GIAC GCIA Exam Practice Questions (P. 4)
- Full Access (507 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
Sandra, a novice computer user, works on Windows environment. She experiences some problem regarding bad sectors formed in a hard disk of her computer.
She wants to run CHKDSK command to check the hard disk for bad sectors and to fix the errors, if any, occurred. Which of the following switches will she use with
CHKDSK command to accomplish the task?
She wants to run CHKDSK command to check the hard disk for bad sectors and to fix the errors, if any, occurred. Which of the following switches will she use with
CHKDSK command to accomplish the task?
send
light_mode
delete
Question #32
Mark works as a Network administrator for SecureEnet Inc. His system runs on Mac OS X. He wants to boot his system from the Network Interface Controller
(NIC). Which of the following snag keys will Mark use to perform the required function?
(NIC). Which of the following snag keys will Mark use to perform the required function?
send
light_mode
delete
Question #33
Which of the following methods is used by forensic investigators to acquire an image over the network in a secure manner?
- ALinux Live CD
- BDOS boot disk
- CSecure Authentication for EnCase (SAFE)
- DEnCase with a hardware write blocker
Correct Answer:
C
C
send
light_mode
delete
Question #34
network?
Each correct answer represents a complete solution. Choose all that apply.
Each correct answer represents a complete solution. Choose all that apply.
- AFor interoperability, IPv4 addresses use the last 32 bits of IPv6 addresses.
- BIt increases the number of available IP addresses.
- CIt provides improved authentication and security.
- DIt uses 128-bit addresses.
- EIt uses longer subnet masks than those used in IPv4.
Correct Answer:
ABCD
ABCD
send
light_mode
delete
Question #35
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. John wants to redirect all TCP port
80 traffic to UDP port 40, so that he can bypass the firewall of the We-are-secure server. Which of the following tools will John use to accomplish his task?
80 traffic to UDP port 40, so that he can bypass the firewall of the We-are-secure server. Which of the following tools will John use to accomplish his task?
send
light_mode
delete
Question #36
An attacker makes an attempt against a Web server. The result is that the attack takes the form of URLs. These URLs search for a certain string that identifies an attack against the Web server.
Which IDS/IPS detection method do the URLs use to detect and prevent an attack?
Which IDS/IPS detection method do the URLs use to detect and prevent an attack?
- AAnamoly-based detection
- BPolicy-based detection
- CHoney pot detection
- DSignature-based detection
Correct Answer:
D
D
send
light_mode
delete
Question #37
HOTSPOT -
You work as a Network Administrator for McRobert Inc. The company's Windows 2000-based network is configured with Internet Security and Acceleration (ISA) on the server. You want to get notified when a TCP SYN packet is sent with a spoofed source IP address and port number that match the destination IP address and port number. Mark the alert that you will enable on the Intrusion Detection tab page of the IP Packet Filters
Properties dialog box to accomplish the task.
Hot Area:
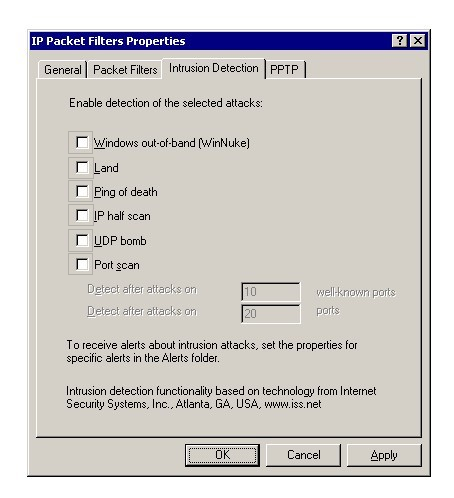
You work as a Network Administrator for McRobert Inc. The company's Windows 2000-based network is configured with Internet Security and Acceleration (ISA) on the server. You want to get notified when a TCP SYN packet is sent with a spoofed source IP address and port number that match the destination IP address and port number. Mark the alert that you will enable on the Intrusion Detection tab page of the IP Packet Filters
Properties dialog box to accomplish the task.
Hot Area:

send
light_mode
delete
send
light_mode
delete
Question #39
Computer networks and the Internet are the prime mode of Information transfer today. Which of the following is a technique used for modifying messages,
, and reducing the risk of hacking attacks during communications and message passing over the Internet?
, and reducing the risk of hacking attacks during communications and message passing over the Internet?
send
light_mode
delete
Question #40
What does a firewall check to prevent certain ports and applications from getting the packets into an Enterprise?
- AThe application layer port numbers and the transport layer headers
- BThe presentation layer headers and the session layer port numbers
- CThe network layer headers and the session layer port numbers
- DThe transport layer port numbers and the application layer headers
Correct Answer:
D
D
send
light_mode
delete
All Pages