Cisco® 210-260 Exam Practice Questions (P. 5)
- Full Access (620 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
What command can you use to verify the binding table status?
- Ashow ip dhcp snooping database
- Bshow ip dhcp snooping binding
- Cshow ip dhcp snooping statistics
- Dshow ip dhcp pool
- Eshow ip dhcp source binding
- Fshow ip dhcp snooping
Correct Answer:
A
To retain the bindings across reloads, you must use the DHCP snooping database agent. Without this agent, the bindings established by DHCP snooping are lost upon reload, and connectivity is lost as well.
The database agent stores the bindings in a file at a configured location. Upon reload, the switch reads the file to build the database for the bindings. The switch keeps the file current by writing to the file as the database changes.
Reference:
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/snoodhcp.html#wp1090624
A
To retain the bindings across reloads, you must use the DHCP snooping database agent. Without this agent, the bindings established by DHCP snooping are lost upon reload, and connectivity is lost as well.
The database agent stores the bindings in a file at a configured location. Upon reload, the switch reads the file to build the database for the bindings. The switch keeps the file current by writing to the file as the database changes.
Reference:
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/snoodhcp.html#wp1090624
send
light_mode
delete
Question #42
If a switch receives a superior BPDU and goes directly into a blocked state, what mechanism must be in use?
- Aroot guard
- BEtherChannel guard
- Cloop guard
- DBPDU guard
Correct Answer:
A
The root guard feature protects the network against such issues.
The configuration of root guard is on a per-port basis. Root guard does not allow the port to become an STP root port, so the port is always STP-designated. If a better BPDU arrives on this port, root guard does not take the BPDU into account and elect a new STP root. Instead, root guard puts the port into the root- inconsistent STP state. You must enable root guard on all ports where the root bridge should not appear. In a way, you can configure a perimeter around the part of the network where the STP root is able to be located.
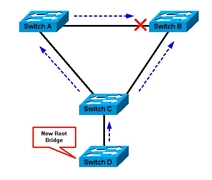
In the following figure, enable root guard on the Switch C port that connects to Switch D.
Switch C in figure below blocks the port that connects to Switch D, after the switch receives a superior BPDU. Root guard puts the port in the root-inconsistent
STP state. No traffic passes through the port in this state. After device D ceases to send superior BPDUs, the port is unblocked again. Via STP, the port goes from the listening state to the learning state, and eventually transitions to the forwarding state. Recovery is automatic; no human intervention is necessary.
This message appears after root guard blocks a port:
%SPANTREE-2-ROOTGUARDBLOCK: Port 1/1 tried to become non-designated in VLAN 77.
Moved to root-inconsistent state
Reference:
http://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10588-74.html
A
The root guard feature protects the network against such issues.
The configuration of root guard is on a per-port basis. Root guard does not allow the port to become an STP root port, so the port is always STP-designated. If a better BPDU arrives on this port, root guard does not take the BPDU into account and elect a new STP root. Instead, root guard puts the port into the root- inconsistent STP state. You must enable root guard on all ports where the root bridge should not appear. In a way, you can configure a perimeter around the part of the network where the STP root is able to be located.
In the following figure, enable root guard on the Switch C port that connects to Switch D.
Switch C in figure below blocks the port that connects to Switch D, after the switch receives a superior BPDU. Root guard puts the port in the root-inconsistent
STP state. No traffic passes through the port in this state. After device D ceases to send superior BPDUs, the port is unblocked again. Via STP, the port goes from the listening state to the learning state, and eventually transitions to the forwarding state. Recovery is automatic; no human intervention is necessary.
This message appears after root guard blocks a port:
%SPANTREE-2-ROOTGUARDBLOCK: Port 1/1 tried to become non-designated in VLAN 77.
Moved to root-inconsistent state

Reference:
http://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10588-74.html
send
light_mode
delete
Question #43
Which statement about a PVLAN isolated port configured on a switch is true?
- AThe isolated port can communicate only with the promiscuous port.
- BThe isolated port can communicate with other isolated ports and the promiscuous port.
- CThe isolated port can communicate only with community ports.
- DThe isolated port can communicate only with other isolated ports.
Correct Answer:
A
A promiscuous port can communicate with all interfaces, including the isolated and community ports within a PVLAN.
Reference:
http://www.cisco.com/c/en/us/tech/lan-switching/private-vlans-pvlans-promiscuous-isolated-community/index.html
A
A promiscuous port can communicate with all interfaces, including the isolated and community ports within a PVLAN.
Reference:
http://www.cisco.com/c/en/us/tech/lan-switching/private-vlans-pvlans-promiscuous-isolated-community/index.html
send
light_mode
delete
Question #44
If you change the native VLAN on the trunk port to an unused VLAN, what happens if an attacker attempts a double-tagging attack?
- AThe trunk port would go into an error-disabled state.
- BA VLAN hopping attack would be successful.
- CA VLAN hopping attack would be prevented.
- DThe attacked VLAN will be pruned.
Correct Answer:
C
The key feature of a double tagging attack is exploiting the native VLAN. Since VLAN 1 is the default VLAN for access ports and the default native VLAN on trunks, its an easy target. The first countermeasure is to remove access ports from the default VLAN 1 since the attackers port must match that of the switchs native VLAN.
Reference:
https://www.nlogic.co/understanding-vlan-hopping-attacks/
C
The key feature of a double tagging attack is exploiting the native VLAN. Since VLAN 1 is the default VLAN for access ports and the default native VLAN on trunks, its an easy target. The first countermeasure is to remove access ports from the default VLAN 1 since the attackers port must match that of the switchs native VLAN.
Reference:
https://www.nlogic.co/understanding-vlan-hopping-attacks/
send
light_mode
delete
Question #45
What is a reason for an organization to deploy a personal firewall?
- ATo protect endpoints such as desktops from malicious activity.
- BTo protect one virtual network segment from another.
- CTo determine whether a host meets minimum security posture requirements.
- DTo create a separate, non-persistent virtual environment that can be destroyed after a session.
- ETo protect the network from DoS and syn-flood attacks.
Correct Answer:
A
The sole purpose of firewall is to protect endpoints (workstations, and other devices) from malicious activity and network connections with nefarious purposes.
Reference:
http://searchmidmarketsecurity.techtarget.com/definition/personal-firewall
A
The sole purpose of firewall is to protect endpoints (workstations, and other devices) from malicious activity and network connections with nefarious purposes.
Reference:
http://searchmidmarketsecurity.techtarget.com/definition/personal-firewall
send
light_mode
delete
Question #46
Which statement about personal firewalls is true?
- AThey can protect a system by denying probing requests.
- BThey are resilient against kernel attacks.
- CThey can protect email messages and private documents in a similar way to a VPN.
- DThey can protect the network against attacks.
Correct Answer:
A
Drop or ignore any probing requests sent to certain service ports on your system. This can mask the presence of the computer from the attacker who is fooled into thinking that no machine is there.
Reference:
https://www.polyu.edu.hk/~ags/itsnews0604/security.html
A
Drop or ignore any probing requests sent to certain service ports on your system. This can mask the presence of the computer from the attacker who is fooled into thinking that no machine is there.
Reference:
https://www.polyu.edu.hk/~ags/itsnews0604/security.html
send
light_mode
delete
Question #47
Refer to the exhibit.

What type of firewall would use the given configuration line?

What type of firewall would use the given configuration line?
- Aa stateful firewall
- Ba personal firewall
- Ca proxy firewall
- Dan application firewall
- Ea stateless firewall
Correct Answer:
A
stateful firewalls, a type of firewall that attempts to track the state of network connections when filtering packets. The stateful firewall's capabilities are somewhat of a cross between the functions of a packet filter and the additional application-level protocol intelligence of a proxy.
Reference:
http://www.informit.com/articles/article.aspx?p=373120
A
stateful firewalls, a type of firewall that attempts to track the state of network connections when filtering packets. The stateful firewall's capabilities are somewhat of a cross between the functions of a packet filter and the additional application-level protocol intelligence of a proxy.
Reference:
http://www.informit.com/articles/article.aspx?p=373120
send
light_mode
delete
Question #48
What is the only permitted operation for processing multicast traffic on zone-based firewalls?
- AOnly control plane policing can protect the control plane against multicast traffic.
- BStateful inspection of multicast traffic is supported only for the self-zone.
- CStateful inspection for multicast traffic is supported only between the self-zone and the internal zone.
- DStateful inspection of multicast traffic is supported only for the internal zone.
Correct Answer:
A
stateful inspection support for multicast traffic is not supported between any zones, including the self zone. Use Control Plane Policing for the protection of the control plane against multicast traffic.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_zbf/configuration/15-mt/sec-data-zbf-15-mt-book/sec-zone-pol-fw.html
A
stateful inspection support for multicast traffic is not supported between any zones, including the self zone. Use Control Plane Policing for the protection of the control plane against multicast traffic.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_zbf/configuration/15-mt/sec-data-zbf-15-mt-book/sec-zone-pol-fw.html
send
light_mode
delete
Question #49
How does a zone-based firewall implementation handle traffic between interfaces in the same zone?
- ATraffic between two interfaces in the same zone is allowed by default.
- BTraffic between interfaces in the same zone is blocked unless you configure the same-security permit command.
- CTraffic between interfaces in the same zone is always blocked.
- DTraffic between interfaces in the same zone is blocked unless you apply a service policy to the zone pair.
Correct Answer:
A
By default, the traffic between interfaces in the same zone is not subject to any policy and passes freely. Firewall zones are used for security features.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_zbf/configuration/15-mt/sec-data-zbf-15-mt-book/sec-zone-pol-fw.html
A
By default, the traffic between interfaces in the same zone is not subject to any policy and passes freely. Firewall zones are used for security features.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_zbf/configuration/15-mt/sec-data-zbf-15-mt-book/sec-zone-pol-fw.html
send
light_mode
delete
Question #50
Which two statements about Telnet access to the ASA are true? (Choose two).
- AYou may VPN to the lowest security interface to telnet to an inside interface.
- BYou must configure an AAA server to enable Telnet.
- CYou can access all interfaces on an ASA using Telnet.
- DYou must use the command virtual telnet to enable Telnet.
- EBest practice is to disable Telnet and use SSH.
Correct Answer:
AE
If SSH is not enabled, the Java applet uses Telnet. But as soon as the SSH service is enabled on the switch, the Java applet will stop using Telnet and use SSH instead.
Reference:
https://www.alliedtelesis.com/sites/default/files/alliedwareplus-best-practice-guide_reva.pdf
AE
If SSH is not enabled, the Java applet uses Telnet. But as soon as the SSH service is enabled on the switch, the Java applet will stop using Telnet and use SSH instead.
Reference:
https://www.alliedtelesis.com/sites/default/files/alliedwareplus-best-practice-guide_reva.pdf
send
light_mode
delete
All Pages
