CompTIA SY0-601 Exam Practice Questions (P. 5)
- Full Access (860 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
A company wants to restrict emailing of PHI documents. The company is implementing a DLP solution. In order to restrict PHI documents, which of the following should be performed FIRST?
send
light_mode
delete
Question #42
A security analyst is investigating some users who are being redirected to a fake website that resembles www.comptia.org. The following output was found on the naming server of the organization:
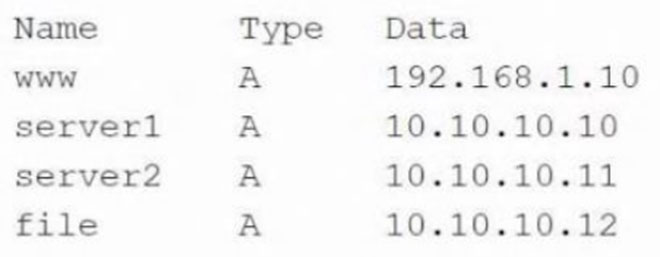
Which of the following attacks has taken place?

Which of the following attacks has taken place?
- ADomain reputation
- BDomain hijacking
- CDisassociation
- DDNS poisoningMost Voted
Correct Answer:
B
B
send
light_mode
delete
Question #43
Which of the following describes the continuous delivery software development methodology?
send
light_mode
delete
Question #44
Which of the following is the BEST example of a cost-effective physical control to enforce a USB removable media restriction policy?
- APutting security/antitamper tape over USB ports, logging the port numbers, and regularly inspecting the ports
- BImplementing a GPO that will restrict access to authorized USB removable media and regularly verifying that it is enforcedMost Voted
- CPlacing systems into locked, key-controlled containers with no access to the USB ports
- DInstalling an endpoint agent to detect connectivity of USB and removable media
Correct Answer:
B
B
send
light_mode
delete
Question #45
A company suspects that some corporate accounts were compromised. The number of suspicious logins from locations not recognized by the users is increasing.
Employees who travel need their accounts protected without the risk of blocking legitimate login requests that may be made over new sign-in properties. Which of the following security controls can be implemented?
Employees who travel need their accounts protected without the risk of blocking legitimate login requests that may be made over new sign-in properties. Which of the following security controls can be implemented?
- AEnforce MFA when an account request reaches a risk threshold.Most Voted
- BImplement geofencing to only allow access from headquarters.
- CEnforce time-based login requests that align with business hours.
- DShift the access control scheme to a discretionary access control.
Correct Answer:
A
A
send
light_mode
delete
Question #46
An organization wants to participate in threat intelligence information sharing with peer groups. Which of the following would MOST likely meet the organization's requirement?
- APerform OSINT investigations.
- BSubscribe to threat intelligence feeds.
- CSubmit RFCs.
- DImplement a TAXII server.Most Voted
Correct Answer:
D
D
send
light_mode
delete
Question #47
Which of the following is the MOST effective control against zero-day vulnerabilities?
- ANetwork segmentationMost Voted
- BPatch management
- CIntrusion prevention system
- DMultiple vulnerability scanners
Correct Answer:
C
C
send
light_mode
delete
Question #48
Which of the following is the GREATEST security concern when outsourcing code development to third-party contractors for an internet-facing application?
- AIntellectual property theft
- BElevated privileges
- CUnknown backdoorMost Voted
- DQuality assurance
Correct Answer:
C
C
send
light_mode
delete
Question #49
An organization has hired a red team to simulate attacks on its security posture. Which of the following will the blue team do after detecting an IoC?
- AReimage the impacted workstations.
- BActivate runbooks for incident response.Most Voted
- CConduct forensics on the compromised system.
- DConduct passive reconnaissance to gather information.
Correct Answer:
C
C
send
light_mode
delete
Question #50
An amusement park is implementing a biometric system that validates customers' fingerprints to ensure they are not sharing tickets. The park's owner values customers above all and would prefer customers' convenience over security. For this reason, which of the following features should the security team prioritize
FIRST?
FIRST?
send
light_mode
delete
All Pages
