Oracle 1z0-888 Exam Practice Questions (P. 1)
- Full Access (155 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
You have just executed a manual backup by using this command: mysqlbackup –u root –p –-socket=/tmp/my.sock –-backup-dir=/my/backup/ backup
The operation completed without error.
What is the state of this backup and operation required before it is ready to be restored?
The operation completed without error.
What is the state of this backup and operation required before it is ready to be restored?
- ABackup State = Compressed Backup
Operation = copy-back - BBackup State = Raw Backup -
Operation = apply-log - CBackup State = Prepared Backup -
Operation = validate - DBackup State = Prepared Backup -
Operation = apply-log - EBackup State = Raw Backup -
Operation = backupdir-to-image
Correct Answer:
E
E
send
light_mode
delete
Question #2
Which MySQL utility program should you use to process and sort the Slow Query Log based on query time or average query time?
send
light_mode
delete
Question #3
Consider:
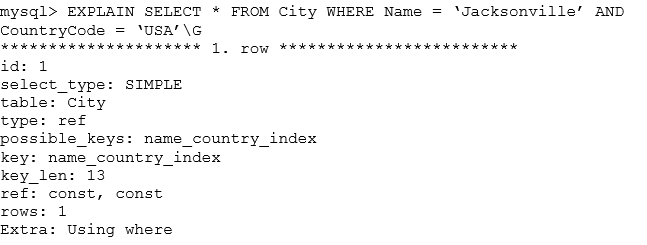
Which statement best describes the meaning of the value for the key_len column?

Which statement best describes the meaning of the value for the key_len column?
- AIt shows how many bytes will be used from each index row.
- BIt shows the number of characters indexed in the key.
- CIt shows the total size of the index row.
- DIt shows how many columns in the index are examined.
Correct Answer:
A
A
send
light_mode
delete
Question #4
Examine the mydata table and SELECT statements:
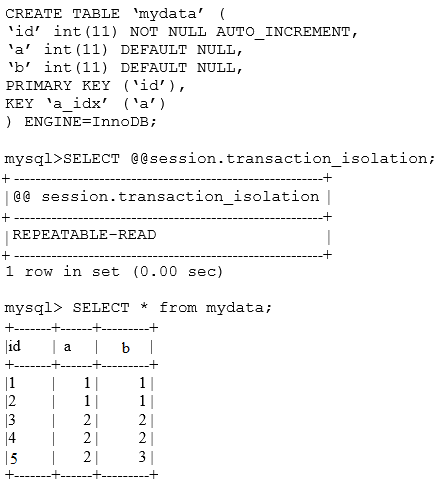
You issue:
mysql> begin;
mysql> update mydata set a=0 where b=3;
How many rows are now protected by locks with the default InnoDB configuration?

You issue:
mysql> begin;
mysql> update mydata set a=0 where b=3;
How many rows are now protected by locks with the default InnoDB configuration?
- Aone
- Bone row and a next-key lock for supremum
- Cone row and a gap-lock
- Dfive
Correct Answer:
D
D
send
light_mode
delete
Question #5
A particular government’s security policy is to have very strict data encryption and safety settings. This is done by restricting access based on their own CA authority and limiting access to particular users within a department. Which method could be used to restrict access as required?
- Ausing GRANT … REQUIRE X509 AND REQUIRE ISSUER ‘/C=…..’ AND REQUIRE SUBJECT ‘/C=…..’
- Busing GRANT USAGE, X509, …….ON *.* TO user@remotehost IDENTIFIED BY ‘secret_password’
- Cusing GRANT … REQUIRE SSL for a secure connection
- Dusing GRANT USAGE, SSL, …..ON *.* TO user@remotehost IDENTIFIED BY ‘secret_password’
Correct Answer:
A
A
send
light_mode
delete
All Pages
