Huawei H12-891 Exam Practice Questions (P. 2)
- Full Access (552 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
On a CloudCampus virtualized campus network, virtual networks are defined based on services. Each virtual network corresponds to a service, and isolation needs to be manually configured between virtual networks.
send
light_mode
delete
Question #12
On a virtualized campus network, all devices in a VXLAN domain must support VXLAN.
send
light_mode
delete
Question #13
VXLAN identifies tenants using VNIs, which are 24 bits long. A tenant can have one or more VNIs, and VXLAN supports a maximum of 12 million tenants.
send
light_mode
delete
Question #14
NETCONF provides a set of mechanisms for managing network devices. What layers can NETCONF be conceptually partitioned into?
- ASecure transport layer, messages layer, operations layer, and content layer
- BSecure transport layer, messages layer, configuration layer, and content layer
- CEncrypted transport layer, messages layer, configuration layer, and content layer
- DEncrypted transport layer, messages layer, operations layer, and content layer
Correct Answer:
A
A
send
light_mode
delete
Question #15
Huawei Open Programmability System (OPS) provides openness and programmability capabilities for network devices and enables users to perform secondary development to implement customized functions. Which of the following commands can be used to view information about the OPS script installed on a network device?
- Adisplay ops script
- Bdisplay ops file
- Ccheck ops script
- Dcheck ops file
Correct Answer:
A
A
send
light_mode
delete
Question #16
In the SSH algorithm negotiation phase, the SSH server and client exchange the list of algorithms that hey support. The list of symmetric encryption algorithms of the SSH server is as follows: aes256-ctr, aes192-ctr, aes128-ctr, and aes256-cbc. The list of symmetric encryption algorithms of the SSH client is as follows: aes128-ctr, aes192-ctr, aes256-ctr, and aes256-cbc. Which of the following symmetric encryption algorithms can be used by both the SSH server and client?
send
light_mode
delete
Question #17
YANG is a data modeling language. Which of the following statements is incorrect about YANG?
- AThe YANG model is presented as a .yang file.
- BThe YANG model can be converted to an XML syntax-based YANG Independent Notation (YIN) model without any loss.
- CYANG is a modular language representing data structures in a hierarchical tree format.
- DYANG only supports built-in data type, while extended data types are not allowed.
Correct Answer:
D
D
send
light_mode
delete
Question #18
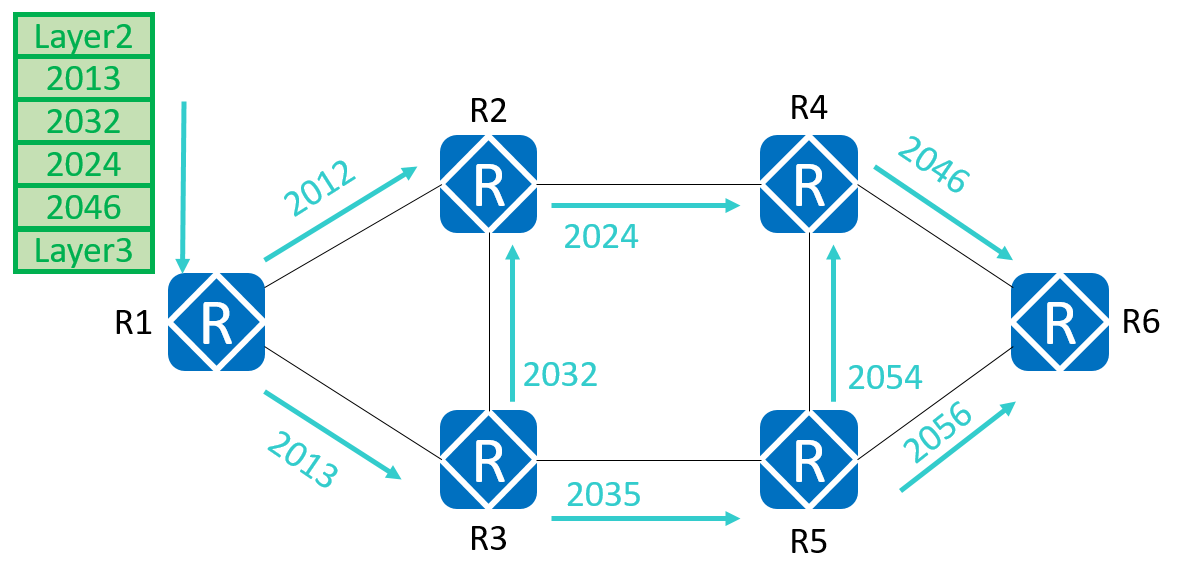
SR-MPLS is enabled on all routers. The label information encapsulated by R1 into a data packet is shown in the figure. Which of the following MPLS labels is carried in the data packet when it is sent from R2 to R4?

send
light_mode
delete
Question #19
Which of the following types of LSAs does OSPF use to support SR-MPLS?
- AType10 Opaque LSA
- BType1 Router LSA
- CType2 Network LSA
- DType7 NSSA External LSA
Correct Answer:
A
A
send
light_mode
delete
Question #20
Which of the following rules does not apply to SR-MPLS Policy design?
- AAssociate service traffic with tunnels to achieve some degree of path visualization.
- BEnsure that the traffic on each tunnel is not too heavy. Otherwise, bandwidth optimization will be difficult.
- CDeploy as many tunnels as possible, as more tunnels result in more refined service isolation and service quality assurance.
- DConsider possible network expansion in the future.
Correct Answer:
C
C
send
light_mode
delete
All Pages
