Microsoft AZ-500 Exam Practice Questions (P. 2)
- Full Access (508 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
Your company has an Azure Container Registry.
You have been tasked with assigning a user a role that allows for the uploading of images to the Azure Container Registry. The role assigned should not require more privileges than necessary.
Which of the following is the role you should assign?
You have been tasked with assigning a user a role that allows for the uploading of images to the Azure Container Registry. The role assigned should not require more privileges than necessary.
Which of the following is the role you should assign?
- AOwner
- BContributor
- CAcrPushMost Voted
- DAcrPull
Correct Answer:
C
Reference:
https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-roles
C
Reference:
https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-roles
send
light_mode
delete
Question #12
Your company has an Azure Container Registry.
You have been tasked with assigning a user a role that allows for the downloading of images from the Azure Container Registry. The role assigned should not require more privileges than necessary.
Which of the following is the role you should assign?
You have been tasked with assigning a user a role that allows for the downloading of images from the Azure Container Registry. The role assigned should not require more privileges than necessary.
Which of the following is the role you should assign?
- AReader
- BContributor
- CAcrDelete
- DAcrPullMost Voted
Correct Answer:
D
Reference:
https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-roles
D
Reference:
https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-roles
send
light_mode
delete
Question #13
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your Company's Azure subscription includes a virtual network that has a single subnet configured.
You have created a service endpoint for the subnet, which includes an Azure virtual machine that has Ubuntu Server 18.04 installed.
You are preparing to deploy Docker containers to the virtual machine. You need to make sure that the containers can access Azure Storage resources and Azure
SQL databases via the service endpoint.
You need to perform a task on the virtual machine prior to deploying containers.
Solution: You create an application security group.
Does the solution meet the goal?
Your Company's Azure subscription includes a virtual network that has a single subnet configured.
You have created a service endpoint for the subnet, which includes an Azure virtual machine that has Ubuntu Server 18.04 installed.
You are preparing to deploy Docker containers to the virtual machine. You need to make sure that the containers can access Azure Storage resources and Azure
SQL databases via the service endpoint.
You need to perform a task on the virtual machine prior to deploying containers.
Solution: You create an application security group.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
The correct approach involves ensuring that Docker containers within the VM can access Azure services through established service endpoints. Once these endpoints are set up for a subnet, all resources within, including VMs and any hosted containers, inherently gain access capabilities. Therefore, the necessity to create an Application Security Group (ASG) as proposed in the solution is extraneous for the goal of enabling access to Azure Storage and SQL databases. ASGs are more about defining security boundaries and less about facilitating connectivity, which is already handled by the service endpoints. Thus, the suggested solution does not meet the requirements for facilitating container access to Azure services.
send
light_mode
delete
Question #14
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your Company's Azure subscription includes a virtual network that has a single subnet configured.
You have created a service endpoint for the subnet, which includes an Azure virtual machine that has Ubuntu Server 18.04 installed.
You are preparing to deploy Docker containers to the virtual machine. You need to make sure that the containers can access Azure Storage resources and Azure
SQL databases via the service endpoint.
You need to perform a task on the virtual machine prior to deploying containers.
Solution: You create an AKS Ingress controller.
Does the solution meet the goal?
Your Company's Azure subscription includes a virtual network that has a single subnet configured.
You have created a service endpoint for the subnet, which includes an Azure virtual machine that has Ubuntu Server 18.04 installed.
You are preparing to deploy Docker containers to the virtual machine. You need to make sure that the containers can access Azure Storage resources and Azure
SQL databases via the service endpoint.
You need to perform a task on the virtual machine prior to deploying containers.
Solution: You create an AKS Ingress controller.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
To meet the requirement of allowing Docker containers access to Azure Storage and SQL databases via the service endpoint, creating an AKS Ingress controller isn't the appropriate solution. An Ingress controller mainly deals with managing external access to the services in a Kubernetes cluster, typically HTTP, which isn’t needed for this scenario involving a single VM. Instead, configuring the networking on the VM to ensure it correctly interacts with Azure services via service endpoints should be the focus. Thus, the solution proposing an AKS Ingress controller does not satisfy the need.
send
light_mode
delete
Question #15
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your Company's Azure subscription includes a virtual network that has a single subnet configured.
You have created a service endpoint for the subnet, which includes an Azure virtual machine that has Ubuntu Server 18.04 installed.
You are preparing to deploy Docker containers to the virtual machine. You need to make sure that the containers can access Azure Storage resources and Azure
SQL databases via the service endpoint.
You need to perform a task on the virtual machine prior to deploying containers.
Solution: You install the container network interface (CNI) plug-in.
Does the solution meet the goal?
Your Company's Azure subscription includes a virtual network that has a single subnet configured.
You have created a service endpoint for the subnet, which includes an Azure virtual machine that has Ubuntu Server 18.04 installed.
You are preparing to deploy Docker containers to the virtual machine. You need to make sure that the containers can access Azure Storage resources and Azure
SQL databases via the service endpoint.
You need to perform a task on the virtual machine prior to deploying containers.
Solution: You install the container network interface (CNI) plug-in.
Does the solution meet the goal?
- AYesMost Voted
- BNo
Correct Answer:
A
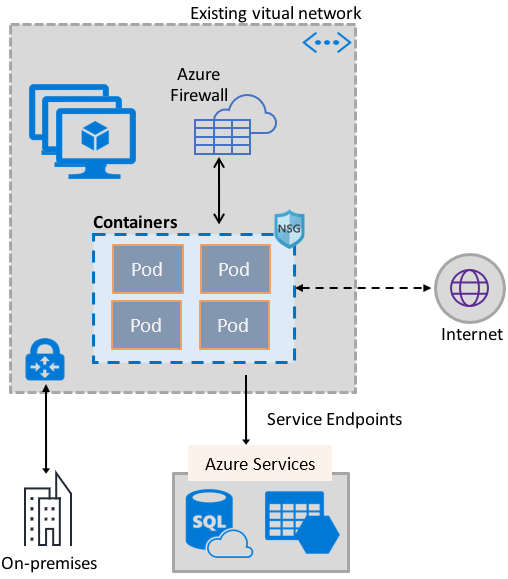
The Azure Virtual Network container network interface (CNI) plug-in installs in an Azure Virtual Machine. The plug-in supports both Linux and Windows platform.
The plug-in assigns IP addresses from a virtual network to containers brought up in the virtual machine, attaching them to the virtual network, and connecting them directly to other containers and virtual network resources. The plug-in doesn't rely on overlay networks, or routes, for connectivity, and provides the same performance as virtual machines.
The following picture shows how the plug-in provides Azure Virtual Network capabilities to Pods:
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/container-networking-overview
A
The Azure Virtual Network container network interface (CNI) plug-in installs in an Azure Virtual Machine. The plug-in supports both Linux and Windows platform.
The plug-in assigns IP addresses from a virtual network to containers brought up in the virtual machine, attaching them to the virtual network, and connecting them directly to other containers and virtual network resources. The plug-in doesn't rely on overlay networks, or routes, for connectivity, and provides the same performance as virtual machines.
The following picture shows how the plug-in provides Azure Virtual Network capabilities to Pods:

Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/container-networking-overview
send
light_mode
delete
Question #16
You make use of Azure Resource Manager templates to deploy Azure virtual machines.
You have been tasked with making sure that Windows features that are not in use, are automatically inactivated when instances of the virtual machines are provisioned.
Which of the following actions should you take?
You have been tasked with making sure that Windows features that are not in use, are automatically inactivated when instances of the virtual machines are provisioned.
Which of the following actions should you take?
- AYou should make use of Azure DevOps.
- BYou should make use of Azure Automation State Configuration.Most Voted
- CYou should make use of network security groups (NSG).
- DYou should make use of Azure Blueprints.
Correct Answer:
B
You can use Azure Automation State Configuration to manage Azure VMs (both Classic and Resource Manager), on-premises VMs, Linux machines, AWS VMs, and on-premises physical machines.
Note: Azure Automation State Configuration provides a DSC pull server similar to the Windows Feature DSC-Service so that target nodes automatically receive configurations, conform to the desired state, and report back on their compliance. The built-in pull server in Azure Automation eliminates the need to set up and maintain your own pull server. Azure Automation can target virtual or physical Windows or Linux machines, in the cloud or on-premises.
Reference:
https://docs.microsoft.com/en-us/azure/automation/automation-dsc-getting-started
B
You can use Azure Automation State Configuration to manage Azure VMs (both Classic and Resource Manager), on-premises VMs, Linux machines, AWS VMs, and on-premises physical machines.
Note: Azure Automation State Configuration provides a DSC pull server similar to the Windows Feature DSC-Service so that target nodes automatically receive configurations, conform to the desired state, and report back on their compliance. The built-in pull server in Azure Automation eliminates the need to set up and maintain your own pull server. Azure Automation can target virtual or physical Windows or Linux machines, in the cloud or on-premises.
Reference:
https://docs.microsoft.com/en-us/azure/automation/automation-dsc-getting-started
send
light_mode
delete
Question #17
Your company's Azure subscription includes Windows Server 2016 Azure virtual machines.
You are informed that every virtual machine must have a custom antimalware virtual machine extension installed. You are writing the necessary code for a policy that will help you achieve this.
Which of the following is an effect that must be included in your code?
You are informed that every virtual machine must have a custom antimalware virtual machine extension installed. You are writing the necessary code for a policy that will help you achieve this.
Which of the following is an effect that must be included in your code?
- ADisabled
- BModify
- CAuditIfNotExists
- DDeployIfNotExistsMost Voted
Correct Answer:
D
DeployIfNotExists executes a template deployment when the condition is met.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
D
DeployIfNotExists executes a template deployment when the condition is met.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
send
light_mode
delete
Question #18
Your company makes use of Azure Active Directory (Azure AD) in a hybrid configuration. All users are making use of hybrid Azure AD joined Windows 10 computers.
You manage an Azure SQL database that allows for Azure AD authentication.
You need to make sure that database developers are able to connect to the SQL database via Microsoft SQL Server Management Studio (SSMS). You also need to make sure the developers use their on-premises Active Directory account for authentication. Your strategy should allow for authentication prompts to be kept to a minimum.
Which of the following is the authentication method the developers should use?
You manage an Azure SQL database that allows for Azure AD authentication.
You need to make sure that database developers are able to connect to the SQL database via Microsoft SQL Server Management Studio (SSMS). You also need to make sure the developers use their on-premises Active Directory account for authentication. Your strategy should allow for authentication prompts to be kept to a minimum.
Which of the following is the authentication method the developers should use?
- AAzure AD token.
- BAzure Multi-Factor authentication.
- CActive Directory integrated authentication.Most Voted
Correct Answer:
C
Azure AD can be the initial Azure AD managed domain. Azure AD can also be an on-premises Active Directory Domain Services that is federated with the Azure
AD.
Using an Azure AD identity to connect using SSMS or SSDT
The following procedures show you how to connect to a SQL database with an Azure AD identity using SQL Server Management Studio or SQL Server Database
Tools.
Active Directory integrated authentication
Use this method if you are logged in to Windows using your Azure Active Directory credentials from a federated domain.
1. Start Management Studio or Data Tools and in the Connect to Server (or Connect to Database Engine) dialog box, in the Authentication box, select Active
Directory - Integrated. No password is needed or can be entered because your existing credentials will be presented for the connection.
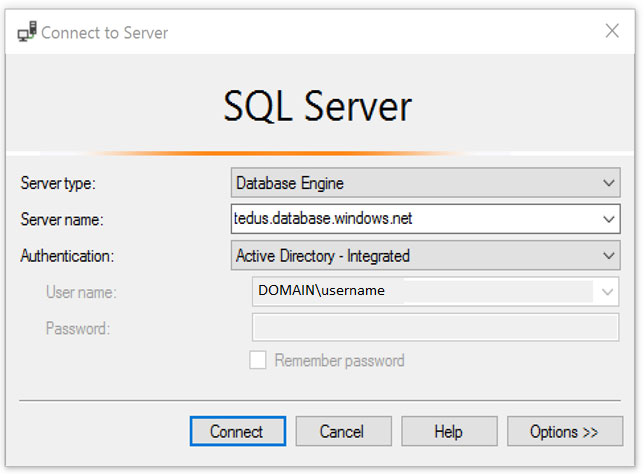
2. Select the Options button, and on the Connection Properties page, in the Connect to database box, type the name of the user database you want to connect to.
(The AD domain name or tenant IDג€ option is only supported for Universal with MFA connection options, otherwise it is greyed out.)
C
Azure AD can be the initial Azure AD managed domain. Azure AD can also be an on-premises Active Directory Domain Services that is federated with the Azure
AD.
Using an Azure AD identity to connect using SSMS or SSDT
The following procedures show you how to connect to a SQL database with an Azure AD identity using SQL Server Management Studio or SQL Server Database
Tools.
Active Directory integrated authentication
Use this method if you are logged in to Windows using your Azure Active Directory credentials from a federated domain.
1. Start Management Studio or Data Tools and in the Connect to Server (or Connect to Database Engine) dialog box, in the Authentication box, select Active
Directory - Integrated. No password is needed or can be entered because your existing credentials will be presented for the connection.

2. Select the Options button, and on the Connection Properties page, in the Connect to database box, type the name of the user database you want to connect to.
(The AD domain name or tenant IDג€ option is only supported for Universal with MFA connection options, otherwise it is greyed out.)
send
light_mode
delete
Question #19
You have been tasked with enabling Advanced Threat Protection for an Azure SQL Database server.
Advanced Threat Protection must be configured to identify all types of threat detection.
Which of the following will happen if when a faulty SQL statement is generate in the database by an application?
Advanced Threat Protection must be configured to identify all types of threat detection.
Which of the following will happen if when a faulty SQL statement is generate in the database by an application?
- AA Potential SQL injection alert is triggered.
- BA Vulnerability to SQL injection alert is triggered.Most Voted
- CAn Access from a potentially harmful application alert is triggered.
- DA Brute force SQL credentials alert is triggered.
Correct Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/sql-database/sql-database-threat-detection-overview
B
Reference:
https://docs.microsoft.com/en-us/azure/sql-database/sql-database-threat-detection-overview
send
light_mode
delete
Question #20
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
You are in the process of creating an Azure Kubernetes Service (AKS) cluster. The Azure Kubernetes Service (AKS) cluster must be able to connect to an Azure
Container Registry.
You want to make sure that Azure Kubernetes Service (AKS) cluster authenticates to the Azure Container Registry by making use of the auto-generated service principal.
Solution: You create an Azure Active Directory (Azure AD) role assignment.
Does the solution meet the goal?
You are in the process of creating an Azure Kubernetes Service (AKS) cluster. The Azure Kubernetes Service (AKS) cluster must be able to connect to an Azure
Container Registry.
You want to make sure that Azure Kubernetes Service (AKS) cluster authenticates to the Azure Container Registry by making use of the auto-generated service principal.
Solution: You create an Azure Active Directory (Azure AD) role assignment.
Does the solution meet the goal?
- AYes
- BNoMost Voted
Correct Answer:
B
When you create an AKS cluster, Azure also creates a service principal to support cluster operability with other Azure resources. You can use this auto-generated service principal for authentication with an ACR registry. To do so, you need to create an Azure AD role assignment that grants the cluster's service principal access to the container registry.
Reference:
https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-auth-aks
B
When you create an AKS cluster, Azure also creates a service principal to support cluster operability with other Azure resources. You can use this auto-generated service principal for authentication with an ACR registry. To do so, you need to create an Azure AD role assignment that grants the cluster's service principal access to the container registry.
Reference:
https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-auth-aks
send
light_mode
delete
All Pages
