Cisco® 300-101 Exam Practice Questions (P. 2)
- Full Access (1468 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
A network administrator uses IP SLA to measure UDP performance and notices that packets on one router have a higher one-way delay compared to the opposite direction. Which UDP characteristic does this scenario describe?
- Alatency
- Bstarvation
- Cconnectionless communication
- Dnonsequencing unordered packets
- Ejitter
Correct Answer:
A
Cisco IOS IP SLAs provides a proactive notification feature with an SNMP trap. Each measurement operation can monitor against a pre-set performance threshold. Cisco IOS IP SLAs generates an SNMP trap to alert management applications if this threshold is crossed. Several SNMP traps are available: round trip time, average jitter, one-way latency, jitter, packet loss, MOS, and connectivity tests.
Here is a partial sample output from the IP SLA statistics that can be seen: router#show ip sla statistics 1
Round Trip Time (RTT) for Index 55
Latest RTT: 1 ms -
Latest operation start time: *23:43:31.845 UTC Thu Feb 3 2005
Latest operation return code: OK
RTT Values:
Number Of RTT: 10 RTT Min/Avg/Max: 1/1/1 milliseconds
Latency one-way time:
Number of Latency one-way Samples: 0
Source to Destination Latency one way Min/Avg/Max: 0/0/0 milliseconds
Destination to Source Latency one way Min/Avg/Max: 0/0/0 milliseconds
Reference:
http://www.cisco.com/en/US/technologies/tk648/tk362/tk920/technologies_white_paper09186a00802d5efe.html
A
Cisco IOS IP SLAs provides a proactive notification feature with an SNMP trap. Each measurement operation can monitor against a pre-set performance threshold. Cisco IOS IP SLAs generates an SNMP trap to alert management applications if this threshold is crossed. Several SNMP traps are available: round trip time, average jitter, one-way latency, jitter, packet loss, MOS, and connectivity tests.
Here is a partial sample output from the IP SLA statistics that can be seen: router#show ip sla statistics 1
Round Trip Time (RTT) for Index 55
Latest RTT: 1 ms -
Latest operation start time: *23:43:31.845 UTC Thu Feb 3 2005
Latest operation return code: OK
RTT Values:
Number Of RTT: 10 RTT Min/Avg/Max: 1/1/1 milliseconds
Latency one-way time:
Number of Latency one-way Samples: 0
Source to Destination Latency one way Min/Avg/Max: 0/0/0 milliseconds
Destination to Source Latency one way Min/Avg/Max: 0/0/0 milliseconds
Reference:
http://www.cisco.com/en/US/technologies/tk648/tk362/tk920/technologies_white_paper09186a00802d5efe.html
send
light_mode
delete
Question #12
Under which condition does UDP dominance occur?
- Awhen TCP traffic is in the same class as UDP
- Bwhen UDP flows are assigned a lower priority queue
- Cwhen WRED is enabled
- Dwhen ACLs are in place to block TCP traffic
Correct Answer:
A
Mixing TCP with UDP -
It is a general best practice to not mix TCP-based traffic with UDP-based traffic (especially Streaming-Video) within a single service-provider class because of the behaviors of these protocols during periods of congestion. Specifically, TCP transmitters throttle back flows when drops are detected. Although some UDP applications have application-level windowing, flow control, and retransmission capabilities, most UDP transmitters are completely oblivious to drops and, thus, never lower transmission rates because of dropping.
When TCP flows are combined with UDP flows within a single service-provider class and the class experiences congestion, TCP flows continually lower their transmission rates, potentially giving up their bandwidth to UDP flows that are oblivious to drops. This effect is called TCP starvation/UDP dominance.
TCP starvation/UDP dominance likely occurs if (TCP-based) Mission-Critical Data is assigned to the same service-provider class as (UDP-based)
. Even if WRED is enabled on the service-provider class, the same behavior would be
Streaming-Video and the class experiences sustained congestion observed because WRED (for the most part) manages congestion only on TCP-based flows.
Reference:
http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/WAN_and_MAN/QoS_SRND/QoS-SRND-Book/VPNQoS.html
A
Mixing TCP with UDP -
It is a general best practice to not mix TCP-based traffic with UDP-based traffic (especially Streaming-Video) within a single service-provider class because of the behaviors of these protocols during periods of congestion. Specifically, TCP transmitters throttle back flows when drops are detected. Although some UDP applications have application-level windowing, flow control, and retransmission capabilities, most UDP transmitters are completely oblivious to drops and, thus, never lower transmission rates because of dropping.
When TCP flows are combined with UDP flows within a single service-provider class and the class experiences congestion, TCP flows continually lower their transmission rates, potentially giving up their bandwidth to UDP flows that are oblivious to drops. This effect is called TCP starvation/UDP dominance.
TCP starvation/UDP dominance likely occurs if (TCP-based) Mission-Critical Data is assigned to the same service-provider class as (UDP-based)
. Even if WRED is enabled on the service-provider class, the same behavior would be
Streaming-Video and the class experiences sustained congestion observed because WRED (for the most part) manages congestion only on TCP-based flows.
Reference:
http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/WAN_and_MAN/QoS_SRND/QoS-SRND-Book/VPNQoS.html
send
light_mode
delete
Question #13
Prior to enabling PPPoE in a virtual private dialup network group, which task must be completed?
- ADisable CDP on the interface.
- BExecute the vpdn enable command.
- CExecute the no switchport command.
- DEnable QoS FIFO for PPPoE support. B
Correct Answer:
Explanation
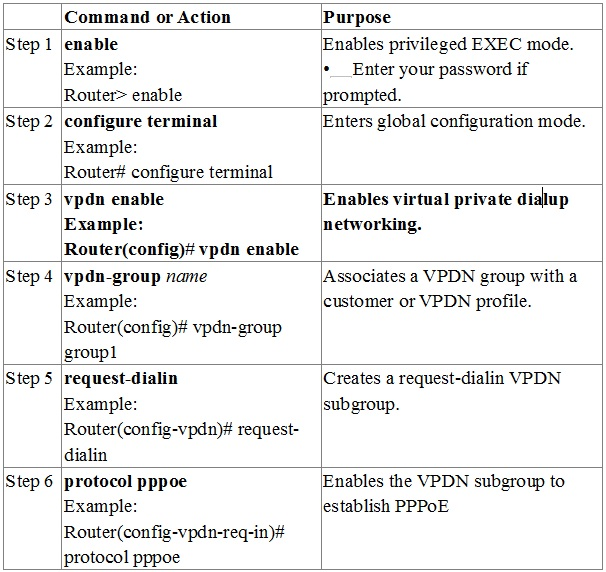
Enabling PPPoE in a VPDN Group -
Perform this task to enable PPPoE in a virtual private dial-up network (VPDN) group.
Restrictions -
This task applies only to releases prior to Cisco IOS Release 12.2(13)T.
SUMMARY STEPS -
1. enable
terminal
2. configure
3. vpdn enable
4. vpdn-group
5. request-dialin
6. protocol pppoe
DETAILED STEPS -
Reference:
http://www.cisco.com/en/US/docs/ios/12_2t/12_2t2/feature/guide/ftpppoec_support_TSD_Island_of_Content_Chapter.html
Explanation
Enabling PPPoE in a VPDN Group -
Perform this task to enable PPPoE in a virtual private dial-up network (VPDN) group.
Restrictions -
This task applies only to releases prior to Cisco IOS Release 12.2(13)T.
SUMMARY STEPS -
1. enable
terminal
2. configure
3. vpdn enable
4. vpdn-group
5. request-dialin
6. protocol pppoe
DETAILED STEPS -

Reference:
http://www.cisco.com/en/US/docs/ios/12_2t/12_2t2/feature/guide/ftpppoec_support_TSD_Island_of_Content_Chapter.html
send
light_mode
delete
Question #14
A network engineer has been asked to ensure that the PPPoE connection is established and authenticated using an encrypted password. Which technology, in combination with PPPoE, can be used for authentication in this manner?
- APAP
- Bdot1x
- CIpsec
- DCHAP
- EESP D
Correct Answer:
Explanation
With PPPoE, the two authentication options are PAP and CHAP. When CHAP is enabled on an interface and a remote device attempts to connect to it, the access server sends a CHAP packet to the remote device. The CHAP packet requests or "challenges" the remote device to respond. The challenge packet consists of an
ID, a random number, and the host name of the local router.
When the remote device receives the challenge packet, it concatenates the ID, the remote device's password, and the random number, and then encrypts all of it using the remote device's password. The remote device sends the results back to the access server, along with the name associated with the password used in the encryption process.
When the access server receives the response, it uses the name it received to retrieve a password stored in its user database. The retrieved password should be the same password the remote device used in its encryption process. The access server then encrypts the concatenated information with the newly retrieved password "" if the result matches the result sent in the response packet, authentication succeeds.
This prevents other devices -
The benefit of using CHAP authentication is that the remote device's password is never transmitted in clear text (encrypted). from stealing it and gaining illegal access to the ISP's network.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfathen.html
Explanation
With PPPoE, the two authentication options are PAP and CHAP. When CHAP is enabled on an interface and a remote device attempts to connect to it, the access server sends a CHAP packet to the remote device. The CHAP packet requests or "challenges" the remote device to respond. The challenge packet consists of an
ID, a random number, and the host name of the local router.
When the remote device receives the challenge packet, it concatenates the ID, the remote device's password, and the random number, and then encrypts all of it using the remote device's password. The remote device sends the results back to the access server, along with the name associated with the password used in the encryption process.
When the access server receives the response, it uses the name it received to retrieve a password stored in its user database. The retrieved password should be the same password the remote device used in its encryption process. The access server then encrypts the concatenated information with the newly retrieved password "" if the result matches the result sent in the response packet, authentication succeeds.
This prevents other devices -
The benefit of using CHAP authentication is that the remote device's password is never transmitted in clear text (encrypted). from stealing it and gaining illegal access to the ISP's network.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfathen.html
send
light_mode
delete
Question #15
A corporate policy requires PPPoE to be enabled and to maintain a connection with the ISP, even if no interesting traffic exists. Which feature can be used to accomplish this task?
- ATCP Adjust
- BDialer Persistent
- CPPPoE Groups
- Dhalf-bridging
- EPeer Neighbor Route
Correct Answer:
B
A new interface configuration command, dialer persistent, allows a dial-on-demand routing (DDR) dialer profile connection to be brought up without being traffic. When configured, the dialer persistent command starts a timer when the dialer interface starts up and starts the connection when the timer expires. If interesting traffic arrives before the timer expires, the connection is still brought up and set as persistent. The command provides a default timer interval, or you can set a custom timer interval.
To configure a dialer interface as persistent, use the following commands beginning in global configuration mode:
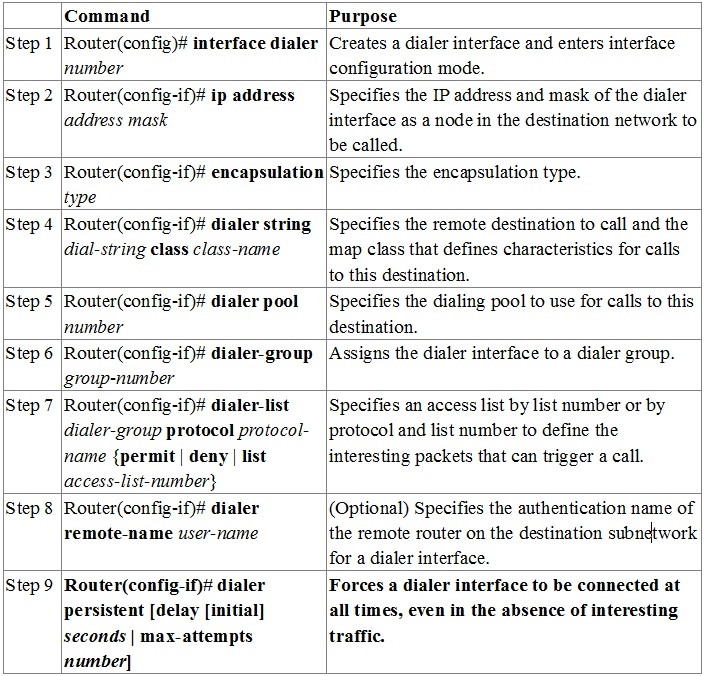
B
A new interface configuration command, dialer persistent, allows a dial-on-demand routing (DDR) dialer profile connection to be brought up without being traffic. When configured, the dialer persistent command starts a timer when the dialer interface starts up and starts the connection when the timer expires. If interesting traffic arrives before the timer expires, the connection is still brought up and set as persistent. The command provides a default timer interval, or you can set a custom timer interval.
To configure a dialer interface as persistent, use the following commands beginning in global configuration mode:

send
light_mode
delete
Question #16
Which PPP authentication method sends authentication information in clear text?
- AMS CHAP
- BCDPCP
- CCHAP
- DPAP
Correct Answer:
D
PAP authentication involves a two-way handshake where the username and password are sent across the link in clear text; hence, PAP authentication does not provide any protection against playback and line sniffing.
CHAP authentication, on the other hand, periodically verifies the identity of the remote node using a three-way handshake. After the PPP link is established, the host sends a "challenge" message to the remote node. The remote node responds with a value calc"lated usi"g a one-way hash function. The host checks the response against its own calculation of the expected hash value. If the values match, the authentication is acknowledged; otherwise, the connection is terminated.
Reference:
http://www.cisco.com/c/en/us/support/docs/wan/point-to-point-protocol-ppp/10241-ppp-callin-hostname.html
D
PAP authentication involves a two-way handshake where the username and password are sent across the link in clear text; hence, PAP authentication does not provide any protection against playback and line sniffing.
CHAP authentication, on the other hand, periodically verifies the identity of the remote node using a three-way handshake. After the PPP link is established, the host sends a "challenge" message to the remote node. The remote node responds with a value calc"lated usi"g a one-way hash function. The host checks the response against its own calculation of the expected hash value. If the values match, the authentication is acknowledged; otherwise, the connection is terminated.
Reference:
http://www.cisco.com/c/en/us/support/docs/wan/point-to-point-protocol-ppp/10241-ppp-callin-hostname.html
send
light_mode
delete
Question #17
Which protocol uses dynamic address mapping to request the next-hop protocol address for a specific connection?
- AFrame Relay inverse ARP
- Bstatic DLCI mapping
- CFrame Relay broadcast queue
- Ddynamic DLCI mapping
Correct Answer:
A
Dynamic address mapping uses Frame Relay Inverse ARP to request the next-hop protocol address for a specific connection, given its known DLCI. Responses to Inverse ARP requests are entered in an address-to-DLCI mapping table on the router or access server; the table is then used to supply the next-hop protocol address or the DLCI for outgoing traffic.
A
Dynamic address mapping uses Frame Relay Inverse ARP to request the next-hop protocol address for a specific connection, given its known DLCI. Responses to Inverse ARP requests are entered in an address-to-DLCI mapping table on the router or access server; the table is then used to supply the next-hop protocol address or the DLCI for outgoing traffic.
send
light_mode
delete
Question #18
Which statement is true about the PPP Session Phase of PPPoE?
- APPP options are negotiated and authentication is not performed. Once the link setup is completed, PPPoE functions as a Layer 3 encapsulation method that allows data to be transferred over the PPP link within PPPoE headers.
- BPPP options are not negotiated and authentication is performed. Once the link setup is completed, PPPoE functions as a Layer 4 encapsulation method that allows data to be transferred over the PPP link within PPPoE headers.
- CPPP options are automatically enabled and authorization is performed. Once the link setup is completed, PPPoE functions as a Layer 2 encapsulation method that allows data to be encrypted over the PPP link within PPPoE headers.
- DPPP options are negotiated and authentication is performed. Once the link setup is completed, PPPoE functions as a Layer 2 encapsulation method that allows data to be transferred over the PPP link within PPPoE headers.
Correct Answer:
D
PPPoE is composed of two main phases:
✑ Active Discovery Phase "" In this phase, the PPPoE client locates a PPPoE server, called an access concentrator. During this phase, a Session ID is assigned and the PPPoE layer is established.
✑ PPP Session Phase "" In this phase, PPP options are negotiated and authentication is performed. Once the link setup is completed, PPPoE functions as a Layer 2 encapsulation method, allowing data to be transferred over the PPP link within PPPoE headers.
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa92/configuration/vpn/asa-vpn-cli/vpn-pppoe.html
D
PPPoE is composed of two main phases:
✑ Active Discovery Phase "" In this phase, the PPPoE client locates a PPPoE server, called an access concentrator. During this phase, a Session ID is assigned and the PPPoE layer is established.
✑ PPP Session Phase "" In this phase, PPP options are negotiated and authentication is performed. Once the link setup is completed, PPPoE functions as a Layer 2 encapsulation method, allowing data to be transferred over the PPP link within PPPoE headers.
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa92/configuration/vpn/asa-vpn-cli/vpn-pppoe.html
send
light_mode
delete
Question #19
PPPoE is composed of which two phases?
- AActive Authentication Phase and PPP Session Phase
- BPassive Discovery Phase and PPP Session Phase
- CActive Authorization Phase and PPP Session Phase
- DActive Discovery Phase and PPP Session Phase
Correct Answer:
D
PPPoE is composed of two main phases:
✑ Active Discovery Phase "" In this phase, the PPPoE client locates a PPPoE server, called an access concentrator. During this phase, a Session ID is assigned and the PPPoE layer is established.
✑ PPP Session Phase "" In this phase, PPP options are negotiated and authentication is performed. Once the link setup is completed, PPPoE functions as a
Layer 2 encapsulation method, allowing data to be transferred over the PPP link within PPPoE headers.
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa92/configuration/vpn/asa-vpn-cli/vpn-pppoe.html
D
PPPoE is composed of two main phases:
✑ Active Discovery Phase "" In this phase, the PPPoE client locates a PPPoE server, called an access concentrator. During this phase, a Session ID is assigned and the PPPoE layer is established.
✑ PPP Session Phase "" In this phase, PPP options are negotiated and authentication is performed. Once the link setup is completed, PPPoE functions as a
Layer 2 encapsulation method, allowing data to be transferred over the PPP link within PPPoE headers.
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa92/configuration/vpn/asa-vpn-cli/vpn-pppoe.html
send
light_mode
delete
Question #20
Refer to the exhibit.
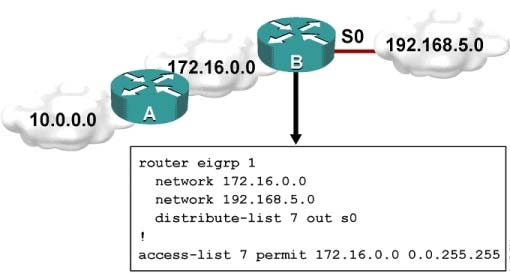
Which one statement is true?

Which one statement is true?
- ATraffic from the 172.16.0.0/16 network will be blocked by the ACL.
- BThe 10.0.0.0/8 network will not be advertised by Router B because the network statement for the 10.0.0.0/8 network is missing from Router B.
- CThe 10.0.0.0/8 network will not be in the routing table on Router B.
- DUsers on the 10.0.0.0/8 network can successfully ping users on the 192.168.5.0/24 network, but users on the 192.168.5.0/24 cannot successfully ping users on the 10.0.0.0/8 network.
- ERouter B will not advertise the 10.0.0.0/8 network because it is blocked by the ACL.
Correct Answer:
E
You can filter what individual routes are sent (out) or received (in) to any interface within your EIGRP configuration.
One example is noted above. If you filter outbound, the next neighbor(s) will not know about anything except the 172.16.0.0/16 route and therefore won't send it to anyone else downstream. If you filter inbound, YOU won't know about the route and therefore won't send it to anyone else downstream.
E
You can filter what individual routes are sent (out) or received (in) to any interface within your EIGRP configuration.
One example is noted above. If you filter outbound, the next neighbor(s) will not know about anything except the 172.16.0.0/16 route and therefore won't send it to anyone else downstream. If you filter inbound, YOU won't know about the route and therefore won't send it to anyone else downstream.
send
light_mode
delete
All Pages
