CompTIA SY0-401 Exam Practice Questions (P. 4)
- Full Access (1780 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
A company has proprietary mission critical devices connected to their network which are configured remotely by both employees and approved customers. The administrator wants to monitor device security without changing their baseline configuration. Which of the following should be implemented to secure the devices without risking availability?
- AHost-based firewall
- BIDS
- CIPS
- DHoneypot
Correct Answer:
B
An intrusion detection system (IDS) is a device or software application that monitors network or system activities for malicious activities or policy violations and produces reports to a management station. IDS come in a variety of "flavors" and approach the goal of detecting suspicious traffic in different ways. There are network based (NIDS) and host based (HIDS) intrusion detection systems. Some systems may attempt to stop an intrusion attempt but this is neither required nor expected of a monitoring system. Intrusion detection and prevention systems (IDPS) are primarily focused on identifying possible incidents, logging information about them, and reporting attempts. In addition, organizations use IDPSes for other purposes, such as identifying problems with security policies, documenting existing threats and deterring individuals from violating security policies. IDPSes have become a necessary addition to the security infrastructure of nearly every organization.
IDPSes typically record information related to observed events, notify security administrators of important observed events and produce reports. Many IDPSes can also respond to a detected threat by attempting to prevent it from succeeding. They use several response techniques, which involve the IDPS stopping the attack itself, changing the security environment (e.g. reconfiguring a firewall) or changing the attack's content.
Incorrect Answers:
A: The question states: The administrator wants to monitor device security without changing their baseline configuration. Installing and configure host-based firewalls would change the baseline configuration. A host-based or personal software firewall can often limit communications to only approved applications and protocols and can usually prevent externally initiated connections. It will not monitor device security.
C: The question states: The administrator wants to monitor device security without changing their baseline configuration. The word monitor is an important distinction. It doesnt say block or prevent. The main functions of intrusion prevention systems are to identify malicious activity, log information about this activity, attempt to block/stop it, and report it. The main differences are, unlike intrusion detection systems, intrusion prevention systems are placed in-line and are able to actively prevent/block intrusions that are detected.
D: A honeypot is a system whose purpose it is to be attacked. An administrator can watch and study the attack to research current attack methodologies. A honeypot is not used to monitor device security.
References:
http://en.wikipedia.org/wiki/Intrusion_detection_system
, Sybex, Indianapolis, 2014, pp. 213, 246
http://en.wikipedia.org/wiki/Intrusion_prevention_system
B
An intrusion detection system (IDS) is a device or software application that monitors network or system activities for malicious activities or policy violations and produces reports to a management station. IDS come in a variety of "flavors" and approach the goal of detecting suspicious traffic in different ways. There are network based (NIDS) and host based (HIDS) intrusion detection systems. Some systems may attempt to stop an intrusion attempt but this is neither required nor expected of a monitoring system. Intrusion detection and prevention systems (IDPS) are primarily focused on identifying possible incidents, logging information about them, and reporting attempts. In addition, organizations use IDPSes for other purposes, such as identifying problems with security policies, documenting existing threats and deterring individuals from violating security policies. IDPSes have become a necessary addition to the security infrastructure of nearly every organization.
IDPSes typically record information related to observed events, notify security administrators of important observed events and produce reports. Many IDPSes can also respond to a detected threat by attempting to prevent it from succeeding. They use several response techniques, which involve the IDPS stopping the attack itself, changing the security environment (e.g. reconfiguring a firewall) or changing the attack's content.
Incorrect Answers:
A: The question states: The administrator wants to monitor device security without changing their baseline configuration. Installing and configure host-based firewalls would change the baseline configuration. A host-based or personal software firewall can often limit communications to only approved applications and protocols and can usually prevent externally initiated connections. It will not monitor device security.
C: The question states: The administrator wants to monitor device security without changing their baseline configuration. The word monitor is an important distinction. It doesnt say block or prevent. The main functions of intrusion prevention systems are to identify malicious activity, log information about this activity, attempt to block/stop it, and report it. The main differences are, unlike intrusion detection systems, intrusion prevention systems are placed in-line and are able to actively prevent/block intrusions that are detected.
D: A honeypot is a system whose purpose it is to be attacked. An administrator can watch and study the attack to research current attack methodologies. A honeypot is not used to monitor device security.
References:
http://en.wikipedia.org/wiki/Intrusion_detection_system
, Sybex, Indianapolis, 2014, pp. 213, 246
http://en.wikipedia.org/wiki/Intrusion_prevention_system
send
light_mode
delete
Question #32
SIMULATION -
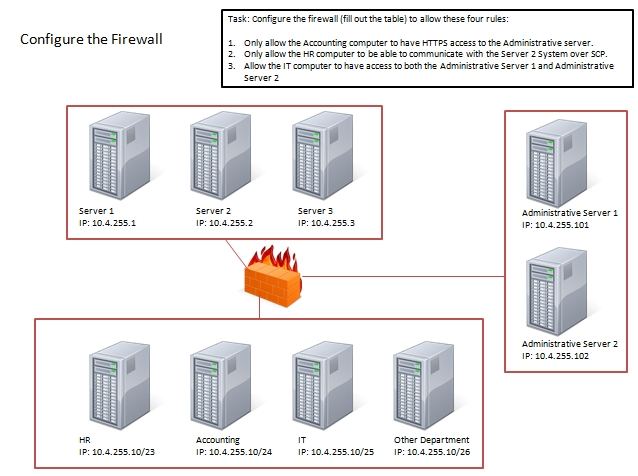
Task: Configure the firewall (fill out the table) to allow these three rules:
1. Only allow the accounting computer to have HTTPS access to the Administrative server.
2. Only allow the HT computer to be able to communicate with the Server2 System over SCP.
3. Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2
Task: Configure the firewall (fill out the table) to allow these three rules:
1. Only allow the accounting computer to have HTTPS access to the Administrative server.
2. Only allow the HT computer to be able to communicate with the Server2 System over SCP.
3. Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2


Correct Answer:
See the solution below.
Firewall rules act like ACLs, and they are used to dictate what traffic can pass between the firewall and the internal network. Three possible actions can be taken based on the rules criteria:
✑ Block the connection
✑ Allow the connection
✑ Allow the connection only if it is secured
TCP is responsible for providing a reliable, one-to-one, connection-oriented session. TCP establishes a connection and ensures that the other end receives any packets sent. Two hosts communicate packet results with each other. TCP also ensures that packets are decoded and sequenced properly. This connection is persistent during the session. When the session ends, the connection is torn down.
UDP provides an unreliable connectionless communication method between hosts. UDP is considered a best-effort protocol, but its considerably faster than TCP.
The sessions dont establish a synchronized session like the kind used in TCP, and UDP doesnt guarantee error-free communications. The primary purpose of
UDP is to send small packets of information. The application is responsible for acknowledging the correct reception of the data.
Port 22 is used by both SSH and SCP with UDP.
Port 443 is used for secure web connections HTTPS and is a TCP port.
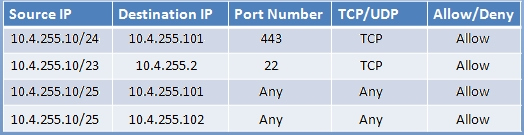
Thus, to make sure only the Accounting computer has HTTPS access to the Administrative server you should use TCP port 443 and set the rule to allow communication between 10.4.255.10/24 (Accounting) and 10.4.255.101 (Administrative server1)
Thus, to make sure that only the HR computer has access to Server2 over SCP you need use of TCP port 22 and set the rule to allow communication between
10.4.255.10/23 (HR) and 10.4.255.2 (server2)
Thus, to make sure that the IT computer can access both the Administrative servers you need to use a port and accompanying port number and set the rule to allow communication between:
✑ 10.4.255.10.25 (IT computer) and 10.4.255.101 (Administrative server1)
✑ 10.4.255.10.25 (IT computer) and 10.4.255.102 (Administrative server2)
References:
, 6th Edition, Sybex, Indianapolis, 2014, pp. 77, 83, 96, 157
See the solution below.

Firewall rules act like ACLs, and they are used to dictate what traffic can pass between the firewall and the internal network. Three possible actions can be taken based on the rules criteria:
✑ Block the connection
✑ Allow the connection
✑ Allow the connection only if it is secured
TCP is responsible for providing a reliable, one-to-one, connection-oriented session. TCP establishes a connection and ensures that the other end receives any packets sent. Two hosts communicate packet results with each other. TCP also ensures that packets are decoded and sequenced properly. This connection is persistent during the session. When the session ends, the connection is torn down.
UDP provides an unreliable connectionless communication method between hosts. UDP is considered a best-effort protocol, but its considerably faster than TCP.
The sessions dont establish a synchronized session like the kind used in TCP, and UDP doesnt guarantee error-free communications. The primary purpose of
UDP is to send small packets of information. The application is responsible for acknowledging the correct reception of the data.
Port 22 is used by both SSH and SCP with UDP.
Port 443 is used for secure web connections HTTPS and is a TCP port.
Thus, to make sure only the Accounting computer has HTTPS access to the Administrative server you should use TCP port 443 and set the rule to allow communication between 10.4.255.10/24 (Accounting) and 10.4.255.101 (Administrative server1)
Thus, to make sure that only the HR computer has access to Server2 over SCP you need use of TCP port 22 and set the rule to allow communication between
10.4.255.10/23 (HR) and 10.4.255.2 (server2)
Thus, to make sure that the IT computer can access both the Administrative servers you need to use a port and accompanying port number and set the rule to allow communication between:
✑ 10.4.255.10.25 (IT computer) and 10.4.255.101 (Administrative server1)
✑ 10.4.255.10.25 (IT computer) and 10.4.255.102 (Administrative server2)
References:
, 6th Edition, Sybex, Indianapolis, 2014, pp. 77, 83, 96, 157
send
light_mode
delete
Question #33
HOTSPOT -
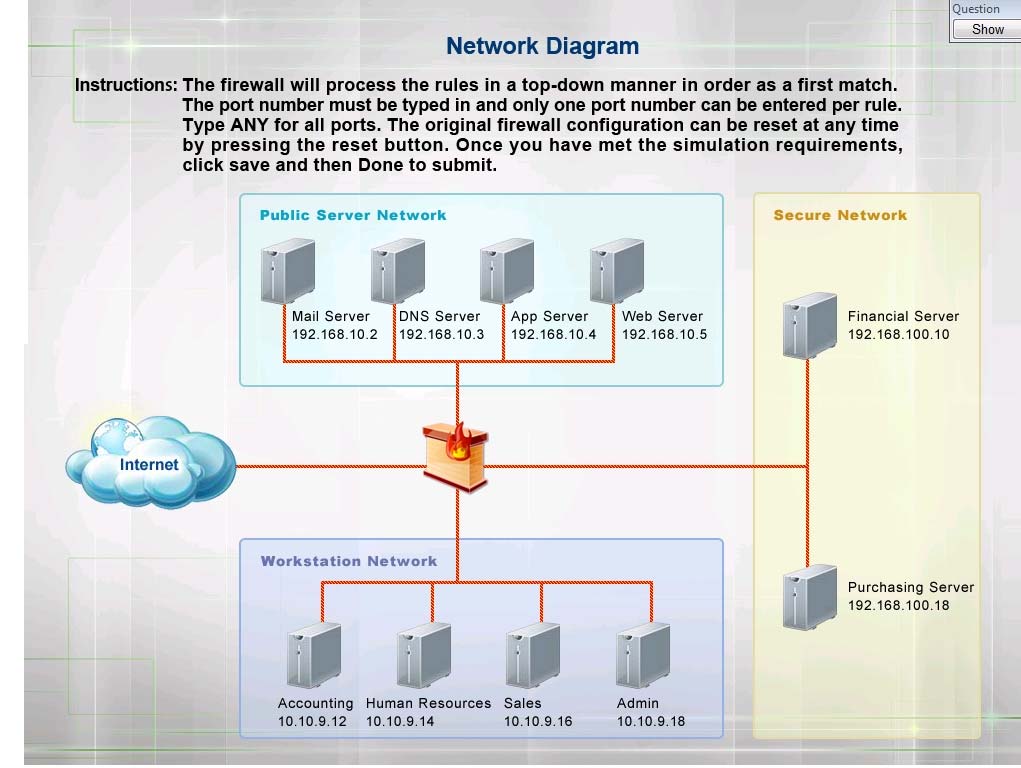
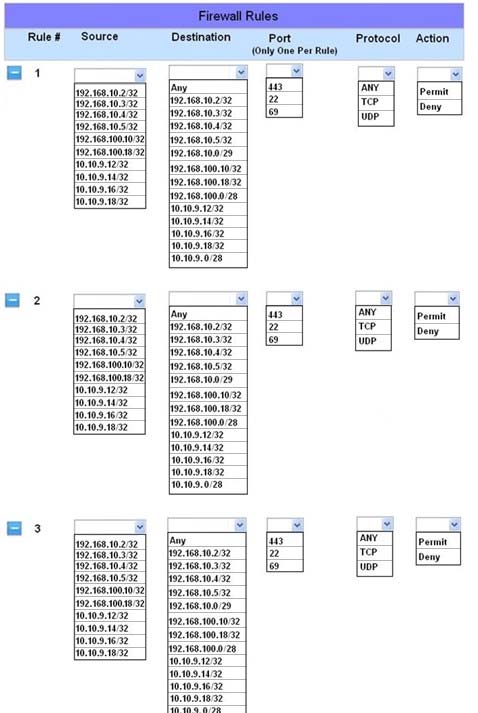
The security administrator has installed a new firewall which implements an implicit DENY policy by default. Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule. Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.
Hot Area:
The security administrator has installed a new firewall which implements an implicit DENY policy by default. Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule. Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.

Hot Area:

Correct Answer:
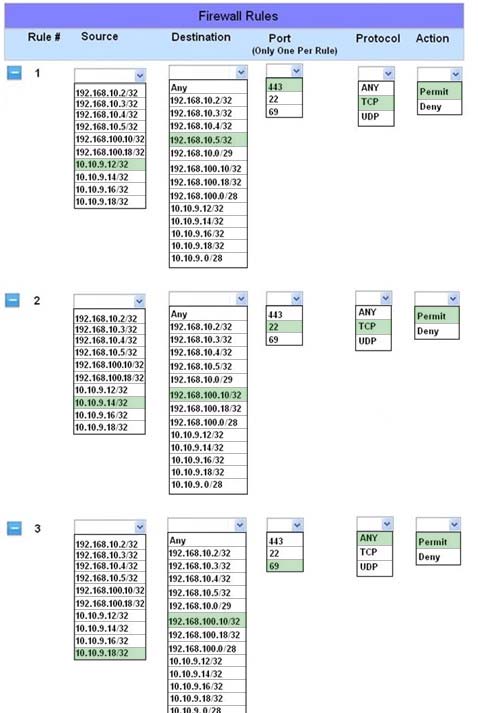
Implicit deny is the default security stance that says if you arent specifically granted access or privileges for a resource, youre denied access by default.
Rule #1 allows the Accounting workstation to ONLY access the web server on the public network over the default HTTPS port, which is TCP port 443.
Rule #2 allows the HR workstation to ONLY communicate with the Financial server over the default SCP port, which is TCP Port 22
Rule #3 & Rule #4 allow the Admin workstation to ONLY access the Financial and Purchasing servers located on the secure network over the default TFTP port, which is Port 69.
References:
, Sybex, Indianapolis, 2014, pp. 26, 44
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers

Implicit deny is the default security stance that says if you arent specifically granted access or privileges for a resource, youre denied access by default.
Rule #1 allows the Accounting workstation to ONLY access the web server on the public network over the default HTTPS port, which is TCP port 443.
Rule #2 allows the HR workstation to ONLY communicate with the Financial server over the default SCP port, which is TCP Port 22
Rule #3 & Rule #4 allow the Admin workstation to ONLY access the Financial and Purchasing servers located on the secure network over the default TFTP port, which is Port 69.
References:
, Sybex, Indianapolis, 2014, pp. 26, 44
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
send
light_mode
delete
Question #34
Which of the following firewall rules only denies DNS zone transfers?
- Adeny udp any any port 53
- Bdeny ip any any
- Cdeny tcp any any port 53
- Ddeny all dns packets
Correct Answer:
C
DNS operates over TCP and UDP port 53. TCP port 53 is used for zone transfers.
C
DNS operates over TCP and UDP port 53. TCP port 53 is used for zone transfers.
send
light_mode
delete
Question #35
A security administrator suspects that an increase in the amount of TFTP traffic on the network is due to unauthorized file transfers, and wants to configure a firewall to block all TFTP traffic.
Which of the following would accomplish this task?
Which of the following would accomplish this task?
- ADeny TCP port 68
- BDeny TCP port 69
- CDeny UDP port 68
- DDeny UDP port 69
Correct Answer:
D
Trivial File Transfer Protocol (TFTP) is a simple file-exchange protocol that doesnt require authentication. It operates on UDP port 69.
D
Trivial File Transfer Protocol (TFTP) is a simple file-exchange protocol that doesnt require authentication. It operates on UDP port 69.
send
light_mode
delete
Question #36
Sara, a security technician, has received notice that a vendor coming in for a presentation will require access to a server outside of the network. Currently, users are only able to access remote sites through a VPN connection. How could Sara BEST accommodate the vendor?
- AAllow incoming IPSec traffic into the vendor’s IP address.
- BSet up a VPN account for the vendor, allowing access to the remote site.
- CTurn off the firewall while the vendor is in the office, allowing access to the remote site.
- DWrite a firewall rule to allow the vendor to have access to the remote site.
Correct Answer:
D
Firewall rules are used to define what traffic is able pass between the firewall and the internal network. Firewall rules block the connection, allow the connection, or allow the connection only if it is secured. Firewall rules can be applied to inbound traffic or outbound traffic and any type of network.
D
Firewall rules are used to define what traffic is able pass between the firewall and the internal network. Firewall rules block the connection, allow the connection, or allow the connection only if it is secured. Firewall rules can be applied to inbound traffic or outbound traffic and any type of network.
send
light_mode
delete
Question #37
A technician is deploying virtual machines for multiple customers on a single physical host to reduce power consumption in a data center. Which of the following should be recommended to isolate the VMs from one another?
- AImplement a virtual firewall
- BInstall HIPS on each VM
- CVirtual switches with VLANs
- DDevelop a patch management guide
Correct Answer:
C
A virtual local area network (VLAN) is a hardware-imposed network segmentation created by switches. VLANs are used for traffic management. VLANs can be used to isolate traffic between network segments.
C
A virtual local area network (VLAN) is a hardware-imposed network segmentation created by switches. VLANs are used for traffic management. VLANs can be used to isolate traffic between network segments.
send
light_mode
delete
Question #38
A router has a single Ethernet connection to a switch. In the router configuration, the Ethernet interface has three sub-interfaces, each configured with ACLs applied to them and 802.1q trunks.
Which of the following is MOST likely the reason for the sub-interfaces?
Which of the following is MOST likely the reason for the sub-interfaces?
- AThe network uses the subnet of 255.255.255.128.
- BThe switch has several VLANs configured on it.
- CThe sub-interfaces are configured for VoIP traffic.
- DThe sub-interfaces each implement quality of service.
Correct Answer:
B
A subinterface is a division of one physical interface into multiple logical interfaces. Routers commonly employ subinterfaces for a variety of purposes, most common of these are for routing traffic between VLANs. Also, IEEE 802.1Q is the networking standard that supports virtual LANs (VLANs) on an Ethernet network.
B
A subinterface is a division of one physical interface into multiple logical interfaces. Routers commonly employ subinterfaces for a variety of purposes, most common of these are for routing traffic between VLANs. Also, IEEE 802.1Q is the networking standard that supports virtual LANs (VLANs) on an Ethernet network.
send
light_mode
delete
Question #39
Joe, a technician at the local power plant, notices that several turbines had ramped up in cycles during the week. Further investigation by the system engineering team determined that a timed .exe file had been uploaded to the system control console during a visit by international contractors.
Which of the following actions should Joe recommend?
Which of the following actions should Joe recommend?
- ACreate a VLAN for the SCADA
- BEnable PKI for the MainFrame
- CImplement patch management
- DImplement stronger WPA2 Wireless
Correct Answer:
A
VLANs are used for traffic management. VLANs can be used to isolate traffic between network segments. This can be accomplished by not defining a route between different VLANs or by specifying a deny filter between certain VLANs (or certain members of a VLAN). Any network segment that doesnt need to communicate with another in order to accomplish a work task/function shouldnt be able to do so.
A
VLANs are used for traffic management. VLANs can be used to isolate traffic between network segments. This can be accomplished by not defining a route between different VLANs or by specifying a deny filter between certain VLANs (or certain members of a VLAN). Any network segment that doesnt need to communicate with another in order to accomplish a work task/function shouldnt be able to do so.
send
light_mode
delete
Question #40
The security administrator needs to manage traffic on a layer 3 device to support FTP from a new remote site. Which of the following would need to be implemented?
- AImplicit deny
- BVLAN management
- CPort security
- DAccess control lists
Correct Answer:
D
In the OSI model, IP addressing and IP routing are performed at layer 3 (the network layer). In this question we need to configure routing. When configuring routing, you specify which IP range (in this case, the IP subnet of the remote site) is allowed to route traffic through the router to the FTP server.
Traffic that comes into the router is compared to ACL entries based on the order that the entries occur in the router. New statements are added to the end of the list. The router continues to look until it has a match. If no matches are found when the router reaches the end of the list, the traffic is denied. For this reason, you should have the frequently hit entries at the top of the list. There is an implied deny for traffic that is not permitted.
D
In the OSI model, IP addressing and IP routing are performed at layer 3 (the network layer). In this question we need to configure routing. When configuring routing, you specify which IP range (in this case, the IP subnet of the remote site) is allowed to route traffic through the router to the FTP server.
Traffic that comes into the router is compared to ACL entries based on the order that the entries occur in the router. New statements are added to the end of the list. The router continues to look until it has a match. If no matches are found when the router reaches the end of the list, the traffic is denied. For this reason, you should have the frequently hit entries at the top of the list. There is an implied deny for traffic that is not permitted.
send
light_mode
delete
All Pages
