HP HPE6-A15 Exam Practice Questions (P. 1)
- Full Access (105 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
Refer to the exhibit.
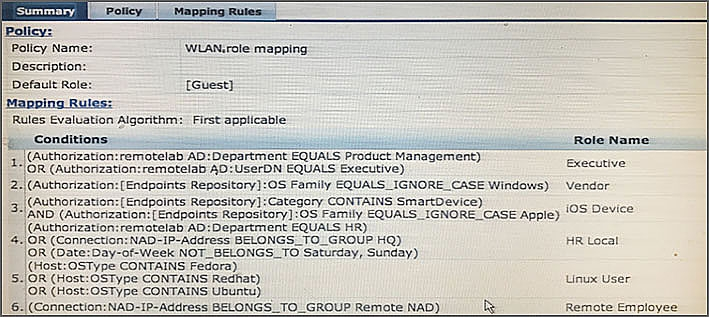
An AD user’s department attribute value is configured as "QA". The user authenticates from a laptop running MAC OS X.
Which role is assigned to the user in ClearPass?

An AD user’s department attribute value is configured as "QA". The user authenticates from a laptop running MAC OS X.
Which role is assigned to the user in ClearPass?
- AHR Local
- BRemote Employee
- C[Guest]
- DExecutive
- EIOS Device
Correct Answer:
C
None of the Listed Role Name conditions are met.
C
None of the Listed Role Name conditions are met.
send
light_mode
delete
Question #2
Refer to the exhibit.
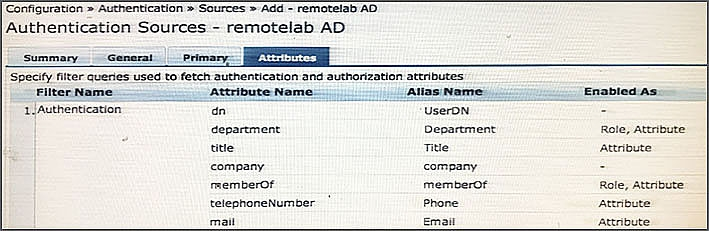
Based on the Attribute configuration shown, which statement accurately describes the status of attribute values?

Based on the Attribute configuration shown, which statement accurately describes the status of attribute values?
- AOnly the attribute values of department and memberOf can be used in role mapping policies.
- BThe attribute values of department, title, memberOf, telephoneNumber, and mail are directly applied as ClearPass.
- COnly the attribute value of company can be used in role mapping policies, not the other attributes.
- DThe attribute values of department and memberOf are directly applied as ClearPass roles.
- EOnly the attribute values of title, telephoneNumber, and mail can be used in role mapping policies.
Correct Answer:
D
D
send
light_mode
delete
Question #3
Which components can use Active Directory authorization attributes for the decision-making process? (Select two.)
- AProfiling policy
- BCertificate validation policy
- CRole Mapping policy
- DEnforcement policy
- EPosture policy
Correct Answer:
CD
C: Role Mappings Page - Rules Editor Page Parameters
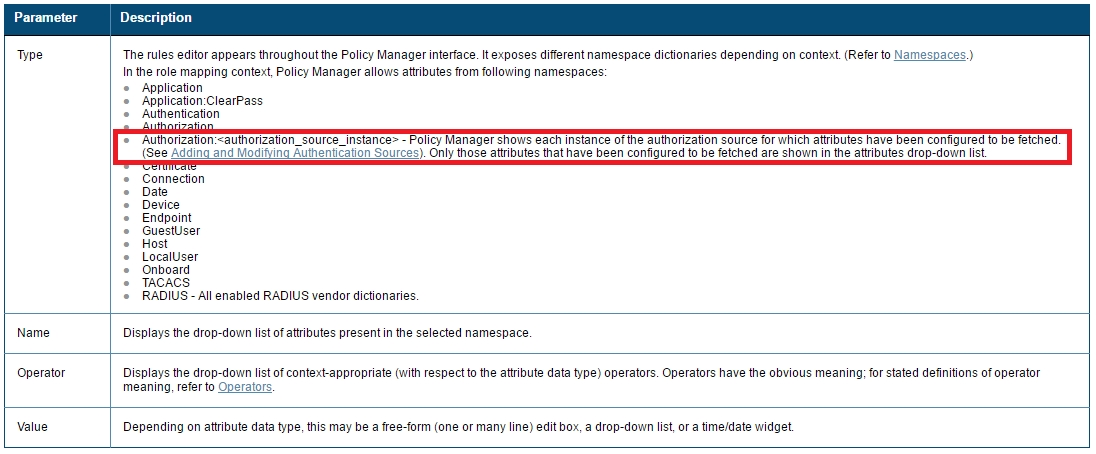
D: Enforcement Policy Attributes tab Parameters
References:
http://www.arubanetworks.com/techdocs/ClearPass/Aruba_CPPMOnlineHelp/Content/CPPM_UserGuide/identity/RoleMappingPolicies.html http://www.arubanetworks.com/techdocs/ClearPass/Aruba_CPPMOnlineHelp/Content/CPPM_UserGuide/PolicySim/PS_Enforcement_Policy.htm
CD
C: Role Mappings Page - Rules Editor Page Parameters

D: Enforcement Policy Attributes tab Parameters

References:
http://www.arubanetworks.com/techdocs/ClearPass/Aruba_CPPMOnlineHelp/Content/CPPM_UserGuide/identity/RoleMappingPolicies.html http://www.arubanetworks.com/techdocs/ClearPass/Aruba_CPPMOnlineHelp/Content/CPPM_UserGuide/PolicySim/PS_Enforcement_Policy.htm
send
light_mode
delete
Question #4
Refer to the exhibit.
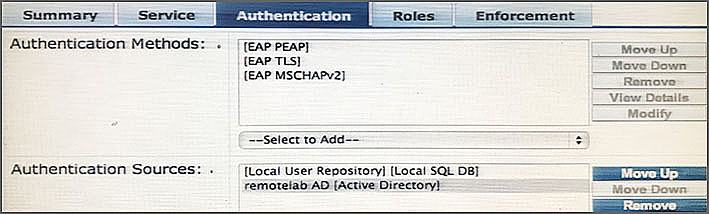
Based on the Authentication sources configuration shown, which statement accurately describes the outcome if the user is not found?

Based on the Authentication sources configuration shown, which statement accurately describes the outcome if the user is not found?
- AIf the user is not found in the remotelab AD but is present in the local user repository, a reject message is sent back to the NAD.
- BIf the user is not found in the local user repository but is present in the remotelab AD, a reject message is sent back to the NAD.
- CIf the user is not found in the local user repository a reject message is sent back to the NAD.
- DIf the user is not found in the local user repository and remotelab AD, a reject message is sent back to the NAD.
- EIf the user is not found in the local user repository a timeout message is sent back to the NAD.
Correct Answer:
D
Policy Manager looks for the device or user by executing the first filter associated with the authentication source.
After the device or user is found, Policy Manager then authenticates this entity against this authentication source. The flow is outlined below:
* On successful authentication, Policy Manager moves on to the next stage of policy evaluation, which collects role mapping attributes from the authorization sources.
* Where no authentication source is specified (for example, for unmanageable devices), Policy Manager passes the request to the next configured policy component for this service.
* If Policy Manager does not find the connecting entity in any of the configured authentication sources, it rejects the request.
References: ClearPass Policy Manager 6.5 User Guide (October 2015), page 134 https://community.arubanetworks.com/aruba/attachments/aruba/SoftwareUserReferenceGuides/52/1/ClearPass%20Policy%20Manager%206.5%20User%
20Guide.pdf
D
Policy Manager looks for the device or user by executing the first filter associated with the authentication source.
After the device or user is found, Policy Manager then authenticates this entity against this authentication source. The flow is outlined below:
* On successful authentication, Policy Manager moves on to the next stage of policy evaluation, which collects role mapping attributes from the authorization sources.
* Where no authentication source is specified (for example, for unmanageable devices), Policy Manager passes the request to the next configured policy component for this service.
* If Policy Manager does not find the connecting entity in any of the configured authentication sources, it rejects the request.
References: ClearPass Policy Manager 6.5 User Guide (October 2015), page 134 https://community.arubanetworks.com/aruba/attachments/aruba/SoftwareUserReferenceGuides/52/1/ClearPass%20Policy%20Manager%206.5%20User%
20Guide.pdf
send
light_mode
delete
Question #5
Which authorization servers are supported by ClearPass? (Select two.)
- AAruba Controller
- BLDAP server
- CCisco Controller
- DActive Directory
- EAruba Mobility Access Switch
Correct Answer:
BD
Authentication Sources can be one or more instances of the following examples:
* Active Directory
* LDAP Directory
* SQL DB
* Token Server
* Policy Manager local DB
References: ClearPass Policy Manager 6.5 User Guide (October 2015), page 114 https://community.arubanetworks.com/aruba/attachments/aruba/SoftwareUserReferenceGuides/52/1/ClearPass%20Policy%20Manager%206.5%20User%
20Guide.pdf
BD
Authentication Sources can be one or more instances of the following examples:
* Active Directory
* LDAP Directory
* SQL DB
* Token Server
* Policy Manager local DB
References: ClearPass Policy Manager 6.5 User Guide (October 2015), page 114 https://community.arubanetworks.com/aruba/attachments/aruba/SoftwareUserReferenceGuides/52/1/ClearPass%20Policy%20Manager%206.5%20User%
20Guide.pdf
send
light_mode
delete
All Pages
