Cisco® 200-201 Exam Practice Questions (P. 4)
- Full Access (462 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
What specific type of analysis is assigning values to the scenario to see expected outcomes?
send
light_mode
delete
Question #32
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
send
light_mode
delete
Question #33
Why is encryption challenging to security monitoring?
- AEncryption analysis is used by attackers to monitor VPN tunnels.
- BEncryption is used by threat actors as a method of evasion and obfuscation.
- CEncryption introduces additional processing requirements by the CPU.
- DEncryption introduces larger packet sizes to analyze and store.
Correct Answer:
B
B
send
light_mode
delete
Question #34
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
- AThe threat actor used a dictionary-based password attack to obtain credentials.
- BThe threat actor gained access to the system by known credentials.Most Voted
- CThe threat actor used the teardrop technique to confuse and crash login services.
- DThe threat actor used an unknown vulnerability of the operating system that went undetected.
Correct Answer:
B
B
send
light_mode
delete
Question #35
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within
48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
- Acompany assets that are threatened
- Bcustomer assets that are threatened
- Cperpetrators of the attackMost Voted
- Dvictims of the attack
Correct Answer:
C
C
send
light_mode
delete
Question #36
What is the relationship between a vulnerability and a threat?
- AA threat exploits a vulnerabilityMost Voted
- BA vulnerability is a calculation of the potential loss caused by a threat
- CA vulnerability exploits a threat
- DA threat is a calculation of the potential loss caused by a vulnerability
Correct Answer:
A
A
send
light_mode
delete
Question #37
What is the principle of defense-in-depth?
- AAgentless and agent-based protection for security are used.
- BSeveral distinct protective layers are involved.Most Voted
- CAccess control models are involved.
- DAuthentication, authorization, and accounting mechanisms are used.
Correct Answer:
B
B
send
light_mode
delete
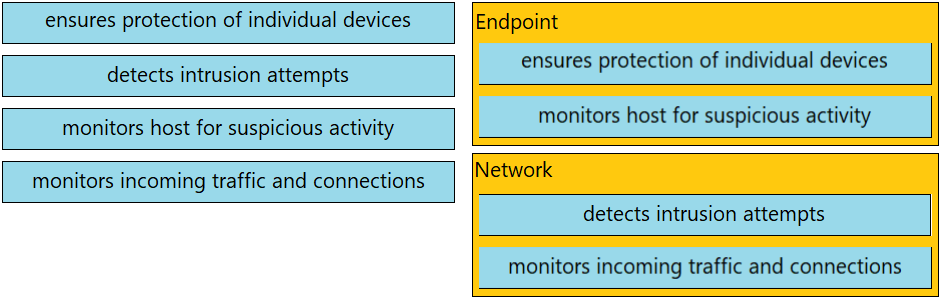
Question #38
DRAG DROP -
Drag and drop the uses on the left onto the type of security system on the right.
Select and Place:
Drag and drop the uses on the left onto the type of security system on the right.
Select and Place:

send
light_mode
delete
Question #39
What is the difference between the rule-based detection when compared to behavioral detection?
- ARule-Based detection is searching for patterns linked to specific types of attacks, while behavioral is identifying per signature.
- BRule-Based systems have established patterns that do not change with new data, while behavioral changes.
- CBehavioral systems are predefined patterns from hundreds of users, while Rule-Based only flags potentially abnormal patterns using signatures.Most Voted
- DBehavioral systems find sequences that match a particular attack signature, while Rule-Based identifies potential attacks.
Correct Answer:
D
D
send
light_mode
delete
Question #40
A security incident occurred with the potential of impacting business services. Who performs the attack?
- Athreat actor
- Bmalware author
- Cdirect competitor
- Dbug bounty hunter
Correct Answer:
A
Reference:
https://www.paubox.com/blog/what-is-threat-actor/#:~:text=The%20term%20threat%20actor%20refers,CTA)%20when%20referencing%
20cybersecurity%20issues
A
Reference:
https://www.paubox.com/blog/what-is-threat-actor/#:~:text=The%20term%20threat%20actor%20refers,CTA)%20when%20referencing%
20cybersecurity%20issues
send
light_mode
delete
All Pages