Fortinet NSE4-5.4 Exam Practice Questions (P. 5)
- Full Access (575 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
How does FortiGate verify the login credentials of a remote LDAP user?
- AFortiGate sends the user entered credentials to the LDAP server for authentication.
- BFortiGate re-generates the algorithm based on the login credentials and compares it against the algorithm stored on the LDAP server.
- CFortiGate queries its own database for credentials.
- DFortiGate queries the LDAP server for credentials.
Correct Answer:
A
A
send
light_mode
delete
Question #42
An administrator has enabled proxy-based antivirus scanning and configured the following settings:

Which statement about the above configuration is true?

Which statement about the above configuration is true?
- AFiles bigger than 10 MB are not scanned for viruses and will be blocked.
- BFortiGate scans only the first 10 MB of any file.
- CFiles bigger than 10 MB are sent to the heuristics engine for scanning.
- DFortiGate scans the files in chunks of 10 MB.
Correct Answer:
A
A
send
light_mode
delete
Question #43
Examine this output from the diagnose sys top command:

Which statements about the output are true? (Choose two.)

Which statements about the output are true? (Choose two.)
- Asshd is the process consuming most memory
- Bsshd is the process consuming most CPU
- CAll the processes listed are in sleeping state
- DThe sshd process is using 123 pages of memory
Correct Answer:
BC
BC
send
light_mode
delete
Question #44
An administrator has created a custom IPS signature. Where does the custom IPS signature have to be applied?
- AIn an IPS sensor
- BIn an interface.
- CIn a DoS policy.
- DIn an application control profile.
Correct Answer:
A
I create a custom signature then I try to add and appear only in IPS sensor.
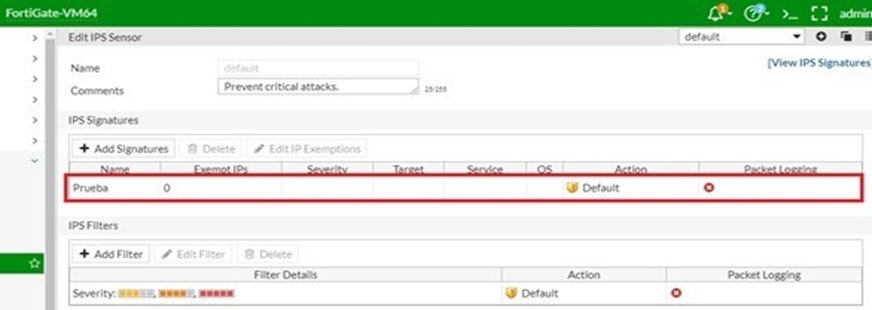
A
I create a custom signature then I try to add and appear only in IPS sensor.

send
light_mode
delete
Question #45
An administrator wants to configure a FortiGate as a DNS server. The FortiGate must use its DNS database first, and then relay all irresolvable queries to an external DNS server. Which of the following DNS method must you use?
- ANon-recursive
- BRecursive
- CForward to primary and secondary DNS
- DForward to system DNS
Correct Answer:
B
B
send
light_mode
delete
Question #46
Which statements about high availability (HA) for FortiGates are true? (Choose two.)
- AVirtual clustering can be configured between two FortiGate devices with multiple VDOM.
- BHeartbeat interfaces are not required on the primary device.
- CHA management interface settings are synchronized between cluster members.
- DSessions handled by UTM proxy cannot be synchronized.
Correct Answer:
AC
AC
send
light_mode
delete
Question #47
Which of the following statements about central NAT are true? (Choose two.)
- AIP tool references must be removed from existing firewall policies before enabling central NAT.
- BCentral NAT can be enabled or disabled from the CLI only.
- CSource NAT, using central NAT, requires at least one central SNAT policy.
- DDestination NAT, using central NAT, requires a VIP object as the destination address in a firewall policy.
Correct Answer:
AB
AB
send
light_mode
delete
Question #48
Which statement about the FortiGuard services for the FortiGate is true?
- AAntivirus signatures are downloaded locally on the FortiGate.
- BFortiGate downloads IPS updates using UDP port 53 or 8888.
- CFortiAnalyzer can be configured as a local FDN to provide antivirus and IPS updates.
- DThe web filtering database is downloaded locally on the FortiGate.
Correct Answer:
A
A

send
light_mode
delete
Question #49
Which statements about antivirus scanning using flow-based full scan are true? (Choose two.)
- AThe antivirus engine starts scanning a file after the last packet arrives.
- BIt does not support FortiSandbox inspection.
- CFortiGate can insert the block replacement page during the first connection attempt only if a virus is detected at the start of the TCP stream.
- DIt uses the compact antivirus database.
Correct Answer:
AC
AC
send
light_mode
delete
Question #50
An administrator has configured a route-based IPsec VPN between two FortiGates. Which statement about this IPsec VPN configuration is true?
- AA phase 2 configuration is not required.
- BThis VPN cannot be used as part of a hub and spoke topology.
- CThe IPsec firewall policies must be placed at the top of the list.
- DA virtual IPsec interface is automatically created after the phase 1 configuration is completed.
Correct Answer:
D
D
send
light_mode
delete
All Pages
