Oracle 1z0-997-20 Exam Practice Questions (P. 1)
- Full Access (50 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
Which three scenarios are suitable for the use of Oracle Cloud Infrastructure (OCI) Autonomous Transaction Processing "" Serverless (ATP-S) deployment?
(Choose three.)
(Choose three.)
- AA manufacturing company is running Oracle E-Business Suite application on-premises. They are looking to move this application to OCI and they want to use a managed database offering for their database tier.
- BA midsize company is considering migrating its legacy on-premises MongoDB database to Oracle Cloud Infrastructure (OCI). The database has significantly higher workloads on weekends than weekdays.
- CA small startup is deploying a new application for eCommerce and it requires a database to store customers' transactions. The team is unsure of what the load will look like since it is a new application.Most Voted
- DA well-established, online auction marketplace is running an application where there is database usage 24x7, but also has peaks of activity that are hard to predict. When the peaks happen, the total activities may reach 3 times the normal activity level.Most Voted
- EA developer working on an internal project needs to use a database during work hours but doesn't need it during nights or weekends. The project budget requires her to keep costs low.Most Voted
Correct Answer:
ACE
Reference:
https://oracle.github.io/learning-library/oci-library/L100-LAB/ATP_Lab/ATP_HOL.html
ACE
Reference:
https://oracle.github.io/learning-library/oci-library/L100-LAB/ATP_Lab/ATP_HOL.html
send
light_mode
delete
Question #2
You are the Solution Architect that designed this Oracle Cloud Infrastructure (OCI) compartment layout for your organization:
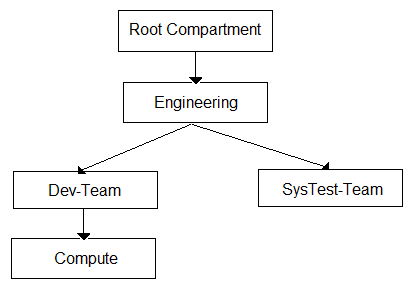
The development team has deployed quite a few instances under "˜Compute' Compartment and the operations team needs to list the instances under the same compartment for their testing. Both teams, development and operations are part of a group called "˜Eng-group'.
You have been looking for an option to allow the operations team to list the instances without access any confidential information or metadata of the resources.
Which IAM policy should you write based on these requirements? (Choose the best answer.)

The development team has deployed quite a few instances under "˜Compute' Compartment and the operations team needs to list the instances under the same compartment for their testing. Both teams, development and operations are part of a group called "˜Eng-group'.
You have been looking for an option to allow the operations team to list the instances without access any confidential information or metadata of the resources.
Which IAM policy should you write based on these requirements? (Choose the best answer.)
- AAllow group Eng-group to inspect instance-family in compartment Dev-Team:Compute and attach the policy to "˜SysTest-Team' Compartment.
- BAllow group Eng-group to read instance-family in compartment Dev-Team:Compute and attach the policy to "˜Dev-Team' Compartment.
- CAllow group Eng-group to inspect instance-family in compartment Dev-Team:Compute and attach the policy to "˜Engineering' Compartment.Most Voted
- DAllow group Eng-group to read instance-family in compartment Compute and attach the policy to "˜Engineering' Compartment.
Correct Answer:
C
C
send
light_mode
delete
Question #3
You are working for a Travel company and your travel portal application is a collection of microservices that run on Oracle Cloud Infrastructure Container Engine for Kubernetes. As per the recent security overview, you have noticed that Oracle has published a newer image of the Operating System used by the worker nodes. You want to make sure that your application doesn't face any downtime but at the same time the worker nodes gets upgraded to the latest version of the
Operating System.
What should you do to get this upgrade done without application downtime? (Choose the best answer.)
Operating System.
What should you do to get this upgrade done without application downtime? (Choose the best answer.)
- A1. Shutdown the worker nodes 2. Create a new node pool 3. Manually schedule the pods on the newly built node pool
- B1. Create a new node pool using the latest available Operating System image. 2. Run kubectl cordon <node name> against all the worker nodes in the old pool to stop any new application pods to get scheduled 3. Run kubectl drain <node name> """"delete""local""data """"force """"ignore""daemonsets to evict any Pods that are running 4. Delete the old node poolMost Voted
- C1. Create a new node pool using the latest available Operating System image 2. Run kubectl taint nodes """"all node""role.kubernetes.io/master"" 3. Delete the old node pool
- D1. Run kubectl cordon <node name> against all the worker nodes in the old pool to stop any new application pods to get scheduled 2. Run kubectl drain <node name> """"delete""local""data """"force """"ignore""daemonsets to evict any Pods that are running 3. Download the patches for the new Operating System image 4. Patch the worker nodes to the latest Operating System image
Correct Answer:
D
D
send
light_mode
delete
Question #4
You work for a large bank where security and compliance are critical. As part of the security overview meeting, your company decided to minimize the installation of local tools on your laptop. You have been running Ansible and kubectl to spin up Oracle Container Engine for Kubernetes (OKE) clusters and deployed your application.
For authentication, you are using an Oracle Cloud Infrastructure (OCI) CLI config file that contains OCIDs, Fingerprint, and a locally stored PEM file. Your security team doesn't want you to store any local API key and certificate, or any other local tools.
Which two actions should you perform to spin up the OKE cluster and interact with it? (Choose two.)
For authentication, you are using an Oracle Cloud Infrastructure (OCI) CLI config file that contains OCIDs, Fingerprint, and a locally stored PEM file. Your security team doesn't want you to store any local API key and certificate, or any other local tools.
Which two actions should you perform to spin up the OKE cluster and interact with it? (Choose two.)
- ACreate a developer workstation on OCI. Install Ansible and kubectl on it. Use resource principal to authenticate against OCI API and create the OKE Cluster.
- BDevelop your own code using OCI SDK to deploy the OKE cluster.
- CWork on OCI Cloud Shell to use built-in Ansible and kubectl to deploy the OKE cluster. Use OCI_CLI_AUTH=instance_obo_user environment variable to authenticate using built-in token.Most Voted
- DWork on OCI Cloud Shell to use built-in Ansible and kubectl to deploy the OKE cluster. Bring in your own config file and certificate to authenticate against OCI API.
- ECreate a developer workstation on OCI. Install Ansible and kubectl on it. Use instance principal to authenticate against OCI API and create the OKE Cluster.Most Voted
Correct Answer:
CE
Reference:
https://oracle-cloud-infrastructure-ansible-modules.readthedocs.io/en/latest/modules/oci_cluster_module.html
CE
Reference:
https://oracle-cloud-infrastructure-ansible-modules.readthedocs.io/en/latest/modules/oci_cluster_module.html
send
light_mode
delete
Question #5
A new international hacktivist group, based in London, launched wide scale cyber attacks including SQL Injection and Cross-Site Scripting (XSS) across multiple websites which are hosted in Oracle Cloud Infrastructure (OCI). As an IT consultant, you must configure a Web Application Firewall (WAF) to protect these websites against the attacks.
How should you configure your WAF to protect the website against those attacks? (Choose the best answer.)
How should you configure your WAF to protect the website against those attacks? (Choose the best answer.)
- AEnable a Protection Rule to block the attacks based on HTTP Headers that contain XSS and SQL strings.
- BEnable an Access Rule to block the IP Address range from London.
- CEnable a Protection Rule to block requests XSS Filters Categories and SQL Filters Categories.Most Voted
- DEnable a Protection Rule to block requests that came from London.
- EEnable an Access Rule that contains XSS Filters Categories and SQL Filters Categories.
Correct Answer:
C
Reference:
https://docs.cloud.oracle.com/en-us/iaas/Content/WAF/Reference/protectionruleids.htm
C
Reference:
https://docs.cloud.oracle.com/en-us/iaas/Content/WAF/Reference/protectionruleids.htm
send
light_mode
delete
All Pages
