Snowflake SnowPro Advanced Architect Exam Practice Questions (P. 3)
- Full Access (152 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
A Data Engineer is designing a near real-time ingestion pipeline for a retail company to ingest event logs into Snowflake to derive insights. A Snowflake Architect is asked to define security best practices to configure access control privileges for the data load for auto-ingest to Snowpipe.
What are the MINIMUM object privileges required for the Snowpipe user to execute Snowpipe?
What are the MINIMUM object privileges required for the Snowpipe user to execute Snowpipe?
- AOWNERSHIP on the named pipe, USAGE on the named stage, target database, and schema, and INSERT and SELECT on the target table
- BOWNERSHIP on the named pipe, USAGE and READ on the named stage, USAGE on the target database and schema, and INSERT end SELECT on the target tableMost Voted
- CCREATE on the named pipe, USAGE and READ on the named stage, USAGE on the target database and schema, and INSERT end SELECT on the target table
- DUSAGE on the named pipe, named stage, target database, and schema, and INSERT and SELECT on the target table
send
light_mode
delete
Question #12
The IT Security team has identified that there is an ongoing credential stuffing attack on many of their organization’s system.
What is the BEST way to find recent and ongoing login attempts to Snowflake?
What is the BEST way to find recent and ongoing login attempts to Snowflake?
- ACall the LOGIN_HISTORY Information Schema table function.
- BQuery the LOGIN_HISTORY view in the ACCOUNT_USAGE schema in the SNOWFLAKE database.Most Voted
- CView the History tab in the Snowflake UI and set up a filter for SQL text that contains the text "LOGIN".
- DView the Users section in the Account tab in the Snowflake UI and review the last login column.
Correct Answer:
A
A
send
light_mode
delete
Question #13
An Architect has a VPN_ACCESS_LOGS table in the SECURITY_LOGS schema containing timestamps of the connection and disconnection, username of the user, and summary statistics.
What should the Architect do to enable the Snowflake search optimization service on this table?
What should the Architect do to enable the Snowflake search optimization service on this table?
- AAssume role with OWNERSHIP on future tables and ADD SEARCH OPTIMIZATION on the SECURITY_LOGS schema.
- BAssume role with ALL PRIVILEGES including ADD SEARCH OPTIMIZATION in the SECURITY LOGS schema.
- CAssume role with OWNERSHIP on VPN_ACCESS_LOGS and ADD SEARCH OPTIMIZATION in the SECURITY_LOGS schema.
- DAssume role with ALL PRIVILEGES on VPN_ACCESS_LOGS and ADD SEARCH OPTIMIZATION in the SECURITY_LOGS schema.
Correct Answer:
C
C
send
light_mode
delete
Question #14
The table contains five columns and it has millions of records. The cardinality distribution of the columns is shown below:
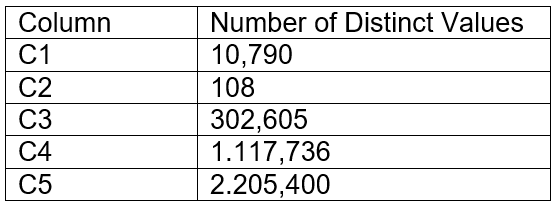
Column C4 and C5 are mostly used by SELECT queries in the GROUP BY and ORDER BY clauses. Whereas columns C1, C2 and C3 are heavily used in filter and join conditions of SELECT queries.
The Architect must design a clustering key for this table to improve the query performance.
Based on Snowflake recommendations, how should the clustering key columns be ordered while defining the multi-column clustering key?

Column C4 and C5 are mostly used by SELECT queries in the GROUP BY and ORDER BY clauses. Whereas columns C1, C2 and C3 are heavily used in filter and join conditions of SELECT queries.
The Architect must design a clustering key for this table to improve the query performance.
Based on Snowflake recommendations, how should the clustering key columns be ordered while defining the multi-column clustering key?
send
light_mode
delete
Question #15
Which security, governance, and data protection features require, at a MINIMUM, the Business Critical edition of Snowflake? (Choose two.)
- AExtended Time Travel (up to 90 days)
- BCustomer-managed encryption keys through Tri-Secret SecureMost Voted
- CPeriodic rekeying of encrypted data
- DAWS, Azure, or Google Cloud private connectivity to SnowflakeMost Voted
- EFederated authentication and SSO
Correct Answer:
BD
BD
send
light_mode
delete
All Pages
