Cisco® 210-260 Exam Practice Questions (P. 3)
- Full Access (620 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
What type of algorithm uses the same key to encrypt and decrypt data?
- Aa symmetric algorithm
- Ban asymmetric algorithm
- Ca Public Key Infrastructure algorithm
- Dan IP security algorithm
Correct Answer:
A
Symmetric encryption (or pre-shared key encryption) uses a single key to both encrypt and decrypt data. Both the sender and the receiver need the same key to communicate.
Reference:
https://www.digicert.com/ssl-cryptography.htm
A
Symmetric encryption (or pre-shared key encryption) uses a single key to both encrypt and decrypt data. Both the sender and the receiver need the same key to communicate.
Reference:
https://www.digicert.com/ssl-cryptography.htm
send
light_mode
delete
Question #22
Refer to the exhibit.
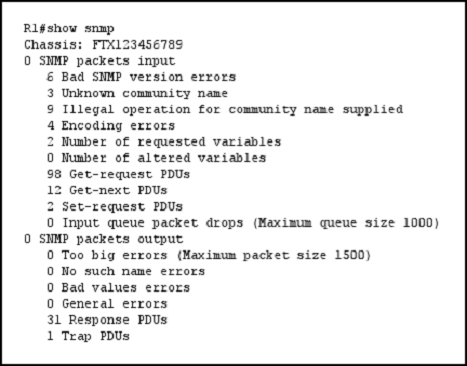
How many times was a read-only string used to attempt a write operation?

How many times was a read-only string used to attempt a write operation?
- A9
- B6
- C4
- D3
- E2
Correct Answer:
A
The read-only string attempted a write operation nine times as seen in the exhibit. It says, 9 illegal operations to community name supplied which means the read- only string attempted 9 write operations.
Reference:
http://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html
A
The read-only string attempted a write operation nine times as seen in the exhibit. It says, 9 illegal operations to community name supplied which means the read- only string attempted 9 write operations.
Reference:
http://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html
send
light_mode
delete
Question #23
Refer to the exhibit.
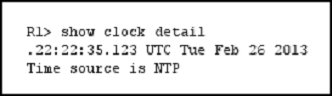
Which statement about the device time is true?

Which statement about the device time is true?
- AThe time is authoritative, but the NTP process has lost contact with its servers.
- BThe time is authoritative because the clock is in sync.
- CThe clock is out of sync.
- DNTP is configured incorrectly.
- EThe time is not authoritative.
Correct Answer:
A
The read-only string attempted a write operation nine times as seen in the exhibit. It says, 9 illegal operations to community name supplied which means the read- only string attempted 9 write operations.
Reference:
http://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html
A
The read-only string attempted a write operation nine times as seen in the exhibit. It says, 9 illegal operations to community name supplied which means the read- only string attempted 9 write operations.
Reference:
http://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html
send
light_mode
delete
Question #24
How does the Cisco ASA use Active Directory to authorize VPN users?
- AIt queries the Active Directory server for a specific attribute for the specified user.
- BIt sends the username and password to retrieve an ACCEPT or REJECT message from the Active Directory server.
- CIt downloads and stores the Active Directory database to query for future authorization requests.
- DIt redirects requests to the Active Directory server defined for the VPN group.
Correct Answer:
A
When user LDAP authentication for VPN access has succeeded, the ASA queries the LDAP server, which returns LDAP, attributes. These attributes generally include authorization data that applies to the VPN session. Thus, using LDAP accomplishes authentication and authorization in a single step.
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/access_aaa.html
A
When user LDAP authentication for VPN access has succeeded, the ASA queries the LDAP server, which returns LDAP, attributes. These attributes generally include authorization data that applies to the VPN session. Thus, using LDAP accomplishes authentication and authorization in a single step.
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/access_aaa.html
send
light_mode
delete
Question #25
Which statement about Cisco ACS authentication and authorization is true?
- AACS servers can be clustered to provide scalability.
- BACS can query multiple Active Directory domains.
- CACS uses TACACS to proxy other authentication servers.
- DACS can use only one authorization profile to allow or deny requests.
Correct Answer:
A
The ACS console server provides the scalability, reliability and security a company requires to control and manage servers and other networked devices.
Reference:
http://www.uk.insight.com/content/dam/insight/EMEA/uk/shop/emerson/advanced-console-server.pdf
(page 2)
A
The ACS console server provides the scalability, reliability and security a company requires to control and manage servers and other networked devices.
Reference:
http://www.uk.insight.com/content/dam/insight/EMEA/uk/shop/emerson/advanced-console-server.pdf
(page 2)
send
light_mode
delete
Question #26
Refer to the exhibit.
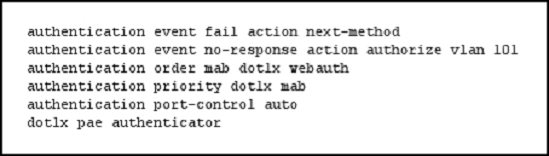
If a supplicant supplies incorrect credentials for all authentication methods configured on the switch, how will the switch respond?

If a supplicant supplies incorrect credentials for all authentication methods configured on the switch, how will the switch respond?
- AThe supplicant will fail to advance beyond the webauth method.
- BThe switch will cycle through the configured authentication methods indefinitely.
- CThe authentication attempt will time out and the switch will place the port into the unauthorized state.
- DThe authentication attempt will time out and the switch will place the port into VLAN 101.
Correct Answer:
A
Incorrect credentials supplied will result in failure to advance beyond webauth method. The authentication needs correct credentials as seen in the exhibit.
A
Incorrect credentials supplied will result in failure to advance beyond webauth method. The authentication needs correct credentials as seen in the exhibit.
send
light_mode
delete
Question #27
Which EAP method uses Protected Access Credentials?
- AEAP-FAST
- BEAP-TLS
- CEAP-PEAP
- DEAP-GTC
Correct Answer:
A
EAP-FAST is an EAP method that enables secure communication between a client and an authentication server by using Transport Layer Security (TLS) to establish a mutually authenticated tunnel. Within the tunnel, data in the form of type, length, and value (TLV) objects are used to send further authentication- related data between the client and the authentication server.
EAP-FAST supports the TLS extension as defined in RFC 4507 to support the fast re-establishment of the secure tunnel without having to maintain per-session state on the server. EAP-FAST-based mechanisms are defined to provision the credentials for the TLS extension. These credentials are called Protected Access
Credentials (PACs).
Reference:
http://www.cisco.com/c/en/us/td/docs/wireless/wlan_adapter/cb21ag/user/vista/1-0/configuration/guide/cb21ag10vistaconfigguide/eap_types.html
A
EAP-FAST is an EAP method that enables secure communication between a client and an authentication server by using Transport Layer Security (TLS) to establish a mutually authenticated tunnel. Within the tunnel, data in the form of type, length, and value (TLV) objects are used to send further authentication- related data between the client and the authentication server.
EAP-FAST supports the TLS extension as defined in RFC 4507 to support the fast re-establishment of the secure tunnel without having to maintain per-session state on the server. EAP-FAST-based mechanisms are defined to provision the credentials for the TLS extension. These credentials are called Protected Access
Credentials (PACs).
Reference:
http://www.cisco.com/c/en/us/td/docs/wireless/wlan_adapter/cb21ag/user/vista/1-0/configuration/guide/cb21ag10vistaconfigguide/eap_types.html
send
light_mode
delete
Question #28
What is one requirement for locking a wired or wireless device from ISE?
- AThe ISE agent must be installed on the device.
- BThe device must be connected to the network when the lock command is executed.
- CThe user must approve the locking action.
- DThe organization must implement an acceptable use policy allowing device locking.
Correct Answer:
A
To lock a wired or wireless device from ISE, you need to install ISE agent on that device first. The agent will assist in locking the device promptly.
A
To lock a wired or wireless device from ISE, you need to install ISE agent on that device first. The agent will assist in locking the device promptly.
send
light_mode
delete
Question #29
What VPN feature allows traffic to exit the security appliance through the same interface it entered?
- Ahairpinning
- BNAT
- CNAT traversal
- Dsplit tunneling
Correct Answer:
A
This feature is useful for VPN traffic that enters an interface, but is then routed out of that same interface. For example, if you have a hub-and-spoke VPN network where the security appliance is the hub and the remote VPN networks are spokes, in order for one spoke to communicate with another spoke traffic must go to the security appliance and then out again to the other spoke.
Enter the same-security-traffic command in order to allow traffic to enter and exit the same interface. ciscoasa(config)#same-security-traffic permit intra-interface
Reference:
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/100918-asa-sslvpn-00.html
A
This feature is useful for VPN traffic that enters an interface, but is then routed out of that same interface. For example, if you have a hub-and-spoke VPN network where the security appliance is the hub and the remote VPN networks are spokes, in order for one spoke to communicate with another spoke traffic must go to the security appliance and then out again to the other spoke.
Enter the same-security-traffic command in order to allow traffic to enter and exit the same interface. ciscoasa(config)#same-security-traffic permit intra-interface
Reference:
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/100918-asa-sslvpn-00.html
send
light_mode
delete
Question #30
What VPN feature allows Internet traffic and local LAN/WAN traffic to use the same network connection?
- Asplit tunneling
- Bhairpinning
- Ctunnel mode
- Dtransparent mode
Correct Answer:
A
When split tunneling is enabled, Internet traffic goes directly from your computer to the Internet and back without involving the VPN at all. Split tunneling also allows you to access other systems on your local network which is impossible if all traffic has go to the corporate network first, although this can be mitigated in some configurations.
Reference:
http://www.tripwire.com/state-of-security/security-data-protection/36th-article-vpn-split-tunneling/
A
When split tunneling is enabled, Internet traffic goes directly from your computer to the Internet and back without involving the VPN at all. Split tunneling also allows you to access other systems on your local network which is impossible if all traffic has go to the corporate network first, although this can be mitigated in some configurations.
Reference:
http://www.tripwire.com/state-of-security/security-data-protection/36th-article-vpn-split-tunneling/
send
light_mode
delete
All Pages
