Microsoft MS-101 Exam Practice Questions (P. 3)
- Full Access (449 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are deploying Microsoft Endpoint Manager.
You successfully enroll Windows 10 devices in Endpoint Manager.
When you try to enroll an iOS device in Endpoint Manager, you get an error.
You need to ensure that you can enroll the iOS device in Endpoint Manager.
Solution: You create the Mobility (MDM and MAM) settings.
Does this meet the goal?

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
Question #22
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).
You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch).
You configure pilot co-management.
You add a new device named Device1 to the domain. You install the Configuration Manager client on Device1.
You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager.
Solution: You add Device1 to a Configuration Manager device collection.
Does this meet the goal?
- AYes
- BNoMost Voted
A
Reference:
https://docs.microsoft.com/en-us/mem/configmgr/comanage/tutorial-co-manage-clients

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
Question #23
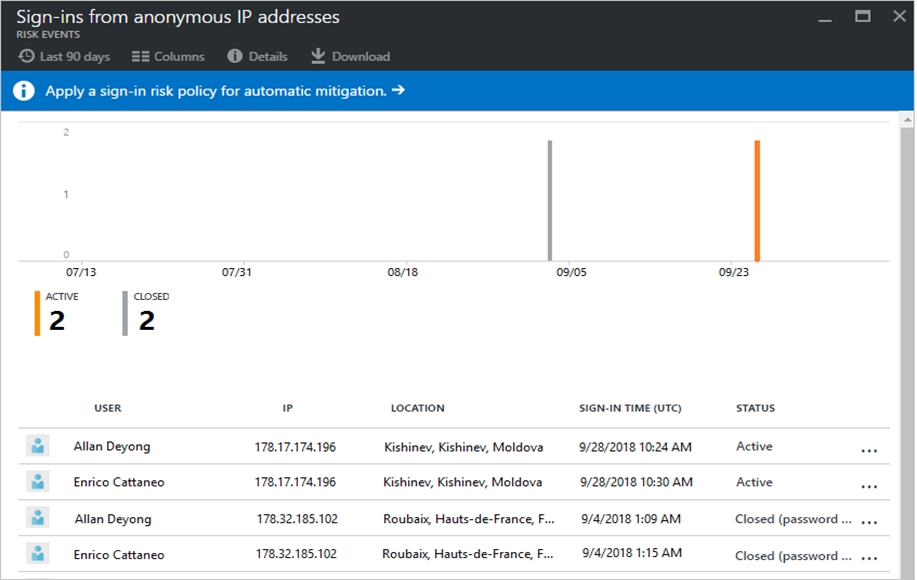
You need to reduce the likelihood that the sign-ins are identified as risky.
What should you do?
- AFrom the Security & Compliance admin center, create a classification label.
- BFrom the Security & Compliance admin center, add the users to the Security Readers role group.
- CFrom the Azure Active Directory admin center, configure the trusted IPs for multi-factor authentication.
- DFrom the Conditional access blade in the Azure Active Directory admin center, create named locations.Most Voted
D
References:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/location-condition

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
Question #24
Users in the research department work with sensitive data.
You need to prevent the research department users from accessing potentially unsafe websites by using hyperlinks embedded in email messages and documents. Users in other departments must not be restricted.
What should you do?
- ACreate a data loss prevention (DLP) policy that has a Content is shared condition.
- BModify the safe links policy Global settings.
- CCreate a data loss prevention (DLP) policy that has a Content contains condition.
- DCreate a new safe links policy.Most Voted
D
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/set-up-atp-safe-links-policies#policies-that-apply-to-specific-email-recipients

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
Question #25
You have a line-of-business application named App1 that users access by using the My Apps portal.
After some recent security breaches, you implement a conditional access policy for App1 that uses Conditional Access App Control.
You need to be alerted by email if impossible travel is detected for a user of App1. The solution must ensure that alerts are generated for App1 only.
What should you do?
- AFrom Microsoft Cloud App Security, create a Cloud Discovery anomaly detection policy.
- BFrom Microsoft Defender for Cloud Apps, modify the impossible travel alert policy.Most Voted
- CFrom Microsoft Defender for Cloud Apps, create an app discovery policy.
- DFrom the Azure Active Directory admin center, modify the conditional access policy.
A
References:
https://docs.microsoft.com/en-us/cloud-app-security/cloud-discovery-anomaly-detection-policy

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
Question #26
`Your sign-in was blocked. We've detected something unusual about this sign-in. For example, you might be signing in from a new location, device, or app. Before you can continue, we need to verify your identity. Please contact your admin.`
Which configuration prevents the users from signing in?
- AMicrosoft Azure Active Directory (Azure AD) Identity Protection policiesMost Voted
- BMicrosoft Azure Active Directory (Azure AD) conditional access policies
- CEndpoint Manager compliance policies
- DSecurity & Compliance data loss prevention (DLP) policies
B
References:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
Question #27
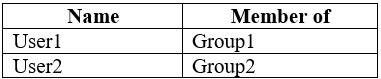
You have the Microsoft Azure Active Directory (Azure AD) users shown in the following table.
Your company uses Microsoft Intune.
Several devices are enrolled in Intune as shown in the following table.
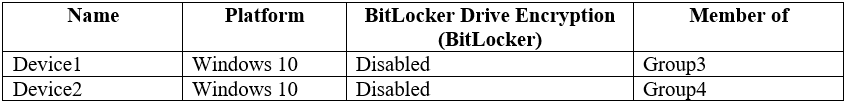
The device compliance policies in Intune are configured as shown in the following table.
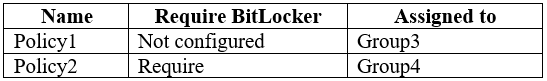
You create a conditional access policy that has the following settings:
✑ The Assignments settings are configured as follows:
1. Users and groups: Group1
2. Cloud apps: Microsoft Office 365 Exchange Online
3. Conditions: Include All device state, exclude Device marked as compliant
✑ Access controls is set to Block access.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
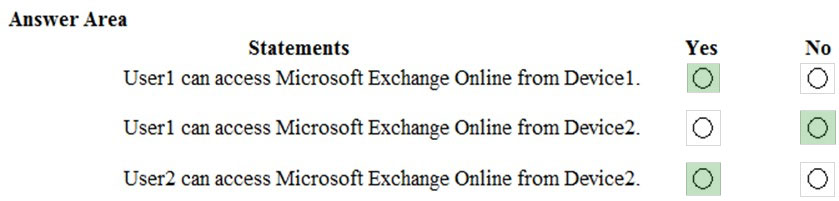
Box 1: Yes.
User1 is in Group1. The Conditional Access Policy applies to Group1. The Conditional Access Policy blocks access unless the device is marked as compliant.
BitLocker is disabled for Device1. Device1 is in Group3 which is assigned device Policy1. The BitLocker policy in Policy1 is not configured so BitLocker is not required.
Therefore, Device1 is compliant so User1 can access Exchange online from Device1.
Box 2: No.
User1 is in Group1. The Conditional Access Policy applies to Group1. The Conditional Access Policy blocks access unless the device is marked as compliant.
BitLocker is disabled for Device2. Device2 is in Group4 which is assigned device Policy2. The BitLocker policy in Policy2 is Required so BitLocker is required.
Therefore, Device2 is not compliant so User1 cannot access Exchange online from Device2.
Box3: Yes.
User2 is in Group2. The Conditional Access Policy applies to Group1. The Conditional Access Policy does not apply to Group2. So even though Device2 is non- compliant, User2 can access Exchange Online using Device2 because there is no Conditional Access Policy preventing him/her from doing so.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/conditions

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
Question #28
You have several devices enrolled in Microsoft Endpoint Manager.
You have a Microsoft Azure Active Directory (Azure AD) tenant that includes the users shown in the following table.
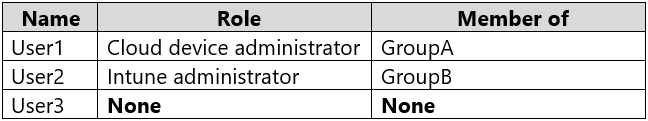
The device limit restrictions in Endpoint Manager are configured as shown in the following table.
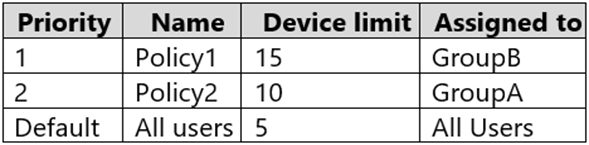
You add User3 as a device enrollment manager in Endpoint Manager.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:


Reference:
https://docs.microsoft.com/en-us/intune/device-enrollment-manager-enroll

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
Question #29
Your company has a Microsoft 365 tenant.
You plan to allow users that are members of a group named Engineering to enroll their mobile device in mobile device management (MDM).
The device type restrictions are configured as shown in the following table.
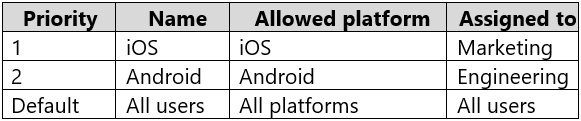
The device limit restrictions are configured as shown in the following table.
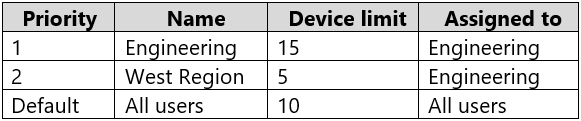
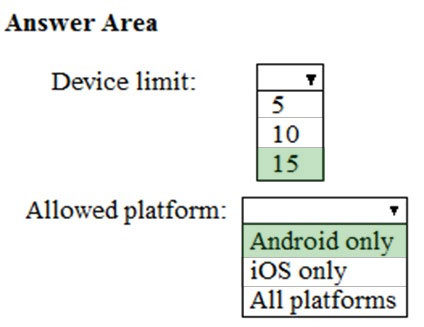
What is the effective configuration for the members of the Engineering group? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
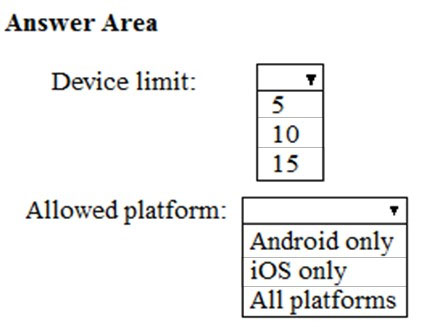

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
Question #30
You plan to deploy a custom Windows 10 Enterprise image to the Windows 8.1 devices.
You need to recommend a Windows 10 deployment method.
What should you recommend?
- Aa provisioning package
- Ban in-place upgrade
- Cwipe and load refreshMost Voted
- DWindows Autopilot
B
References:
https://docs.microsoft.com/en-us/microsoft-365/enterprise/windows10-infrastructure

Hi! Do you need help with this question ?
- Why isn't the A the right answer?
- Traducir la pregunta al español
Contributor get free access to an augmented ChatGPT 4 trained with the latest IT Questions.
All Pages