Oracle 1z0-034 Exam Practice Questions (P. 3)
- Full Access (148 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
You are managing a 24*7 database. The backup strategy for the database is to perform user-managedbackups.
Identify two prerequisites to perform the backups. (Choose two.)
Identify two prerequisites to perform the backups. (Choose two.)
- AThe database must be opened in restricted mode.
- BThe database must be configured to run in ARCHIVELOG mode.
- CThe tablespaces are required to be in backup mode before taking the backup.
- DThe tablespaces are required to be in read-only mode before taking the backup
Correct Answer:
BC
BC
send
light_mode
delete
Question #12
You need to configure fine-grained access control to external network resources from within your database. You create an access control list (ACL) using the
DBMS_NETWORK_ACL_ADMIN package.
Which statement is true regarding the ACL created?
DBMS_NETWORK_ACL_ADMIN package.
Which statement is true regarding the ACL created?
- AIt is a list of remote database links stored in the XML file that are available to the users of the database.
- BIt is a list of users and network privileges stored in the XML file according to which a group of users canconnect to one or more hosts.
- CIt is a list of users and network privileges stored in the data dictionary according to which a group of userscan connect to one or more hosts.
- DIt is the list of the host names or the IP addresses stored in the data dictionary that can connect to yourdatabase through PL/SQL network utility packages such
Correct Answer:
B
The DBMS_NETWORK_ACL_ADMIN package provides the interface to administer the network Access ControlList (ACL).
Refer to here for About Fin-Grained Access to External Network ServicesConfiguring fine-grained access control for users and roles that need to access external network services fromthe database. This way, specific groups of users can connect to one or more host computers, based onprivileges that you grant them.
Typically, you use this feature to control access to applications that run onspecific host addresses.
To configure fine-grained access control to external network services, you create an access control list (ACL),which is stored in Oracle XML DB. You can create the access control list by using Oracle XML DB itself, orby using the DBMS_NETWORK_ACL_ADMIN and DBMS_NETWORK_ACL_UTILITY PL/SQL packages.
This guideexplains how to use these packages to create and manage the access control list. To create an access controllist by using Oracle XML DB and for general conceptual information about access control lists, see Oracle XMLDB Developer's Guide.
B
The DBMS_NETWORK_ACL_ADMIN package provides the interface to administer the network Access ControlList (ACL).
Refer to here for About Fin-Grained Access to External Network ServicesConfiguring fine-grained access control for users and roles that need to access external network services fromthe database. This way, specific groups of users can connect to one or more host computers, based onprivileges that you grant them.
Typically, you use this feature to control access to applications that run onspecific host addresses.
To configure fine-grained access control to external network services, you create an access control list (ACL),which is stored in Oracle XML DB. You can create the access control list by using Oracle XML DB itself, orby using the DBMS_NETWORK_ACL_ADMIN and DBMS_NETWORK_ACL_UTILITY PL/SQL packages.
This guideexplains how to use these packages to create and manage the access control list. To create an access controllist by using Oracle XML DB and for general conceptual information about access control lists, see Oracle XMLDB Developer's Guide.
send
light_mode
delete
Question #13
View the Exhibit and examine the RMAN commands.
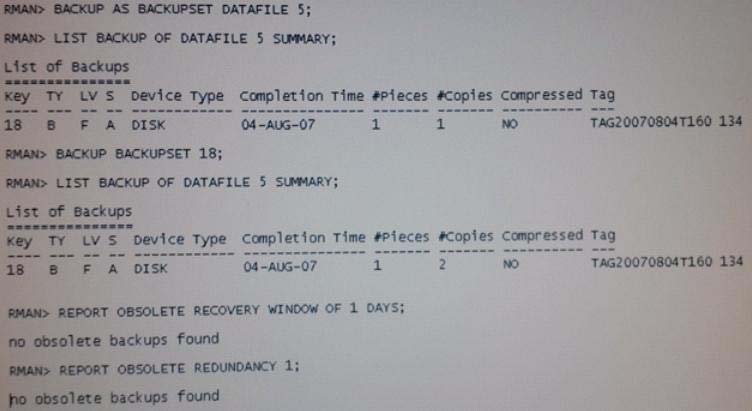
Which statement describes the effect of a backup retention policy on the backup of a backup set?

Which statement describes the effect of a backup retention policy on the backup of a backup set?
- AEither all the copies of a backup set are obsolete or none of them are as per the retention policy.
- BThe copies of the backup will be reported as obsolete under a redundancy-based backup retention policy.
- CThe copies of the backup will be reported as obsolete under a recovery window-based backup retentionpolicy.
- DAll the copies of the backup set are counted as one instance of a backup and will deleted in backup setexceeds the redundancy-based backup retention policy.
Correct Answer:
A
A
send
light_mode
delete
Question #14
Which four resources can directives be specified by using the Oracle Resource Manager?
- ACPU usage
- Bdegree of parallelism
- Cnumber of open cursors
- Dnumber of sorts performed
- Eidle time for blocking sessions
- Fnumber of I/Os requests
Correct Answer:
ABEF
ABEF
send
light_mode
delete
Question #15
You are using the control file to maintain information about the database backups that are being performed by Recovery Manager (RMAN).
Identify two scenarios in which you must have a recovery catalog.
Identify two scenarios in which you must have a recovery catalog.
- ATo store the backup information of multiple database
- BTo restrict the amount of space that is used by the backups
- CTo maintain a backup for a certain time is set by the CONTROL_FILE_RECORD_KEEP_TIME parameter.
- DTo list the data files that were in a target database at a given time by using the AT option of REPORTSCHEMA command.
Correct Answer:
AD
AD
send
light_mode
delete
All Pages
