Microsoft 70-413 Exam Practice Questions (P. 5)
- Full Access (337 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain and two sites named Montreal and Vancouver.
Montreal contains an IP Address Management (IPAM) server named Server1 that is used to manage all of the DHCP servers and the DNS servers in the site.
Vancouver contains several DHCP servers and several DNS servers.
In Vancouver, you install the IP Address Management (IPAM) Server feature on a server named Server2.
You need to recommend which configurations must be performed to ensure that the DHCP servers and the DNS servers in Vancouver are managed by Server2.
What should you recommend?
Montreal contains an IP Address Management (IPAM) server named Server1 that is used to manage all of the DHCP servers and the DNS servers in the site.
Vancouver contains several DHCP servers and several DNS servers.
In Vancouver, you install the IP Address Management (IPAM) Server feature on a server named Server2.
You need to recommend which configurations must be performed to ensure that the DHCP servers and the DNS servers in Vancouver are managed by Server2.
What should you recommend?
- AReplicate the IPAM database from Server1 to Server2. On Server2, change the manageability status of the DNS servers and the DHCP servers in Vancouver.
- BReplicate the IPAM database from Server1 to Server2. On Server1, change the manageability status of the DNS servers and the DHCP servers in Vancouver.
- CFrom Server2, run the Invoke-IpamGpoProvisioning cmdlet. On Server2, change the manageability status of the DNS servers and the DHCP servers in Vancouver.
- DFrom Server1, run the Invoke-IpamGpoProvisioning cmdlet. On Server1, change the manageability status of the DNS servers and the DHCP servers in Vancouver.
Correct Answer:
C
Invoke-IpamGpoProvisioning -
Creates and links group policies in the specified domain for provisioning required access settings on the servers managed by the computer running the IPAM server.
Reference:
Invoke-IpamGpoProvisioning -
https://technet.microsoft.com/en-us/library/jj553805(v=wps.630).aspx
C
Invoke-IpamGpoProvisioning -
Creates and links group policies in the specified domain for provisioning required access settings on the servers managed by the computer running the IPAM server.
Reference:
Invoke-IpamGpoProvisioning -
https://technet.microsoft.com/en-us/library/jj553805(v=wps.630).aspx
send
light_mode
delete
Question #42
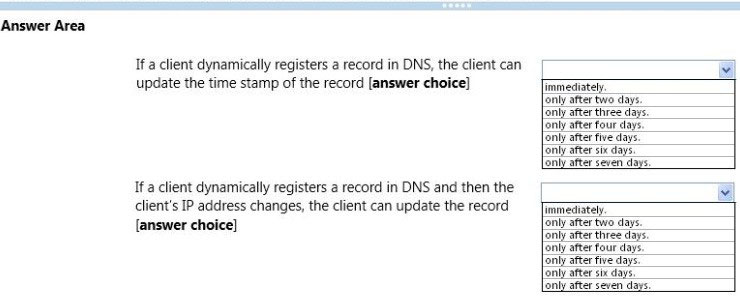
HOTSPOT -
You have a domain controller that hosts an Active Directory-integrated zone.
On the domain controller, you run the following cmdlet:
PS C:\> Get-DnsServerScavenging -
NoRefreshInterval:2.00:00:00 -
RefreshInterval:3.00:00:00 -
ScavengingInterval:4.00:00:00 -
ScavengingState:True -
LastScavengeTime:1/30/2014 9:10:36 AM
Use the drop-down menus to select the answer choice that completes each statement.
Hot Area:
You have a domain controller that hosts an Active Directory-integrated zone.
On the domain controller, you run the following cmdlet:
PS C:\> Get-DnsServerScavenging -
NoRefreshInterval:2.00:00:00 -
RefreshInterval:3.00:00:00 -
ScavengingInterval:4.00:00:00 -
ScavengingState:True -
LastScavengeTime:1/30/2014 9:10:36 AM
Use the drop-down menus to select the answer choice that completes each statement.
Hot Area:

Correct Answer:
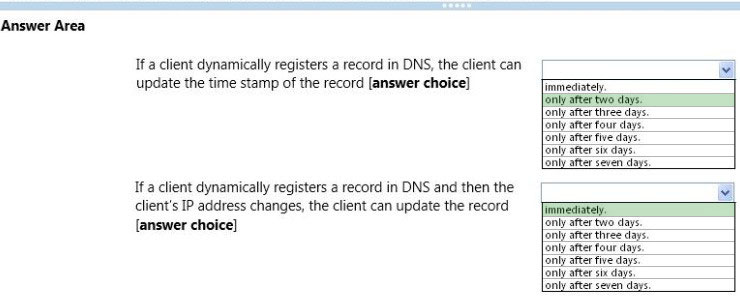
First answer -
* -NoRefreshInterval<TimeSpan>
Specifies a length of time as a TimeSpan object. NoRefreshInterval sets a period of time in which no refreshes are accepted for dynamically updated records.
Zones on the server inherit this value automatically.
This value is the interval between the last update of a timestamp for a record and the earliest time when the timestamp can be refreshed. The minimum value is 0.
The maximum value is 8760 hours (seven days).
* Here it is set to 2 days: NoRefreshInterval:2.00:00:00
Second answer -
-ScavengingState<Boolean> (In this question it is set to true)
Enables or disables automatic scavenging of stale records. ScavengingState determines whether the DNS scavenging feature is enabled by default on newly created zones. The acceptable values for this parameter are:
-- $False. Disables scavenging. This is the default setting.
-- $True. Enables scavenging

First answer -
* -NoRefreshInterval<TimeSpan>
Specifies a length of time as a TimeSpan object. NoRefreshInterval sets a period of time in which no refreshes are accepted for dynamically updated records.
Zones on the server inherit this value automatically.
This value is the interval between the last update of a timestamp for a record and the earliest time when the timestamp can be refreshed. The minimum value is 0.
The maximum value is 8760 hours (seven days).
* Here it is set to 2 days: NoRefreshInterval:2.00:00:00
Second answer -
-ScavengingState<Boolean> (In this question it is set to true)
Enables or disables automatic scavenging of stale records. ScavengingState determines whether the DNS scavenging feature is enabled by default on newly created zones. The acceptable values for this parameter are:
-- $False. Disables scavenging. This is the default setting.
-- $True. Enables scavenging
send
light_mode
delete
Question #43
You are the administrator for a large company. You plan to implement servers in the environment that do not use local hard drives.
You need to recommend a supported storage solution.
Which technology should you recommend?
You need to recommend a supported storage solution.
Which technology should you recommend?
- AClustered NAS
- BCloud storage
- CFibre Channel SAN
- DServer Message Block (SMB) Scale-out File Servers
- EStorage Spaces
Correct Answer:
C
Reference:
https://www.networkworld.com/article/3256312/what-is-a-san-and-how-does-it-differ-from-nas.html https://docs.microsoft.com/en-us/windows-server/storage/storage-spaces/overview
C
Reference:
https://www.networkworld.com/article/3256312/what-is-a-san-and-how-does-it-differ-from-nas.html https://docs.microsoft.com/en-us/windows-server/storage/storage-spaces/overview
send
light_mode
delete
Question #44
Your network contains an internal network and a perimeter network. The internal network contains an Active Directory forest named contoso.com. The forest contains a Microsoft Exchange Server 2010 organization. All of the domain controllers in contoso.com run Windows Server 2012.
The perimeter network contains an Active Directory forest named litware.com.
You deploy Microsoft Forefront Unified Access Gateway (UAG) to litware.com. All of the domain controllers in litware.com run Windows Server 2012.
Some users connect from outside the network to use Outlook Web App.
You need to ensure that external users can authenticate by using client certificates.
What should you do?
More than one answer choice may achieve the goal. Select the BEST answer.
The perimeter network contains an Active Directory forest named litware.com.
You deploy Microsoft Forefront Unified Access Gateway (UAG) to litware.com. All of the domain controllers in litware.com run Windows Server 2012.
Some users connect from outside the network to use Outlook Web App.
You need to ensure that external users can authenticate by using client certificates.
What should you do?
More than one answer choice may achieve the goal. Select the BEST answer.
- ATo the perimeter network, add an Exchange server that has the Client Access server role installed.
- BDeploy UAG to contoso.com.
- CEnable Kerberos delegation in litware.com.
- DEnable Kerberos constrained delegation in litware.com.
Correct Answer:
D
Forefront TMG provides support for Kerberos constrained delegation (often abbreviated as KCD) to enable published Web servers to authenticate users by
Kerberos after Forefront TMG verifies their identity by using a non-Kerberos authentication method. When used in this way, Kerberos constrained delegation eliminates the need for requiring users to provide credentials twice.
Reference:
About Kerberos constrained delegation
https://technet.microsoft.com/en-us/library/cc995228.aspx
D
Forefront TMG provides support for Kerberos constrained delegation (often abbreviated as KCD) to enable published Web servers to authenticate users by
Kerberos after Forefront TMG verifies their identity by using a non-Kerberos authentication method. When used in this way, Kerberos constrained delegation eliminates the need for requiring users to provide credentials twice.
Reference:
About Kerberos constrained delegation
https://technet.microsoft.com/en-us/library/cc995228.aspx
send
light_mode
delete
Question #45
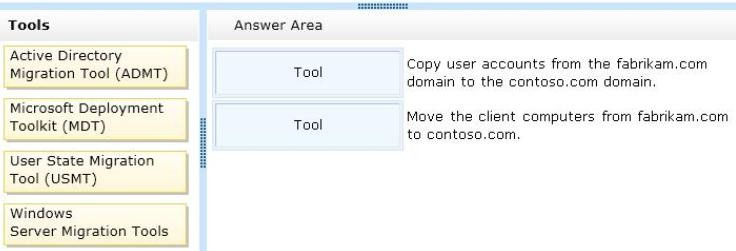
DRAG DROP -
Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com.
You plan to decommission the fabrikam.com domain.
You need to perform the following migration tasks:
✑ Copy user accounts from the fabrikam.com domain to the contoso.com domain.
✑ Move the client computers from fabrikam.com to contoso.com.
The solution must ensure that all of the user profiles are associated to the migrated user accounts.
Which tool should you use to perform each task? To answer, drag the appropriate tools to the correct migration tasks. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com.
You plan to decommission the fabrikam.com domain.
You need to perform the following migration tasks:
✑ Copy user accounts from the fabrikam.com domain to the contoso.com domain.
✑ Move the client computers from fabrikam.com to contoso.com.
The solution must ensure that all of the user profiles are associated to the migrated user accounts.
Which tool should you use to perform each task? To answer, drag the appropriate tools to the correct migration tasks. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

Correct Answer:
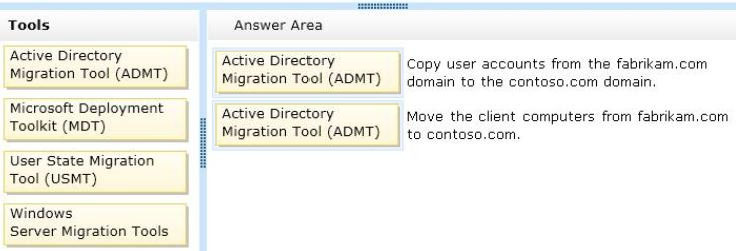
Note:
* You can use ADMT to migrate objects in Active Directory forests. This tool includes wizards that automate migration tasks, such as migrating users, groups, service accounts, computers, and trusts and performing security translation.
* You might perform an interforest restructure for business changes, such as mergers or acquisitions or divestitures, in which your organizations have to combine or divide resources. As part of the restructuring process, when you migrate objects between forests both the source and target domain environments exist simultaneously.
* Migration objects Domain objects that are moved from the source domain to the target domain during the migration process. Migration objects can be user accounts, service accounts, groups, or computers.

Note:
* You can use ADMT to migrate objects in Active Directory forests. This tool includes wizards that automate migration tasks, such as migrating users, groups, service accounts, computers, and trusts and performing security translation.
* You might perform an interforest restructure for business changes, such as mergers or acquisitions or divestitures, in which your organizations have to combine or divide resources. As part of the restructuring process, when you migrate objects between forests both the source and target domain environments exist simultaneously.
* Migration objects Domain objects that are moved from the source domain to the target domain during the migration process. Migration objects can be user accounts, service accounts, groups, or computers.
send
light_mode
delete
Question #46
HOTSPOT -
Your network contains an Active Directory forest named contoso.com. The forest contains one domain. All domain controllers run Windows Server 2012. The functional level of the forest and the domain is Windows Server 2012.
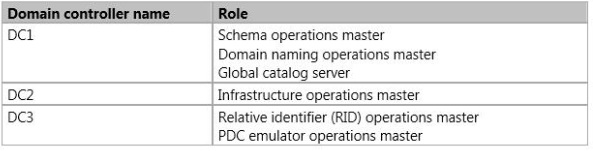
The domain contains three domain controllers. The domain controllers are configured as shown in the following table.
In the forest, you plan to add a new domain controller that runs Windows Server 2012 R2.
You need to prepare the environment before you add the new domain controller.
Which domain controllers must be available to run each command? To answer, select the appropriate domain controllers in the answer area.
Hot Area:
Your network contains an Active Directory forest named contoso.com. The forest contains one domain. All domain controllers run Windows Server 2012. The functional level of the forest and the domain is Windows Server 2012.
The domain contains three domain controllers. The domain controllers are configured as shown in the following table.

In the forest, you plan to add a new domain controller that runs Windows Server 2012 R2.
You need to prepare the environment before you add the new domain controller.
Which domain controllers must be available to run each command? To answer, select the appropriate domain controllers in the answer area.
Hot Area:

Correct Answer:
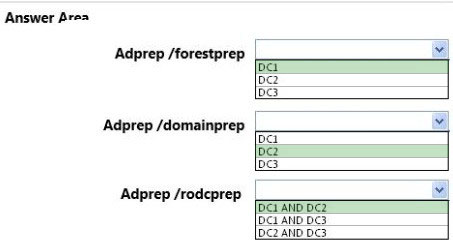
* adprep /forestprep
Must be run on the schema operations master for the forest (here DC1).
Once for the entire forest -
* adprep /domainprep
Must be run on the infrastructure operations (DC2) master for the domain.
* adprep /rodcprep
Can be run from any computer. This command performs operations remotely. For the operations to complete successfully, the domain naming operations master
(DC1) for the forest and the infrastructure operations master (DC2) for each application directory partition and each domain partition must be accessible.

* adprep /forestprep
Must be run on the schema operations master for the forest (here DC1).
Once for the entire forest -
* adprep /domainprep
Must be run on the infrastructure operations (DC2) master for the domain.
* adprep /rodcprep
Can be run from any computer. This command performs operations remotely. For the operations to complete successfully, the domain naming operations master
(DC1) for the forest and the infrastructure operations master (DC2) for each application directory partition and each domain partition must be accessible.
send
light_mode
delete
Question #47
You are designing an Active Directory forest for a company named Contoso, Ltd. Contoso identifies the following administration requirements for the design:
✑ User account administration and Group Policy administration will be performed by network technicians. The technicians will be added to a group named
OUAdmins.
✑ IT staff who are responsible for backing up servers will have user accounts that are members of the Backup Operators group in the domain.
✑ All user accounts will be located in an organizational unit (OU) named AllEmployees.
You run the Delegation of Control Wizard and assign the OUAdmins group full control to all of the objects in the AllEmployeesOU.
After delegating the required permissions, you discover that the user accounts of some of the IT staff have inconsistent permissions on the objects in
AllEmployees.
You need to recommend a solution to ensure that the members of OUAdmins can manage all of the objects in AllEmployees.
What should you include in the recommendation?
✑ User account administration and Group Policy administration will be performed by network technicians. The technicians will be added to a group named
OUAdmins.
✑ IT staff who are responsible for backing up servers will have user accounts that are members of the Backup Operators group in the domain.
✑ All user accounts will be located in an organizational unit (OU) named AllEmployees.
You run the Delegation of Control Wizard and assign the OUAdmins group full control to all of the objects in the AllEmployeesOU.
After delegating the required permissions, you discover that the user accounts of some of the IT staff have inconsistent permissions on the objects in
AllEmployees.
You need to recommend a solution to ensure that the members of OUAdmins can manage all of the objects in AllEmployees.
What should you include in the recommendation?
- ARemove the IT staff user accounts from Backup Operators and place them in a new group. Grant the new group the Backup files and directories user right and the Restore files and directories user right. Enforce permission inheritance on all of the objects in the AllEmployeesOU.
- BCreate separate administrator user accounts for the technicians. Enforce permission inheritance on all of the objects in the AllEmployeesOU. Delegate permissions to the new user accounts.
- CEnforce permission inheritance on all of the objects in the AllEmployeesOU. Run the Delegation of Control Wizard.
- DMove the user accounts of the technicians to a separate OU. Enforce permission inheritance on all of the objects in the AllEmployeesOU. Run the Delegation of Control Wizard on the AllEmployeesOU.
Correct Answer:
A
The users will still have their backup rights and when the delegated permissions are reapplied to the OU, AdminSDHolder will not find the accounts as members of the protected Backup Operators group any longer and will do nothing. Thus, leaving the accounts with the limited delegated rights required.
A
The users will still have their backup rights and when the delegated permissions are reapplied to the OU, AdminSDHolder will not find the accounts as members of the protected Backup Operators group any longer and will do nothing. Thus, leaving the accounts with the limited delegated rights required.
send
light_mode
delete
Question #48
Your network contains an Active Directory forest named contoso.com. The forest contains one domain.
Your company plans to open a new division named Division1. A group named Division1Admins will administer users and groups for Division1.
You identify the following requirements for Division1:
✑ All Division1 users must have a complex password that is 14 characters.
✑ Division1Admins must be able to manage the user accounts for Division1.
✑ Division1Admins must be able to create groups, and then delete the groups that they create.
✑ Division1Admins must be able to reset user passwords and force a password change at the next logon for all Division1 users.
You need to recommend changes to the forest to support the Division1 requirements.
What should you recommend?
More than one answer choice may achieve the goal. Select the BEST answer.
Your company plans to open a new division named Division1. A group named Division1Admins will administer users and groups for Division1.
You identify the following requirements for Division1:
✑ All Division1 users must have a complex password that is 14 characters.
✑ Division1Admins must be able to manage the user accounts for Division1.
✑ Division1Admins must be able to create groups, and then delete the groups that they create.
✑ Division1Admins must be able to reset user passwords and force a password change at the next logon for all Division1 users.
You need to recommend changes to the forest to support the Division1 requirements.
What should you recommend?
More than one answer choice may achieve the goal. Select the BEST answer.
- AIn the forest, create a new organizational unit (OU) named Division1 and delegate permissions for the OU to the Division1Admins group. Move all of the Division1 user accounts to the new OU. Create a fine-grained password policy for the Division1 users.
- BCreate a new child domain named division1.contoso.com. Move all of the Division1 user accounts to the new domain. Add the Division1Admin members to the Domain Admins group. Configure the password policy in a Group Policy object (GPO).
- CCreate a new forest. Migrate all of the Division1 user objects to the new forest and add the Division1Admins members to the Enterprise Admins group. Configure the password policy in a Group Policy object (GPO).
- DIn the forest, create a new organizational unit (OU) named Division1 and add Division1Admins to the Managed By attribute of the new OU. Move the Division1 user objects to the new OU. Create a fine-grained password policy for the Division1 users.
Correct Answer:
A
A
send
light_mode
delete
Question #49
Your company has a main office and three branch offices. The main office is located in North America. The branch offices are located in South America, Asia and
Europe.
You plan to design an Active Directory forest and domain infrastructure.
You need to recommend an Active Directory design to meet the following requirements:
✑ The contact information of all the users in the Europe office must not be visible to the users in the other offices.
✑ The administrators in each office must be able to control the user settings and the computer settings of the users in their respective office.
✑ The administrators in the Asia office must be able to deploy a custom application named App1. App1 requires modifications to the Active Directory schema.
The solution must use the least amount of administrative effort.
What should you include in the recommendation?
Europe.
You plan to design an Active Directory forest and domain infrastructure.
You need to recommend an Active Directory design to meet the following requirements:
✑ The contact information of all the users in the Europe office must not be visible to the users in the other offices.
✑ The administrators in each office must be able to control the user settings and the computer settings of the users in their respective office.
✑ The administrators in the Asia office must be able to deploy a custom application named App1. App1 requires modifications to the Active Directory schema.
The solution must use the least amount of administrative effort.
What should you include in the recommendation?
- AOne forest that contains four domains
- BFour forests that each contain one domain
- CTwo forests that each contain one domain
- DOne forest that contains one domain
Correct Answer:
D
The most basic of all Active Directory structures is the single domain model; this type of domain structure comes with one major advantage over the other models: simplicity. A single security boundary defines the borders of the domain, and all objects are located within that boundary. The establishment of trust relationships between other domains is not necessary, and implementation of technologies such as Group Policies is made easier by the simple structure.
D
The most basic of all Active Directory structures is the single domain model; this type of domain structure comes with one major advantage over the other models: simplicity. A single security boundary defines the borders of the domain, and all objects are located within that boundary. The establishment of trust relationships between other domains is not necessary, and implementation of technologies such as Group Policies is made easier by the simple structure.
send
light_mode
delete
Question #50
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains 50 servers that run Windows Server 2008 Service Pack 2 (SP2) and 50 servers that run Windows Server 2008 R2.
You plan to implement Windows Server 2012 R2.
You need to create a report that includes the following information:
✑ The servers that run applications and services that can be moved to Windows Server 2012 R2
✑ The servers that have hardware that can run Windows Server 2012 R2
✑ The servers that are suitable to be converted to virtual machines hosted on Hyper-V hosts that run Windows Server 2012 R2
Solution: From an existing server, you run the Microsoft Application Compatibility Toolkit (ACT).
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains 50 servers that run Windows Server 2008 Service Pack 2 (SP2) and 50 servers that run Windows Server 2008 R2.
You plan to implement Windows Server 2012 R2.
You need to create a report that includes the following information:
✑ The servers that run applications and services that can be moved to Windows Server 2012 R2
✑ The servers that have hardware that can run Windows Server 2012 R2
✑ The servers that are suitable to be converted to virtual machines hosted on Hyper-V hosts that run Windows Server 2012 R2
Solution: From an existing server, you run the Microsoft Application Compatibility Toolkit (ACT).
Does this meet the goal?
- AYes
- BNo
Correct Answer:
B
With the ACT, you can:
✑ Analyze your portfolio of applications, websites, and computers
✑ Evaluate operating system deployments, the impact of operating system updates, and your compatibility with websites
✑ Centrally manage compatibility evaluators and configuration settings
✑ Rationalize and organize applications, websites, and computers
✑ Prioritize application compatibility efforts with filtered reporting
✑ Add and manage issues and solutions for your enterprise-computing environment
✑ Deploy automated mitigations to known compatibility issues
✑ Send and receive compatibility information from the Microsoft Compatibility Exchange
Reference:
Application Compatibility Toolkit (ACT)
https://msdn.microsoft.com/en-us/library/windows/desktop/dd562082(v=vs.85).aspx
B
With the ACT, you can:
✑ Analyze your portfolio of applications, websites, and computers
✑ Evaluate operating system deployments, the impact of operating system updates, and your compatibility with websites
✑ Centrally manage compatibility evaluators and configuration settings
✑ Rationalize and organize applications, websites, and computers
✑ Prioritize application compatibility efforts with filtered reporting
✑ Add and manage issues and solutions for your enterprise-computing environment
✑ Deploy automated mitigations to known compatibility issues
✑ Send and receive compatibility information from the Microsoft Compatibility Exchange
Reference:
Application Compatibility Toolkit (ACT)
https://msdn.microsoft.com/en-us/library/windows/desktop/dd562082(v=vs.85).aspx
send
light_mode
delete
All Pages
