Fortinet NSE4_FGT-6.2 Exam Practice Questions (P. 3)
- Full Access (119 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
Consider a new IPsec deployment with the following criteria:
✑ All satellite offices must connect to the two HQ sites.
✑ The satellite offices do not need to communicate directly with other satellite offices.
✑ Backup VPN is not required.
✑ The design should minimize the number of tunnels being configured.
Which topology should you use to satisfy all of the requirements?
✑ All satellite offices must connect to the two HQ sites.
✑ The satellite offices do not need to communicate directly with other satellite offices.
✑ Backup VPN is not required.
✑ The design should minimize the number of tunnels being configured.
Which topology should you use to satisfy all of the requirements?
send
light_mode
delete
Question #12
What criteria does FortiGate use to look for a matching firewall policy to process traffic? (Choose two.)
- AServices defined in the firewall policy.
- BIncoming and outgoing interfaces
- CHighest to lowest priority defined in the firewall policy.
- DLowest to highest policy ID number.
Correct Answer:
AB
AB
send
light_mode
delete
Question #13
Refer to the exhibit.
You are configuring the root FortiGate to implement the Security Fabric. You are configuring port10 to communicate with a downstream FortiGate. The exhibit shows the default Edit Interface.
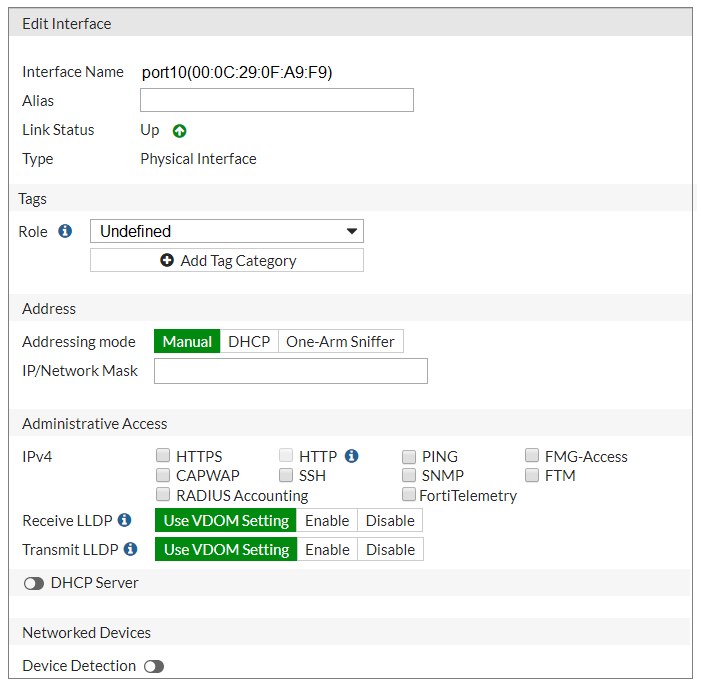
When configuring the root FortiGate to communicate with a downstream FortiGate, which two settings must you configure? (Choose two.)
You are configuring the root FortiGate to implement the Security Fabric. You are configuring port10 to communicate with a downstream FortiGate. The exhibit shows the default Edit Interface.

When configuring the root FortiGate to communicate with a downstream FortiGate, which two settings must you configure? (Choose two.)
- AEnable Device Detection
- BAdministrative Access: FortiTelemetry.
- CIP/Network Mask.
- DRole: Security Fabric.
Correct Answer:
BC
BC
send
light_mode
delete
Question #14
Which two statements about NTLM authentication are correct? (Choose two.)
- AIt requires DC agents on every domain controller when used in multidomain environments.
- BIt is useful when users log in to DCs that are not monitored by a collector agent.
- CIt requires NTLM-enabled web browsers.
- DIt takes over as the primary authentication method when configured alongside FSSO.
Correct Answer:
BC
Reference:
https://www.fortinetguru.com/2016/07/configuring-authenticated-access/12/
BC
Reference:
https://www.fortinetguru.com/2016/07/configuring-authenticated-access/12/
send
light_mode
delete
Question #15
Refer to the exhibit.
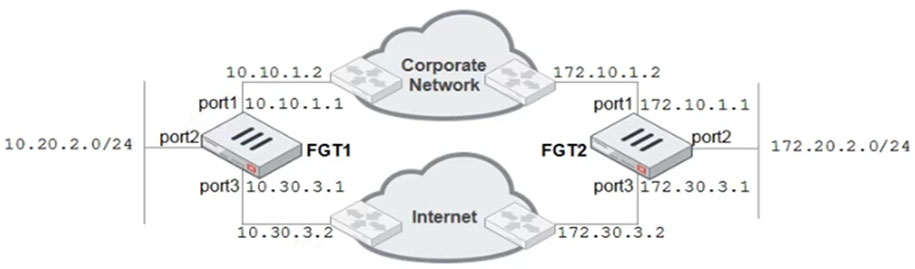
A firewall administrator must configure equal cost multipath (ECMP) routing on FGT1 to ensure both port1 and port3 links are used, at the same time, for all traffic destined for 172.20.2.0/24.
Given the network diagram shown in the exhibit, which two static routes will satisfy this requirement on FGT1? (Choose two.)

A firewall administrator must configure equal cost multipath (ECMP) routing on FGT1 to ensure both port1 and port3 links are used, at the same time, for all traffic destined for 172.20.2.0/24.
Given the network diagram shown in the exhibit, which two static routes will satisfy this requirement on FGT1? (Choose two.)
- A172.20.2.0/24 [1/0] via 10.10.1.2, port1 [0/0]
- B172.20.2.0/24 [25/0] via 10.30.3.2, port3 [5/0]
- C172.20.2.0/24 [25/0] via 10.10.1.2, port1 [5/0]
- D172.20.2.0/24 [1/150] via 10.30.3.2, port3 [10/0]
Correct Answer:
BC
BC
send
light_mode
delete
All Pages
