class cisco in
- Aall traffic to vty 0 4 from source 2001:DB8:0:4::32
- Bonly ssh traffic to vty 0 4 from source all
- Conly ssh traffic to vty 0 4 from source 2001:DB8:0:4::32
- Dall traffic to vty 0 4 from source all
Correct Answer:
C
Here we see that the Ipv6 access list called "cisco" is being applied to incoming VTY connections to the router. Ipv6 access list has just one entry, which allows only the single Ipv6 IP address of 2001:DB8:0:4::32 to connect using SSH only.
C
Here we see that the Ipv6 access list called "cisco" is being applied to incoming VTY connections to the router. Ipv6 access list has just one entry, which allows only the single Ipv6 IP address of 2001:DB8:0:4::32 to connect using SSH only.
send
light_mode
delete
Question #50
For troubleshooting purposes, which method can you use in combination with the "debug ip packet" command to limit the amount of output data?
- AYou can disable the IP route cache globally.
- BYou can use the KRON scheduler.
- CYou can use an extended access list.
- DYou can use an IOS parser.
- EYou can use the RITE traffic exporter.
Correct Answer:
C
The "debug ip packet" command generates a substantial amount of output and uses a substantial amount of system resources. This command should be used with caution in production networks. Always use with the access-list command to apply an extended ACL to the debug output.
Reference:
http://www.cisco.com/c/en/us/support/docs/security/dynamic-multipoint-vpn-dmvpn/111976-dmvpn-troubleshoot-00.html
C
The "debug ip packet" command generates a substantial amount of output and uses a substantial amount of system resources. This command should be used with caution in production networks. Always use with the access-list command to apply an extended ACL to the debug output.
Reference:
http://www.cisco.com/c/en/us/support/docs/security/dynamic-multipoint-vpn-dmvpn/111976-dmvpn-troubleshoot-00.html
send
light_mode
delete
All Pages
