Microsoft AZ-304 Exam Practice Questions (P. 4)
- Full Access (237 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #16
You have an Azure subscription that contains web apps in three Azure regions.
You need to implement Azure Key Vault to meet the following requirements:
✑ In the event of a regional outage, all keys must be readable.
✑ All the web apps in the subscription must be able to access Key Vault.
✑ The number of Key Vault resources to be deployed and managed must be minimized.
How many instances of Key Vault should you implement?
You need to implement Azure Key Vault to meet the following requirements:
✑ In the event of a regional outage, all keys must be readable.
✑ All the web apps in the subscription must be able to access Key Vault.
✑ The number of Key Vault resources to be deployed and managed must be minimized.
How many instances of Key Vault should you implement?
- A1
- B2
- C3Most Voted
- D6
Correct Answer:
A
The contents of your key vault are replicated within the region and to a secondary region at least 150 miles away but within the same geography. This maintains high durability of your keys and secrets. See the Azure paired regions document for details on specific region pairs.
Example: Secrets that must be shared by your application in both Europe West and Europe North. Minimize these as much as you can. Put these in a key vault in either of the two regions. Use the same URI from both regions. Microsoft will fail over the Key Vault service internally.
Reference:
https://docs.microsoft.com/en-us/azure/key-vault/general/disaster-recovery-guidance
A
The contents of your key vault are replicated within the region and to a secondary region at least 150 miles away but within the same geography. This maintains high durability of your keys and secrets. See the Azure paired regions document for details on specific region pairs.
Example: Secrets that must be shared by your application in both Europe West and Europe North. Minimize these as much as you can. Put these in a key vault in either of the two regions. Use the same URI from both regions. Microsoft will fail over the Key Vault service internally.
Reference:
https://docs.microsoft.com/en-us/azure/key-vault/general/disaster-recovery-guidance
send
light_mode
delete
Question #17
You have an Azure Active Directory (Azure AD) tenant.
You plan to provide users with access to shared files by using Azure Storage. The users will be provided with different levels of access to various Azure file shares based on their user account or their group membership.
You need to recommend which additional Azure services must be used to support the planned deployment.
What should you include in the recommendation?
You plan to provide users with access to shared files by using Azure Storage. The users will be provided with different levels of access to various Azure file shares based on their user account or their group membership.
You need to recommend which additional Azure services must be used to support the planned deployment.
What should you include in the recommendation?
- Aan Azure AD enterprise application
- BAzure Information Protection
- Can Azure AD Domain Services (Azure AD DS) instanceMost Voted
- Dan Azure Front Door instance
Correct Answer:
C
Azure Filesג€‰supports identity-based authentication over Server Message Block (SMB) throughג€‰two types of Domain Services: on-premises Active Directory Domain
Services (AD DS) and Azure Active Directory Domain Services (Azure AD DS).
Reference:
https://docs.microsoft.com/en-us/azure/storage/files/storage-files-identity-auth-active-directory-domain-service-enable
C
Azure Filesג€‰supports identity-based authentication over Server Message Block (SMB) throughג€‰two types of Domain Services: on-premises Active Directory Domain
Services (AD DS) and Azure Active Directory Domain Services (Azure AD DS).
Reference:
https://docs.microsoft.com/en-us/azure/storage/files/storage-files-identity-auth-active-directory-domain-service-enable
send
light_mode
delete
Question #18
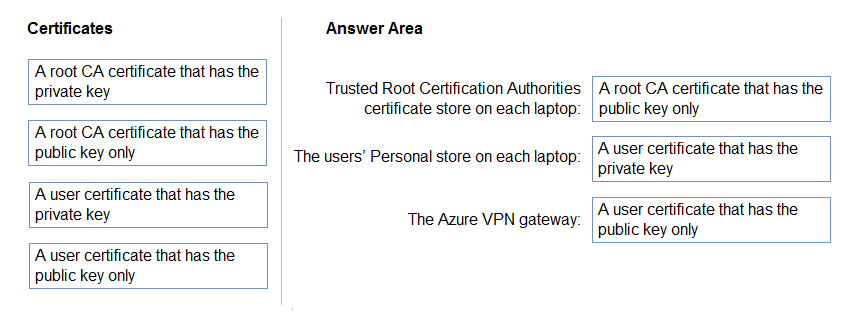
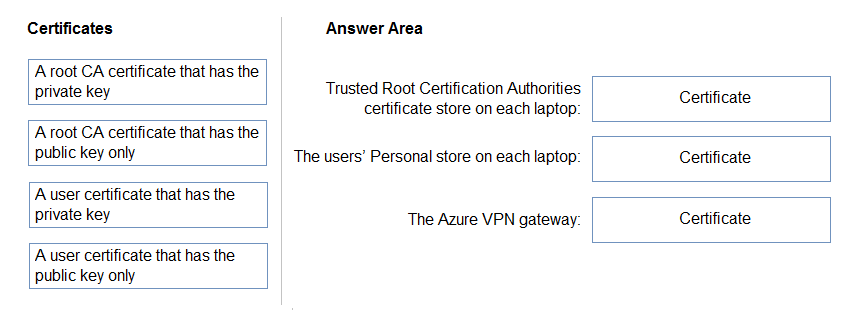
DRAG DROP -
Your company has users who work remotely from laptops.
You plan to move some of the applications accessed by the remote users to Azure virtual machines. The users will access the applications in Azure by using a point-to-site VPN connection. You will use certificates generated from an on-premises-based Certification authority (CA).
You need to recommend which certificates are required for the deployment.
What should you include in the recommendation? To answer, drag the appropriate certificates to the correct targets. Each certificate may be used once, more than once, of not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Your company has users who work remotely from laptops.
You plan to move some of the applications accessed by the remote users to Azure virtual machines. The users will access the applications in Azure by using a point-to-site VPN connection. You will use certificates generated from an on-premises-based Certification authority (CA).
You need to recommend which certificates are required for the deployment.
What should you include in the recommendation? To answer, drag the appropriate certificates to the correct targets. Each certificate may be used once, more than once, of not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

send
light_mode
delete
Question #19
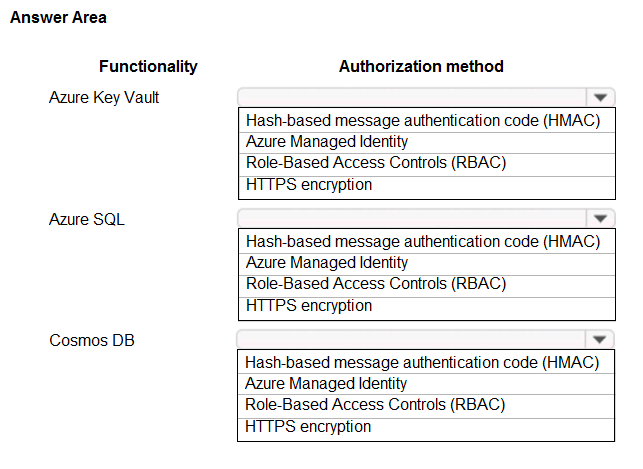
HOTSPOT -
You are building an application that will run in a virtual machine (VM). The application will use Azure Managed Identity.
The application uses Azure Key Vault, Azure SQL Database, and Azure Cosmos DB.
You need to ensure the application can use secure credentials to access these services.
Which authorization method should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You are building an application that will run in a virtual machine (VM). The application will use Azure Managed Identity.
The application uses Azure Key Vault, Azure SQL Database, and Azure Cosmos DB.
You need to ensure the application can use secure credentials to access these services.
Which authorization method should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
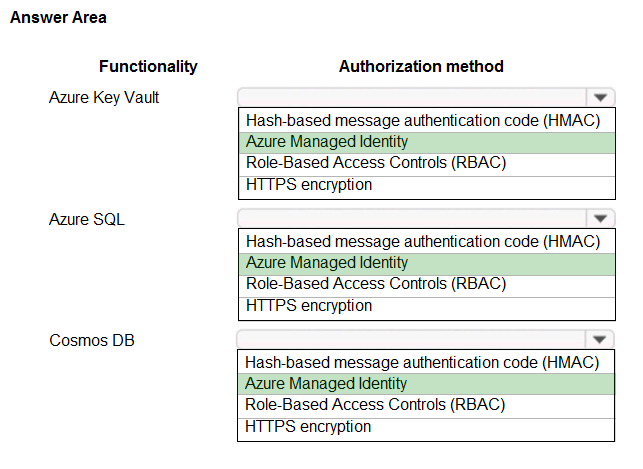
Note: Managed identities for Azure resources is the new name for the service formerly known as Managed Service Identity (MSI).
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/overview

Note: Managed identities for Azure resources is the new name for the service formerly known as Managed Service Identity (MSI).
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/overview
send
light_mode
delete
Question #20
You have an Azure subscription that contains a custom application named Application1. Application1 was developed by an external company named Fabrikam,
Ltd. Developers at Fabrikam were assigned role-based access control (RBAC) permissions to the Application1 components. All users are licensed for the
Microsoft 365 E5 plan.
You need to recommend a solution to verify whether the Fabrikam developers still require permissions to Application1. The solution must meet the following requirements:
✑ To the manager of the developers, send a monthly email message that lists the access permissions to Application1.
✑ If the manager does not verify an access permission, automatically revoke that permission.
✑ Minimize development effort.
What should you recommend?
Ltd. Developers at Fabrikam were assigned role-based access control (RBAC) permissions to the Application1 components. All users are licensed for the
Microsoft 365 E5 plan.
You need to recommend a solution to verify whether the Fabrikam developers still require permissions to Application1. The solution must meet the following requirements:
✑ To the manager of the developers, send a monthly email message that lists the access permissions to Application1.
✑ If the manager does not verify an access permission, automatically revoke that permission.
✑ Minimize development effort.
What should you recommend?
- ACreate an Azure Automation runbook that runs the Get-AzureADUserAppRoleAssignment cmdlet.
- BCreate an Azure Automation runbook that runs the Get-AzRoleAssignment cmdlet.
- CIn Azure Active Directory (Azure AD), create an access review of Application1.Most Voted
- DIn Azure Active Directory (AD) Privileged Identity Management, create a custom role assignment for the Application1 resources.
Correct Answer:
C
C
send
light_mode
delete
All Pages