Microsoft SC-900 Exam Practice Questions (P. 5)
- Full Access (220 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
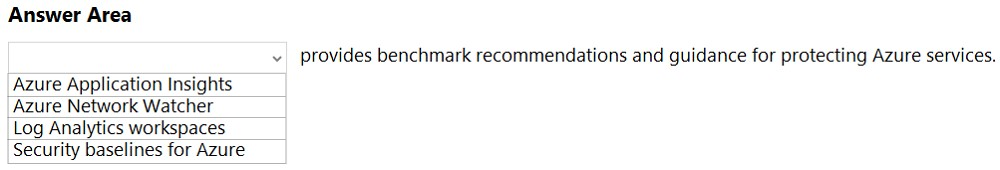
Select the answer that correctly completes the sentence.
Hot Area:

Correct Answer:
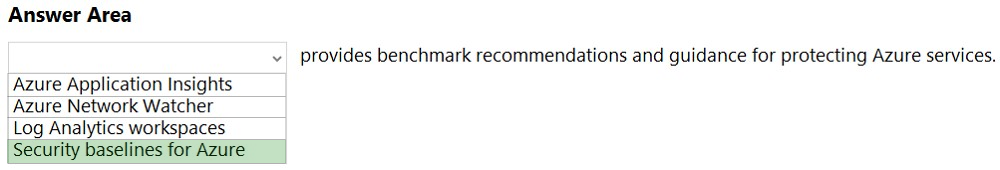
Reference:
https://docs.microsoft.com/en-us/security/benchmark/azure/baselines/cloud-services-security-baseline

Reference:
https://docs.microsoft.com/en-us/security/benchmark/azure/baselines/cloud-services-security-baseline
send
light_mode
delete
Question #22
What is an example of encryption at rest?
- Aencrypting communications by using a site-to-site VPN
- Bencrypting a virtual machine diskMost Voted
- Caccessing a website by using an encrypted HTTPS connection
- Dsending an encrypted email
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/encryption-atrest
B
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/encryption-atrest
send
light_mode
delete
Question #23
Which three statements accurately describe the guiding principles of Zero Trust? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
NOTE: Each correct selection is worth one point.
- ADefine the perimeter by physical locations.
- BUse identity as the primary security boundary.Most Voted
- CAlways verify the permissions of a user explicitly.Most Voted
- DAlways assume that the user system can be breached.Most Voted
- EUse the network as the primary security boundary.
Correct Answer:
BCD
Reference:
https://docs.microsoft.com/en-us/security/zero-trust/
BCD
Reference:
https://docs.microsoft.com/en-us/security/zero-trust/
send
light_mode
delete
Question #24
HOTSPOT -
Which service should you use to view your Azure secure score? To answer, select the appropriate service in the answer area.
Hot Area:
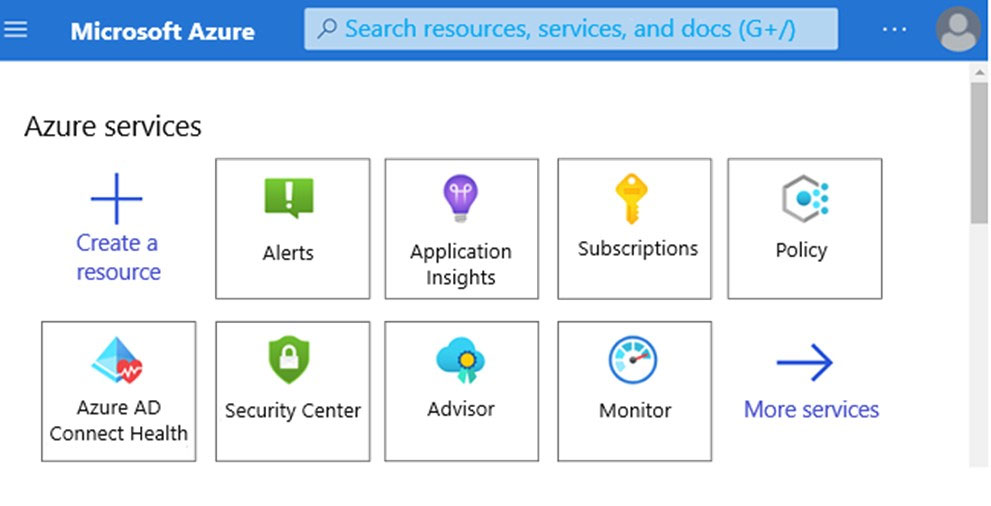
Which service should you use to view your Azure secure score? To answer, select the appropriate service in the answer area.
Hot Area:

Correct Answer:
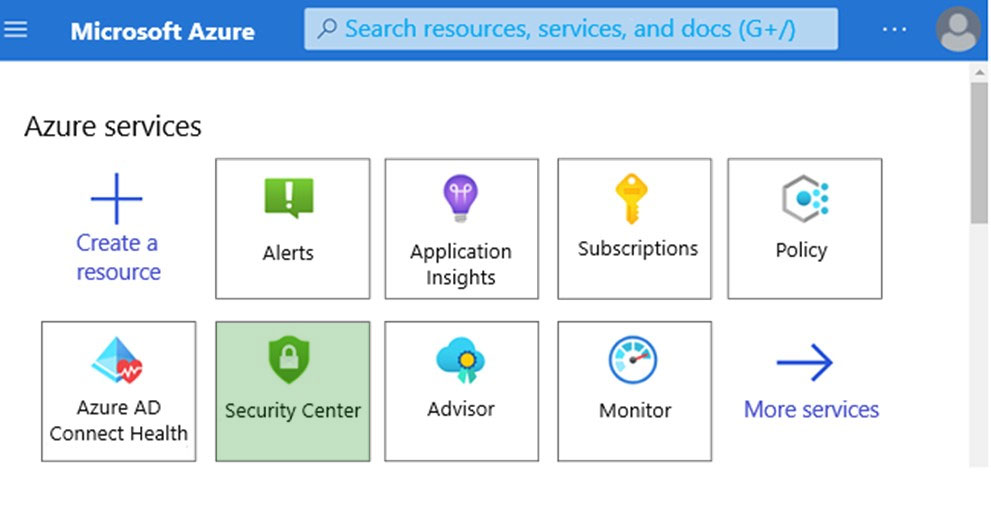
Reference:
https://docs.microsoft.com/en-us/azure/security-center/secure-score-access-and-track

Reference:
https://docs.microsoft.com/en-us/azure/security-center/secure-score-access-and-track
send
light_mode
delete
Question #25
DRAG DROP -
You are evaluating the compliance score in Compliance Manager.
Match the compliance score action subcategories to the appropriate actions.
To answer, drag the appropriate action subcategory from the column on the left to its action on the right. Each action subcategory may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place:
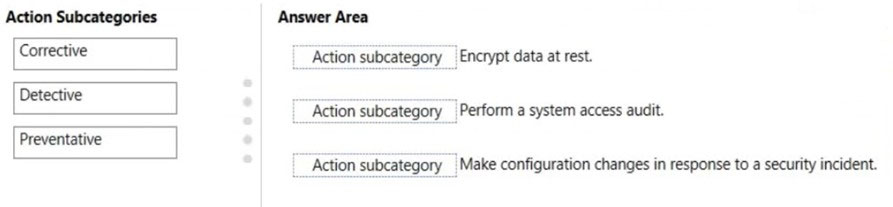
You are evaluating the compliance score in Compliance Manager.
Match the compliance score action subcategories to the appropriate actions.
To answer, drag the appropriate action subcategory from the column on the left to its action on the right. Each action subcategory may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place:

Correct Answer:
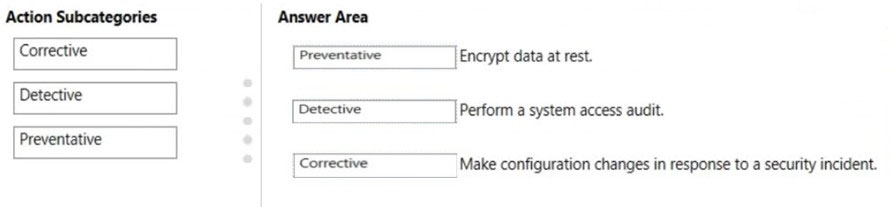
Box 1: Preventative -
Preventative actions address specific risks. For example, protecting information at rest using encryption is a preventative action against attacks and breaches.
Separation of duties is a preventative action to manage conflict of interest and guard against fraud.
Box 2: Detective -
Detective actions actively monitor systems to identify irregular conditions or behaviors that represent risk, or that can be used to detect intrusions or breaches.
Examples include system access auditing and privileged administrative actions. Regulatory compliance audits are a type of detective action used to find process issues.
Box 3: Corrective -
Corrective actions try to keep the adverse effects of a security incident to a minimum, take corrective action to reduce the immediate effect, and reverse the damage if possible. Privacy incident response is a corrective action to limit damage and restore systems to an operational state after a breach.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation

Box 1: Preventative -
Preventative actions address specific risks. For example, protecting information at rest using encryption is a preventative action against attacks and breaches.
Separation of duties is a preventative action to manage conflict of interest and guard against fraud.
Box 2: Detective -
Detective actions actively monitor systems to identify irregular conditions or behaviors that represent risk, or that can be used to detect intrusions or breaches.
Examples include system access auditing and privileged administrative actions. Regulatory compliance audits are a type of detective action used to find process issues.
Box 3: Corrective -
Corrective actions try to keep the adverse effects of a security incident to a minimum, take corrective action to reduce the immediate effect, and reverse the damage if possible. Privacy incident response is a corrective action to limit damage and restore systems to an operational state after a breach.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation
send
light_mode
delete
All Pages
