GIAC GASF Exam Practice Questions (P. 2)
- Full Access (71 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #6
An analyst investigating a Nokia S60 Symbian device wants to know if an Adobe Flash file on the handset is compromised. Which file in the image will best target the Adobe Flash files?
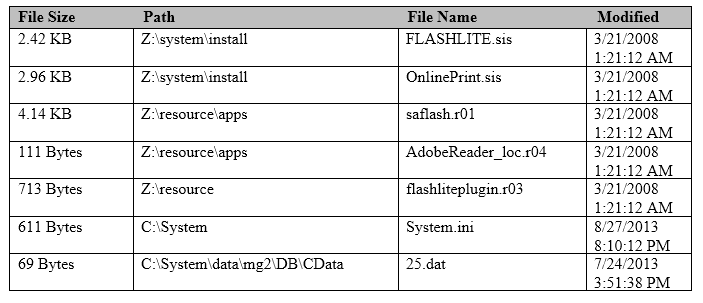

- AFLASHLITE.sis
- Bflashliteplugin.r03
- Csaflash.r01
- DOnlinePrint.sis
Correct Answer:
A
A sis.file is the package that Symbian uses to install applications on their OS compatible handsets. Knowing that you are investigating an application that is installed on the handset, first narrowing the files down to installer packages, or *.sis files, is a good starting point. Flash is an Adobe product making the most logical of the two remaining* .sis files for review, the FLASHLITE installer package. There are several other files related to "Flash" but as resource files, they provide supporting documentation and will not contain the .app file or code that was possibly malicious.
A
A sis.file is the package that Symbian uses to install applications on their OS compatible handsets. Knowing that you are investigating an application that is installed on the handset, first narrowing the files down to installer packages, or *.sis files, is a good starting point. Flash is an Adobe product making the most logical of the two remaining* .sis files for review, the FLASHLITE installer package. There are several other files related to "Flash" but as resource files, they provide supporting documentation and will not contain the .app file or code that was possibly malicious.
send
light_mode
delete
Question #7
As part of your analysis of a legacy BlackBerry device, you examine the installed applications list and it appears that no third-party applications were installed on the device. Which other file may provide you with additional information on applications that were accessed with the handset?
- ABlackBerry NV Items
- BContent Store
- CEvent logs
- DBBThumbs.dat
Correct Answer:
C
Analyzing both the Event Logs (which are accessible in Oxygen Forensic Suite) and/or the Installed Applications (which is a feature available in
Cellebrite Physical Analyzer) may lead you to additional data. If applications of interest were located in the Event Logs, a Keyword Search across the media may reveal more data related to the application.
C
Analyzing both the Event Logs (which are accessible in Oxygen Forensic Suite) and/or the Installed Applications (which is a feature available in
Cellebrite Physical Analyzer) may lead you to additional data. If applications of interest were located in the Event Logs, a Keyword Search across the media may reveal more data related to the application.
send
light_mode
delete
Question #8
Which artifact must be carved out manually when examining a file system acquisition of an Android device?
send
light_mode
delete
Question #9
When conducting forensic analysis of an associated media card, one would most often expect to find this particular file system format?
send
light_mode
delete
Question #10
Cellebrite Physical Analyzer uses Bit Defender to scan for malware by flagging files who have known bad hash values. This is an example of which type of mobile malware detection?
- ASpecific-based malware detection
- BSignature-based detection
- CBehavioral-based detection
- DCloud based malware detection
Correct Answer:
B
Reference:
https://security.stackexchange.com/questions/95186/what-is-the-precise-difference-between-a-signature-based-vs-behavior-based-antiv
B
Reference:
https://security.stackexchange.com/questions/95186/what-is-the-precise-difference-between-a-signature-based-vs-behavior-based-antiv
send
light_mode
delete
All Pages
