CompTIA PT1-002 Exam Practice Questions (P. 3)
- Full Access (110 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
send
light_mode
delete
Question #12
SIMULATION -
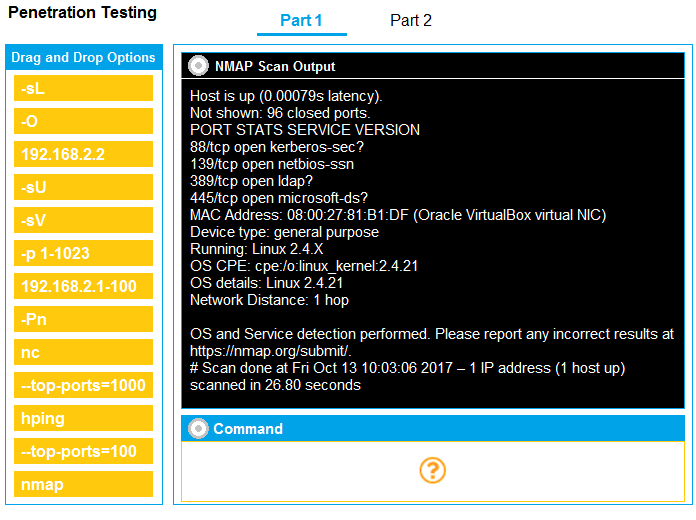
You are a penetration tester running port scans on a server.
INSTRUCTIONS -
Part 1: Given the output, construct the command that was used to generate this output from the available options.
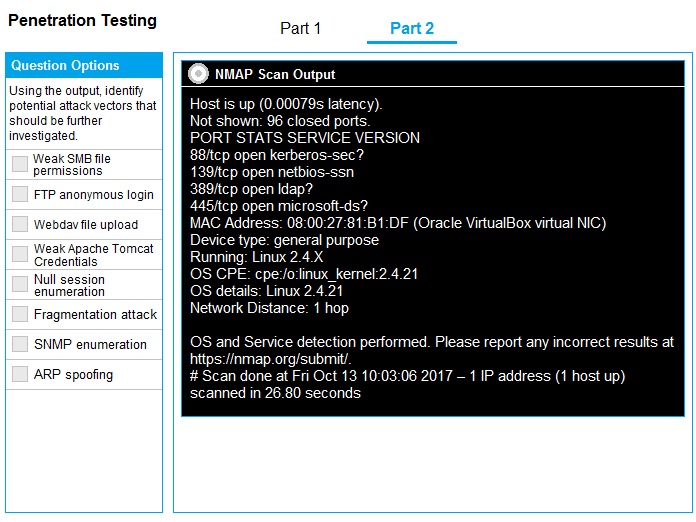
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
You are a penetration tester running port scans on a server.
INSTRUCTIONS -
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Correct Answer:
See explanation below.
Part 1 - nmap 192.168.2.2 -sV -O
Part 2 - Weak SMB file permissions
See explanation below.
Part 1 - nmap 192.168.2.2 -sV -O
Part 2 - Weak SMB file permissions
send
light_mode
delete
Question #13
A penetration tester is exploring a client's website. The tester performs a curl command and obtains the following:
* Connected to 10.2.11.144 (::1) port 80 (#0)
> GET /readmine.html HTTP/1.1
> Host: 10.2.11.144
> User-Agent: curl/7.67.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Date: Tue, 02 Feb 2021 21:46:47 GMT
< Server: Apache/2.4.41 (Debian)
< Content-Length: 317
< Content-Type: text/html; charset=iso-8859-1
<
<!DOCTYPE html>
<html lang=`en`>
<head>
<meta name=`viewport` content=`width=device-width` />
<meta http-equiv=`Content-Type` content=`text/html; charset=utf-8` />
<title>WordPress › ReadMe</title>
<link rel=`stylesheet` href=`wp-admin/css/install.css?ver=20100228` type=`text/css` />
</head>
Which of the following tools would be BEST for the penetration tester to use to explore this site further?
* Connected to 10.2.11.144 (::1) port 80 (#0)
> GET /readmine.html HTTP/1.1
> Host: 10.2.11.144
> User-Agent: curl/7.67.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Date: Tue, 02 Feb 2021 21:46:47 GMT
< Server: Apache/2.4.41 (Debian)
< Content-Length: 317
< Content-Type: text/html; charset=iso-8859-1
<
<!DOCTYPE html>
<html lang=`en`>
<head>
<meta name=`viewport` content=`width=device-width` />
<meta http-equiv=`Content-Type` content=`text/html; charset=utf-8` />
<title>WordPress › ReadMe</title>
<link rel=`stylesheet` href=`wp-admin/css/install.css?ver=20100228` type=`text/css` />
</head>
Which of the following tools would be BEST for the penetration tester to use to explore this site further?
- ABurp Suite
- BDirBuster
- CWPScanMost Voted
- DOWASP ZAP
Correct Answer:
A
Reference:
https://tools.kali.org/web-applications/burpsuite
A
Reference:
https://tools.kali.org/web-applications/burpsuite
send
light_mode
delete
Question #14
A penetration tester wrote the following script to be used in one engagement:
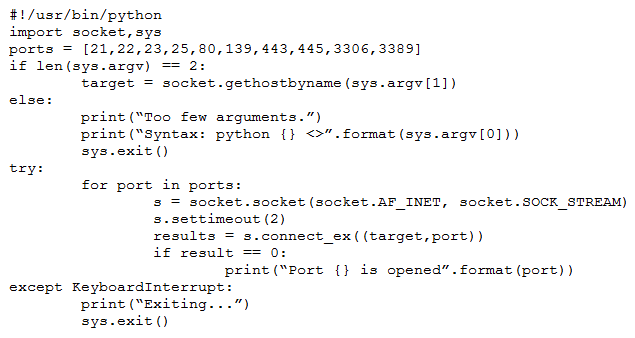
Which of the following actions will this script perform?

Which of the following actions will this script perform?
- ALook for open ports.
- BListen for a reverse shell.
- CAttempt to flood open ports.
- DCreate an encrypted tunnel.
Correct Answer:
A
A
send
light_mode
delete
Question #15
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site. Which of the following recommendations would BEST address this situation?
- AImplement a recurring cybersecurity awareness education program for all users.Most Voted
- BImplement multifactor authentication on all corporate applications.
- CRestrict employees from web navigation by defining a list of unapproved sites in the corporate proxy.
- DImplement an email security gateway to block spam and malware from email communications.
Correct Answer:
A
Reference:
https://resources.infosecinstitute.com/topic/top-9-free-phishing-simulators/
A
Reference:
https://resources.infosecinstitute.com/topic/top-9-free-phishing-simulators/
send
light_mode
delete
All Pages
