Cisco® 200-201 Exam Practice Questions (P. 5)
- Full Access (462 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
How does a certificate authority impact security?
- AIt authenticates domain identity when requesting an SSL certificate.
- BIt validates client identity when communicating with the server.
- CIt authenticates client identity when requesting an SSL certificate.
- DIt validates the domain identity of the SSL certificate.
Correct Answer:
D
Reference:
https://en.wikipedia.org/wiki/Certificate_authority
D
Reference:
https://en.wikipedia.org/wiki/Certificate_authority
send
light_mode
delete
Question #42
Which data type is necessary to get information about source/destination ports?
- Astatistical data
- Bsession dataMost Voted
- Calert data
- Dconnectivity data
Correct Answer:
D
Reference:
https://community.cisco.com/t5/application-networking/difference-between-session-connections-socket/td-p/2417074
D
Reference:
https://community.cisco.com/t5/application-networking/difference-between-session-connections-socket/td-p/2417074
send
light_mode
delete
Question #43
Which event is a vishing attack?
- Aobtaining disposed documents from an organization
- Busing a vulnerability scanner on a corporate network
- Cimpersonating a tech support agent during a phone call
- Dsetting up a rogue access point near a public hotspot
Correct Answer:
C
Reference:
https://www.cisco.com/c/en/us/products/security/email-security/what-is-phishing.html#~types-of-phishing-attacks
C
Reference:
https://www.cisco.com/c/en/us/products/security/email-security/what-is-phishing.html#~types-of-phishing-attacks
send
light_mode
delete
Question #44
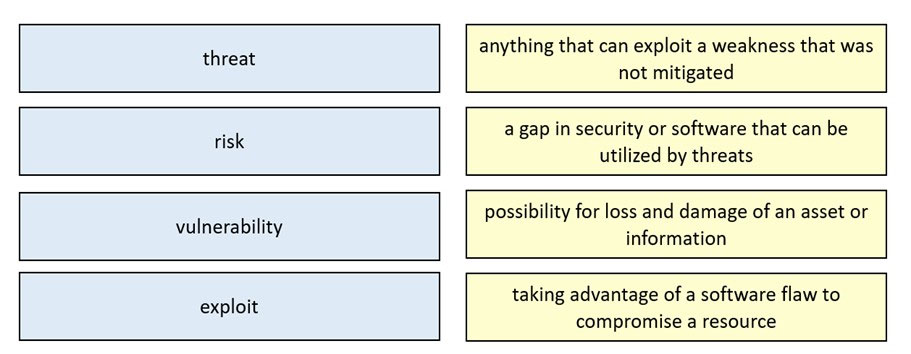
DRAG DROP -
Drag and drop the security concept from the left onto the example of that concept on the right.
Select and Place:
Drag and drop the security concept from the left onto the example of that concept on the right.
Select and Place:

send
light_mode
delete
Question #45
What is a difference between SIEM and SOAR?
- ASIEM predicts and prevents security alerts, while SOAR checks attack patterns and applies the mitigation.
- BSIEM's primary function is to collect and detect anomalies, while SOAR is more focused on security operations automation and response.
- CSOAR's primary function is to collect and detect anomalies, while SIEM is more focused on security operations automation and response.
- DSOAR predicts and prevents security alerts, while SIEM checks attack patterns and applies the mitigation.
Correct Answer:
B
Reference:
https://www.cisco.com/c/en/us/products/security/what-is-a-security-platform.html
B
Reference:
https://www.cisco.com/c/en/us/products/security/what-is-a-security-platform.html
send
light_mode
delete
Question #46
What is vulnerability management?
- AA process to identify and remediate existing weaknesses.
- BA process to recover from service interruptions and restore business-critical applications.
- CA security practice of performing actions rather than acknowledging the threats.
- DA security practice focused on clarifying and narrowing intrusion points.
Correct Answer:
A
Reference:
https://www.brinqa.com/vulnerability-management-primer-part-2-challenges/
A
Reference:
https://www.brinqa.com/vulnerability-management-primer-part-2-challenges/
send
light_mode
delete
Question #47
What is a difference between signature-based and behavior-based detection?
- ASignature-based identifies behaviors that may be linked to attacks, while behavior-based has a predefined set of rules to match before an alert.
- BBehavior-based identifies behaviors that may be linked to attacks, while signature-based has a predefined set of rules to match before an alert.Most Voted
- CBehavior-based uses a known vulnerability database, while signature-based intelligently summarizes existing data.
- DSignature-based uses a known vulnerability database, while behavior-based intelligently summarizes existing data.
Correct Answer:
D
Reference:
https://accedian.com/blog/what-is-the-difference-between-signature-based-and-behavior-based-ids/
D
Reference:
https://accedian.com/blog/what-is-the-difference-between-signature-based-and-behavior-based-ids/
send
light_mode
delete
Question #48
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
Which information is available on the server certificate?
- Aserver name, trusted subordinate CA, and private key
- Btrusted subordinate CA, public key, and cipher suites
- Ctrusted CA name, cipher suites, and private key
- Dserver name, trusted CA, and public keyMost Voted
Correct Answer:
D
D
send
light_mode
delete
Question #49
How does an SSL certificate impact security between the client and the server?
- Aby enabling an authenticated channel between the client and the server
- Bby creating an integrated channel between the client and the server
- Cby enabling an authorized channel between the client and the server
- Dby creating an encrypted channel between the client and the serverMost Voted
Correct Answer:
D
D
send
light_mode
delete
Question #50
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
- Aforgery attack
- Bplaintext-only attack
- Cciphertext-only attackMost Voted
- Dmeet-in-the-middle attack
Correct Answer:
C
C
send
light_mode
delete
All Pages