Oracle 1z0-060 Exam Practice Questions (P. 4)
- Full Access (209 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
The tnsnames.ora file has an entry for the service alias ORCL as follows:
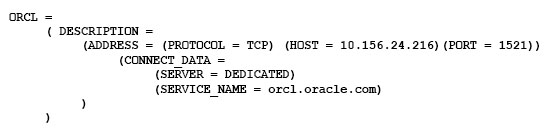
The TNSPING command executes successfully when tested with ORCL; however, from the same OS user session, you are not able to connect to the database instance with the following command:
SQL > CONNECT scott/tiger@orcl -
What could be the reason for this?

The TNSPING command executes successfully when tested with ORCL; however, from the same OS user session, you are not able to connect to the database instance with the following command:
SQL > CONNECT scott/tiger@orcl -
What could be the reason for this?
- AThe listener is not running on the database node.
- BThe TNS_ADMIN environment variable is set to the wrong value.
- CThe orcl.oracle.com database service is not registered with the listener.
- DThe DEFAULT_DOMAIN parameter is set to the wrong value in the sqlnet.ora file.
- EThe listener is running on a different port.
Correct Answer:
C
Service registration enables the listener to determine whether a database service and its service handlers are available. A service handler is a dedicated server process or dispatcher that acts as a connection point to a database. During registration, the LREG process provides the listener with the instance name, database service names, and the type and addresses of service handlers. This information enables the listener to start a service handler when a client request arrives.
C
Service registration enables the listener to determine whether a database service and its service handlers are available. A service handler is a dedicated server process or dispatcher that acts as a connection point to a database. During registration, the LREG process provides the listener with the instance name, database service names, and the type and addresses of service handlers. This information enables the listener to start a service handler when a client request arrives.
send
light_mode
delete
Question #17
Examine the following steps of privilege analysis for checking and revoking excessive, unused privileges granted to users:
1. Create a policy to capture the privilege used by a user for privilege analysis.
2. Generate a report with the data captured for a specified privilege capture.
3. Start analyzing the data captured by the policy.
4. Revoke the unused privileges.
5. Compare the used and unused privileges lists.
6. Stop analyzing the data.
Identify the correct sequence of steps.
1. Create a policy to capture the privilege used by a user for privilege analysis.
2. Generate a report with the data captured for a specified privilege capture.
3. Start analyzing the data captured by the policy.
4. Revoke the unused privileges.
5. Compare the used and unused privileges lists.
6. Stop analyzing the data.
Identify the correct sequence of steps.
- A1, 3, 5, 6, 2, 4
- B1, 3, 6, 2, 5, 4
- C1, 3, 2, 5, 6, 4
- D1, 3, 2, 5, 6, 4
- E1, 3, 5, 2, 6, 4
Correct Answer:
B
1. Create a policy to capture the privilege used by a user for privilege analysis.
3. Start analyzing the data captured by the policy.
6. Stop analyzing the data.
2. Generate a report with the data captured for a specified privilege capture.
5. Compare the used and unused privileges lists.
4. Revoke the unused privileges.
B
1. Create a policy to capture the privilege used by a user for privilege analysis.
3. Start analyzing the data captured by the policy.
6. Stop analyzing the data.
2. Generate a report with the data captured for a specified privilege capture.
5. Compare the used and unused privileges lists.
4. Revoke the unused privileges.
send
light_mode
delete
Question #18
Your database is running an ARCHIVELOG mode.
The following parameters are set in your database instance:
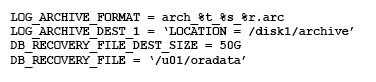
Which statement is true about the archived redo log files?
The following parameters are set in your database instance:

Which statement is true about the archived redo log files?
- AThey are created only in the location specified by the LOG_ARCHIVE_DEST_1 parameter.
- BThey are created only in the Fast Recovery Area because configuring the DB_RECOVERY_FILE_DEST and DB_RECOVERY_FILE_DEST_SIZE parameters automatically enables flashback for the database.
- CThey are created in the location specified by the LOG_ARCHIVE_DEST_1 parameter and in the default location $ORACLE_HOME/dbs/arch.
- DThey are created in the location specified by the LOG_ARCHIVE_DEST_1 parameter and in the location specified by the DB_RECOVERY_FILE_DEST
Correct Answer:
A
You can choose to archive redo logs to a single destination or to multiple destinations.
Destinations can be localwithin the local file system or an Oracle Automatic Storage Management (Oracle ASM) disk groupor remote (on a standby database).
When you archive to multiple destinations, a copy of each filled redo log file is written to each destination. These redundant copies help ensure that archived logs are always available in the event of a failure at one of the destinations.
To archive to only a single destination, specify that destination using the LOG_ARCHIVE_DEST and LOG_ARCHIVE_DUPLEX_DEST initialization parameters.
ARCHIVE_DEST initialization parameter. To archive to multiple destinations, you can choose to archive to two or more locations using the
LOG_ARCHIVE_DEST_n initialization parameters, or to archive only to a primary and secondary destination using the LOG_ARCHIVE_DEST and
LOG_ARCHIVE_DUPLEX_DEST initialization parameters.
A
You can choose to archive redo logs to a single destination or to multiple destinations.
Destinations can be localwithin the local file system or an Oracle Automatic Storage Management (Oracle ASM) disk groupor remote (on a standby database).
When you archive to multiple destinations, a copy of each filled redo log file is written to each destination. These redundant copies help ensure that archived logs are always available in the event of a failure at one of the destinations.
To archive to only a single destination, specify that destination using the LOG_ARCHIVE_DEST and LOG_ARCHIVE_DUPLEX_DEST initialization parameters.
ARCHIVE_DEST initialization parameter. To archive to multiple destinations, you can choose to archive to two or more locations using the
LOG_ARCHIVE_DEST_n initialization parameters, or to archive only to a primary and secondary destination using the LOG_ARCHIVE_DEST and
LOG_ARCHIVE_DUPLEX_DEST initialization parameters.
send
light_mode
delete
Question #19
Your multitenant container database (CDB) is running in ARCHIVELOG mode. You connect to the CDB RMAN.
Examine the following command and its output:

You execute the following command:
RMAN > BACKUP DATABASE PLUS ARCHIVELOG;
Which data files will be backed up?
Examine the following command and its output:

You execute the following command:
RMAN > BACKUP DATABASE PLUS ARCHIVELOG;
Which data files will be backed up?
- AData files that belong to only the root container
- BData files that belong to the root container and all the pluggable databases (PDBs)
- CData files that belong to only the root container and PDB$SEED
- DData files that belong to the root container and all the PDBs excluding PDB$SEED
Correct Answer:
B
Backing Up a Whole CDB -
Backing up a whole CDB is similar to backing up a non-CDB. When you back up a whole CDB, RMAN backs up the root, all the PDBs, and the archived redo logs.
You can then recover either the whole CDB, the root only, or one or more PDBs from the CDB backup.
Note:
* You can back up and recover a whole CDB, the root only, or one or more PDBs.
* Backing Up Archived Redo Logs with RMAN
Archived redo logs are the key to successful media recovery. Back them up regularly. You can back up logs with BACKUP ARCHIVELOG, or back up logs while backing up datafiles and control files by specifying BACKUP ... PLUS ARCHIVELOG.
B
Backing Up a Whole CDB -
Backing up a whole CDB is similar to backing up a non-CDB. When you back up a whole CDB, RMAN backs up the root, all the PDBs, and the archived redo logs.
You can then recover either the whole CDB, the root only, or one or more PDBs from the CDB backup.
Note:
* You can back up and recover a whole CDB, the root only, or one or more PDBs.
* Backing Up Archived Redo Logs with RMAN
Archived redo logs are the key to successful media recovery. Back them up regularly. You can back up logs with BACKUP ARCHIVELOG, or back up logs while backing up datafiles and control files by specifying BACKUP ... PLUS ARCHIVELOG.
send
light_mode
delete
Question #20
You are administering a database stored in Automatic Storage management (ASM). The files are stored in the DATA disk group. You execute the following command:
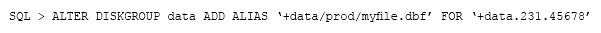
What is the result?

What is the result?
- AThe file ‘+data.231.45678’ is physically relocated to ‘+data/prod’ and renamed as ‘myfile.dbf’.
- BThe file ‘+data.231.45678’ is renamed as ‘myfile.dbf’, and copied to ‘+data/prod’.
- CThe file ‘+data.231.45678’ remains in the same location and a synonym 'myfile.dbf' is created.
- DThe file ‘myfile.dbf’ is created in ‘+data/prod’ and the reference to ‘+data.231.45678’ in the data dictionary removed.
Correct Answer:
C
ADD ALIAS -
Use this clause to create an alias name for an Oracle ASM filename. The alias_name consists of the full directory path and the alias itself.
C
ADD ALIAS -
Use this clause to create an alias name for an Oracle ASM filename. The alias_name consists of the full directory path and the alias itself.
send
light_mode
delete
All Pages
