Fortinet FCSS_EFW_AD-7.4 Exam Practice Questions (P. 2)
- Full Access (57 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #6
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
- AFortiGate has a predefined list of all IPs and ports for specific applications downloaded from FortiGuard.
- BThe ISDB blocks the IP addresses and ports of an application predefined by FortiGuard.
- CThe ISDB works in proxy mode, allowing the analysis of packets in layers 3 and 4 of the OSI model.
- DThe ISDB limits access by URL and domain.
send
light_mode
delete
Question #7
Refer to the exhibits.
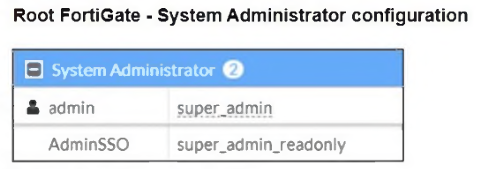
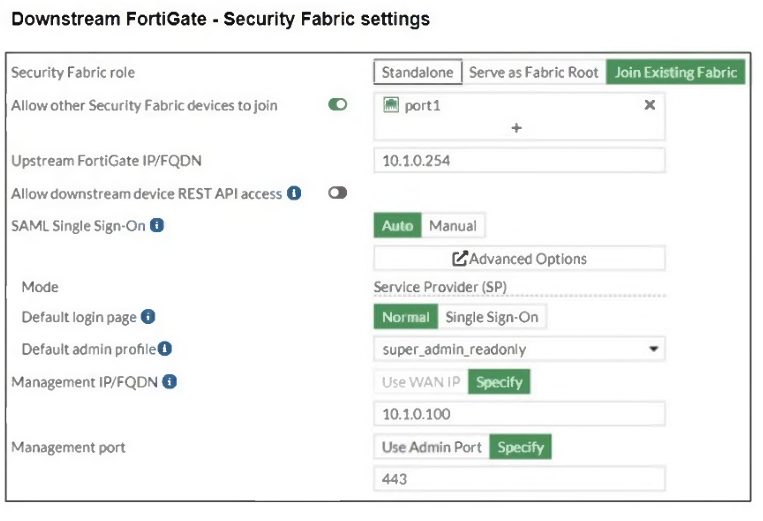
The Administrators section of a root FortiGate device and the Security Fabric Settings section of a downstream FortiGate device are shown.
When prompted to sign in with Security Fabric in the downstream FortiGate device, a user enters the AdminSSO credentials.
What is the next status for the user?


The Administrators section of a root FortiGate device and the Security Fabric Settings section of a downstream FortiGate device are shown.
When prompted to sign in with Security Fabric in the downstream FortiGate device, a user enters the AdminSSO credentials.
What is the next status for the user?
- AThe user is prompted to create an SSO administrator account for AdminSSO.
- BThe user receives an authentication failure message.
- CThe user accesses the downstream FortiGate with super_admin_readonly privileges.
- DThe user accesses the downstream FortiGate with super_admin privileges.
send
light_mode
delete
Question #8
A user reports that their computer was infected with malware after accessing a secured HTTPS website. However, when the administrator checks the FortiGate logs, they do not see that the website was detected as insecure despite having an SSL certificate and correct profiles applied on the policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
- AThe administrator must enable reputable websites to allow only SSL/TLS websites rated by FortiGuard web filter.
- BThe administrator must enable URL extraction from SNI on the SSL certificate inspection to ensure the TLS three-way handshake is correctly analyzed by FortiGate.
- CThe administrator must enable DNS over TLS to protect against fake Server Name Indication (SNI) that cannot be analyzed in common DNS requests on HTTPS websites.
- DThe administrator must enable full SSL inspection in the SSL/SSH Inspection Profile to decrypt packets and ensure they are analyzed as expected.
send
light_mode
delete
Question #9
Refer to the exhibit, which shows an ADVPN network.
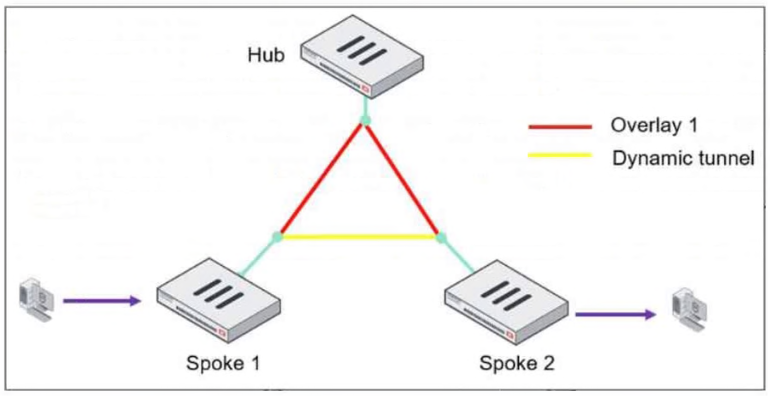
The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?

The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?
send
light_mode
delete
Question #10
What is the initial step performed by FortiGate when handling the first packets of a session?
- AInstallation of the session key in the network processor (NP)
- BData encryption and decryption
- CSecurity inspections such as ACL, HPE, and IP integrity header checking
- DOffloading the packets directly to the content processor (CP)
send
light_mode
delete
All Pages
