Fortinet NSE8 Exam Practice Questions (P. 2)
- Full Access (65 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #6
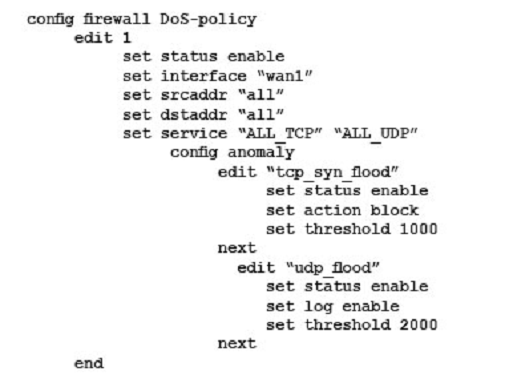
A company wants to protect against Denial of Service attacks and has launched a new project. They want to block the attacks that go above a certain threshold and for some others they are just trying to get a baseline of activity for those types of attacks so they are letting the traffic pass through without action. Given the following:
- The interface to the Internet is on WAN1.
- There is no requirement to specify which addresses are being protected or protected from.
- The protection is to extend to all services.
- The tcp_syn_flood attacks are to be recorded and blocked.
- The udp_flood attacks are to be recorded but not blocked.
- The tcp_syn_flood attacks threshold is to be changed from the default to 1000.
The exhibit shows the current DoS-policy.
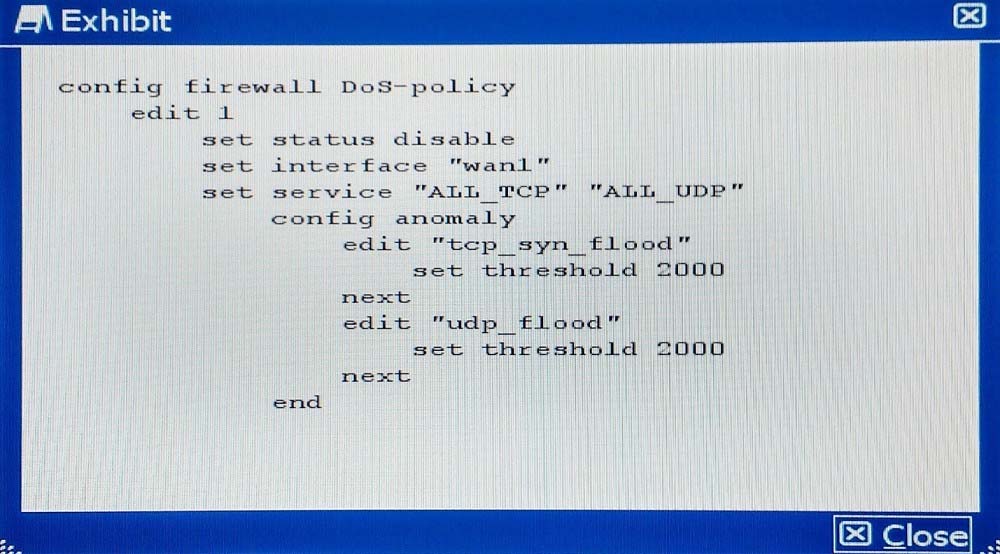
Which policy will implement the project requirements?
A)
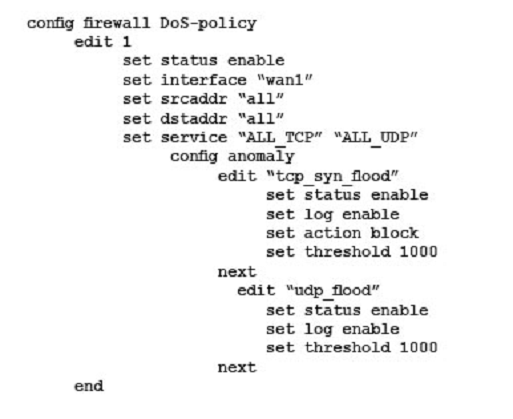
B)
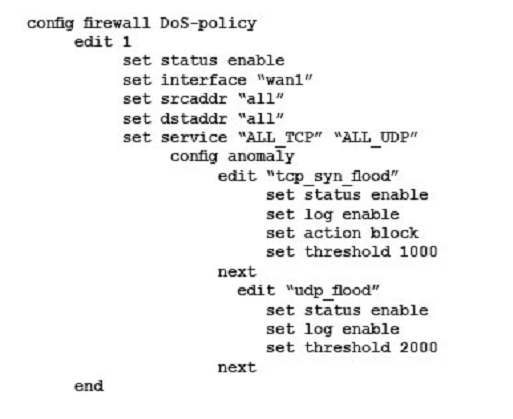
C)
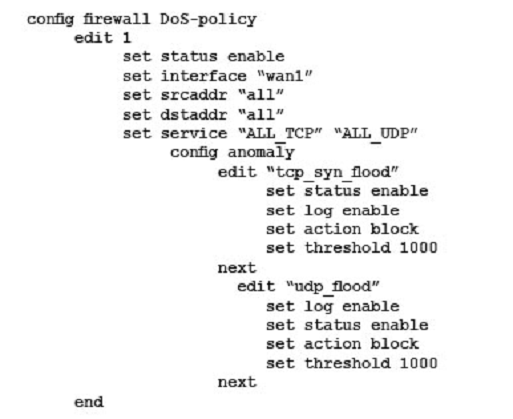
D)
- The interface to the Internet is on WAN1.
- There is no requirement to specify which addresses are being protected or protected from.
- The protection is to extend to all services.
- The tcp_syn_flood attacks are to be recorded and blocked.
- The udp_flood attacks are to be recorded but not blocked.
- The tcp_syn_flood attacks threshold is to be changed from the default to 1000.
The exhibit shows the current DoS-policy.

Which policy will implement the project requirements?
A)

B)

C)

D)

- AOption A
- BOption B
- COption C
- DOption D
Correct Answer:
BD
B&D both have same policy which fulfills the above criteria.
http://help.fortinet.com/fos50hlp/52data/Content/FortiOS/fortigate-firewall-52/Examples/Example-%20DoS%20Policy.htm
BD
B&D both have same policy which fulfills the above criteria.
http://help.fortinet.com/fos50hlp/52data/Content/FortiOS/fortigate-firewall-52/Examples/Example-%20DoS%20Policy.htm
send
light_mode
delete
Question #7
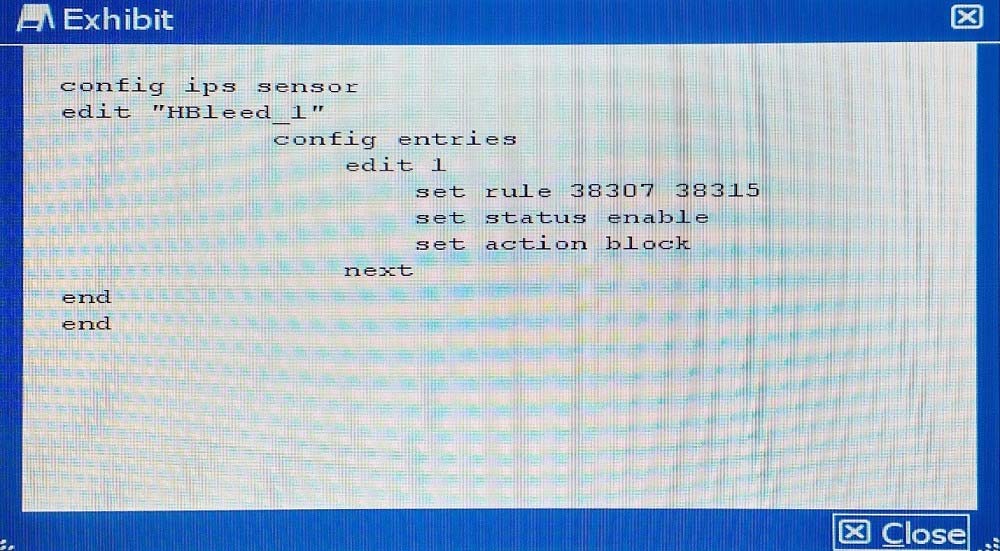
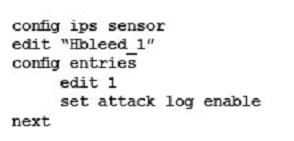
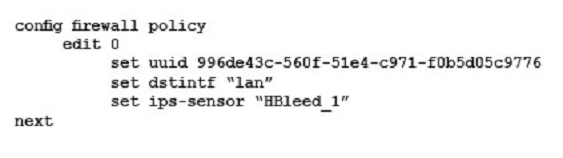
Your security department has requested that you implement the OpenSSL.TLS.Heartbeat.Information.Disclosure signature using an IPS sensor to scan traffic destined to the FortiGate. You must log all packets that attempt to exploit this vulnerability.
Referring to the exhibit, which two configurations are required to accomplish this task? (Choose two.)
A)

B)
C)
D)
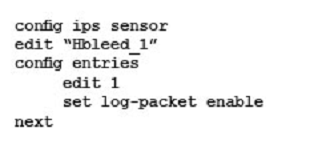
Referring to the exhibit, which two configurations are required to accomplish this task? (Choose two.)

A)

B)

C)

D)

- AOption AMost Voted
- BOption B
- COption C
- DOption DMost Voted
Correct Answer:
AB
http://defadhil.blogspot.in/2014/04/how-to-protect-fortigate-from.html
AB
http://defadhil.blogspot.in/2014/04/how-to-protect-fortigate-from.html
send
light_mode
delete
Question #8
Which command syntax would you use to configure the serial number of a FortiGate as its host name?
A)
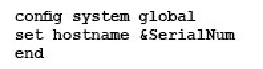
B)
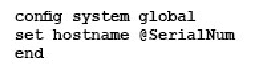
C)
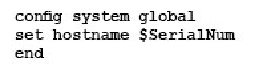
D)
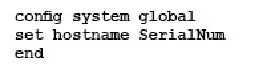
A)

B)

C)

D)

- AOption A
- BOption B
- COption C
- DOption D
Correct Answer:
C
http://docs.fortinet.com/uploaded/files/2002/FortiOS%20Handbook%20-%20System%20Administration%205.2.pdf
C
http://docs.fortinet.com/uploaded/files/2002/FortiOS%20Handbook%20-%20System%20Administration%205.2.pdf
send
light_mode
delete
Question #9
Referring to the exhibit, which statement is true?
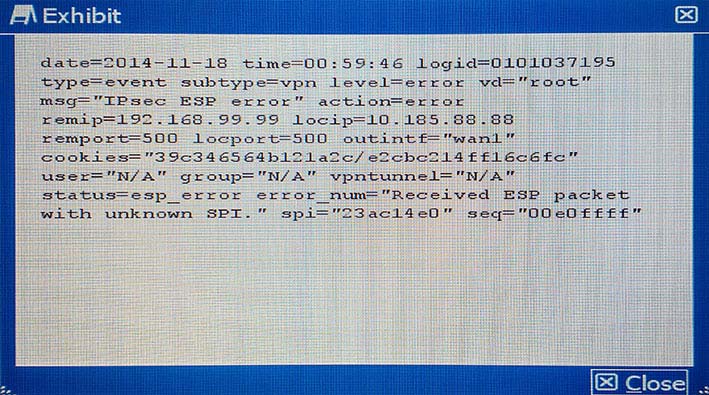

- AThe packet failed the HMAC validation.
- BThe packet did not match any of the local IPsec SAs.Most Voted
- CThe packet was protected with an unsupported encryption algorithm.
- DThe IPsec negotiation failed because the SPI was unknown.
Correct Answer:
A
http://kb.fortinet.com/kb/viewContent.do?externalId=FD33101
A
http://kb.fortinet.com/kb/viewContent.do?externalId=FD33101
send
light_mode
delete
Question #10
You are asked to establish a VPN tunnel with a service provider using a third-party VPN device. The service provider has assigned subnet 30.30.30.0/24 for your outgoing traffic going towards the services hosted by the provider on network 20.20.20.0/24. You have multiple computers which will be accessing the remote services hosted by the service provider.
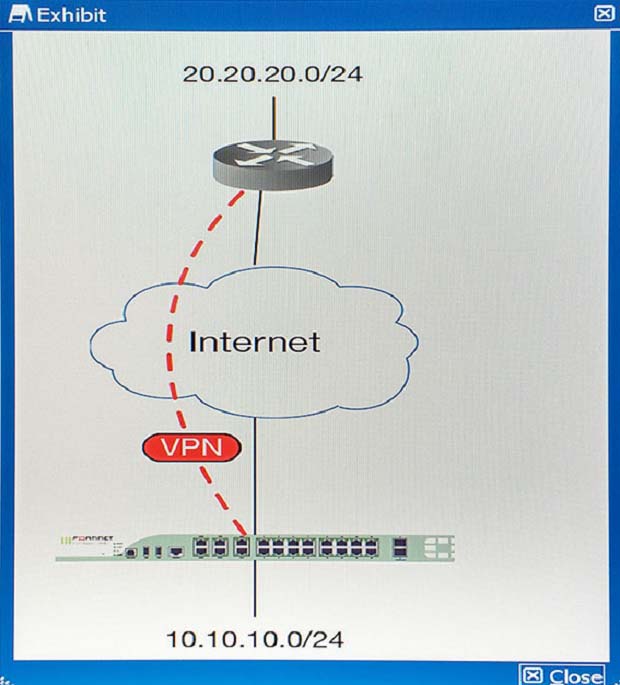
Which three configuration components meet these requirements? (Choose three.)

Which three configuration components meet these requirements? (Choose three.)
- AConfigure an IP Pool of type Overload for range 30.30.30.10-30.30.30.10. Enable NAT on a policy from your LAN forwards the VPN tunnel and select that pool.
- BConfigure IPsec phase 2 proxy IDs for a source of 10.10.10.0/24 and destination of 20.20.20.0/24.
- CConfigure an IP Pool of Type One-to-One for range 30.30.30.10-30.30.30.10. Enable NAT on a policy from your LAN towards the VPN tunnel and select that pool.
- DConfigure a static route towards the VPN tunnel for 20.20.20.0/24.
- EConfigure IPsec phase 2 proxy IDs for a source of 30.30.30.0/24 and destination of 20.20.20.0/24.
Correct Answer:
CDE
CDE
send
light_mode
delete
All Pages
