Oracle 1z0-588 Exam Practice Questions (P. 5)
- Full Access (73 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
You decide to implement node type? for the Account dimension. What are the required steps that must be completed to implement a node type?
1. Under Administer, create node types with valid assigned DRM elements.
2. Create a hierarchy property that contains a list of values thatmatches the node types defined.
3. Create a local node property called "HierarchyNodeType".
4. For version, set the HierarchyNodeType to "Dimension".
5. For the hierarchy, set the Dimension property to the desired Node type value (for example. Account dimension type for the Account hierarchy).
6. Upload a glyph for each node type.
1. Under Administer, create node types with valid assigned DRM elements.
2. Create a hierarchy property that contains a list of values thatmatches the node types defined.
3. Create a local node property called "HierarchyNodeType".
4. For version, set the HierarchyNodeType to "Dimension".
5. For the hierarchy, set the Dimension property to the desired Node type value (for example. Account dimension type for the Account hierarchy).
6. Upload a glyph for each node type.
- A1, 2, 3, 5 only
- B1,3, 4, 5 only
- C1, 2, 3, 4, 5 only
- D1, 2, 3, 5, 6 only
- E1, 2, 3, 4, 5, 6
Correct Answer:
B
B
send
light_mode
delete
Question #22
Identify the two true statements about node access groups.
- ANode access groups use inheritance to assign the same access to descendants of a node but this inherited security may be overwritten at lower levels.
- BValid node access levels are Read, Edit,LimitedEdit, Insert, Inactivate, and Add.
- CAccess levels are assigned separately for leaf and limb nodes.
- DNode access groups can be used to filter the display of the hierarchy so that users only see the section of the hierarchy for which they have access.
- ENode access groups may be assigned by the Application Administrator or Access Manager.
Correct Answer:
BE
BE
send
light_mode
delete
Question #23
Identify the three true statements about External Connections.
- ADefined connections for FTP or UNC file path representing a target or source for an import/export.
- BThey allow you to have multiple exports or books target the same network folder or database, sothat, if the folder changes, you can just update the External Connection, rather than all the individual exports.
- COnly Administrators can configure or use External Connections.
- DPasswords will display for connections.
- EYou must explicitly choose the allowed tables for external database connections; this preventsusers from exporting to the incorrect table.
Correct Answer:
BCE
BCE
send
light_mode
delete
Question #24
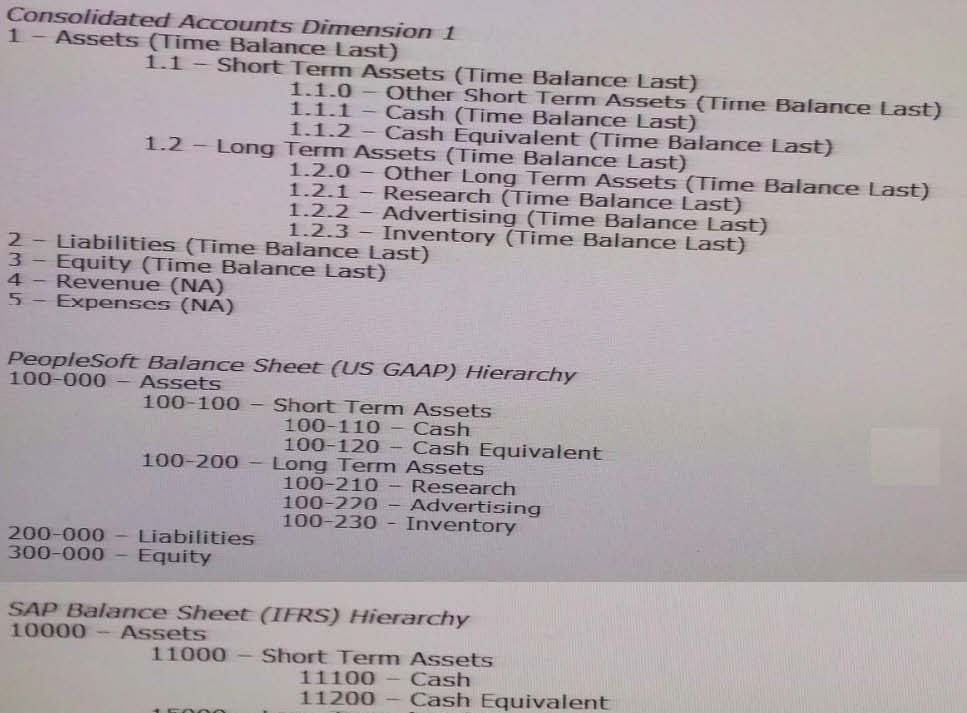
Your organization has two ERPs: PeopleSoft (PS) and SAP. Each ERP has its own chart of accounts. Each chart of accounts is mapped to a consolidated chart of accounts.
The Finance department maintains the consolidated account hierarchy.
Identify the steps in the correct order to manage the mapping of the local chart of accounts in the consolidated chart of accountsstructure using DRM hierarchies.
1. Build the consolidated chart of accounts hierarchy.
2. Build the PeopleSoft and SAP chart of accounts hierarchies.
3. Create a property category called CoA Map with two property definitions: PS CoA Mapping and SAP CoA Mapping.
4. Create an alternate Market hierarchy with limb nodes "large", "Medium", and "Small". Insert cities as leaf nodes under the appropriate Market Size nodes.
5. Use the Blend function to merge the PeopleSoft and sap chart of accounts to the correct consolidated account node In the consolidated hierarchy.
6. Drag and drop the PeopleSoft and SAP chart of accounts to the correct consolidated account in the consolidated hierarchy.
- A1, 2, 3, 4, 5, 6
- B3, 1, 2, 4, 6
- C3, 1, 2, 5, 6
- D1, 2, 4, 6
- E4, 3, 1, 2, 5, 6
Correct Answer:
C
C
send
light_mode
delete
Question #25
What are the four valid functions available in the DRM Migration utility?
- AExtract hierarchies and property values from one DRM version.
- BExtract property definitions, property categories, validations, and queries from a DRM application to an XML file.
- CLoad hierarchies and property values to a DRM version.
- DLoad metadata from an XML file into a Data Relationship Management application.
- ECompare metadata differences between two sources, such as a development DRM instance to a production DRM instance.
- FGenerate an HTML report from the results.
Correct Answer:
BCEF
BCEF
send
light_mode
delete
All Pages
