CompTIA PT0-002 Exam Practice Questions (P. 5)
- Full Access (531 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
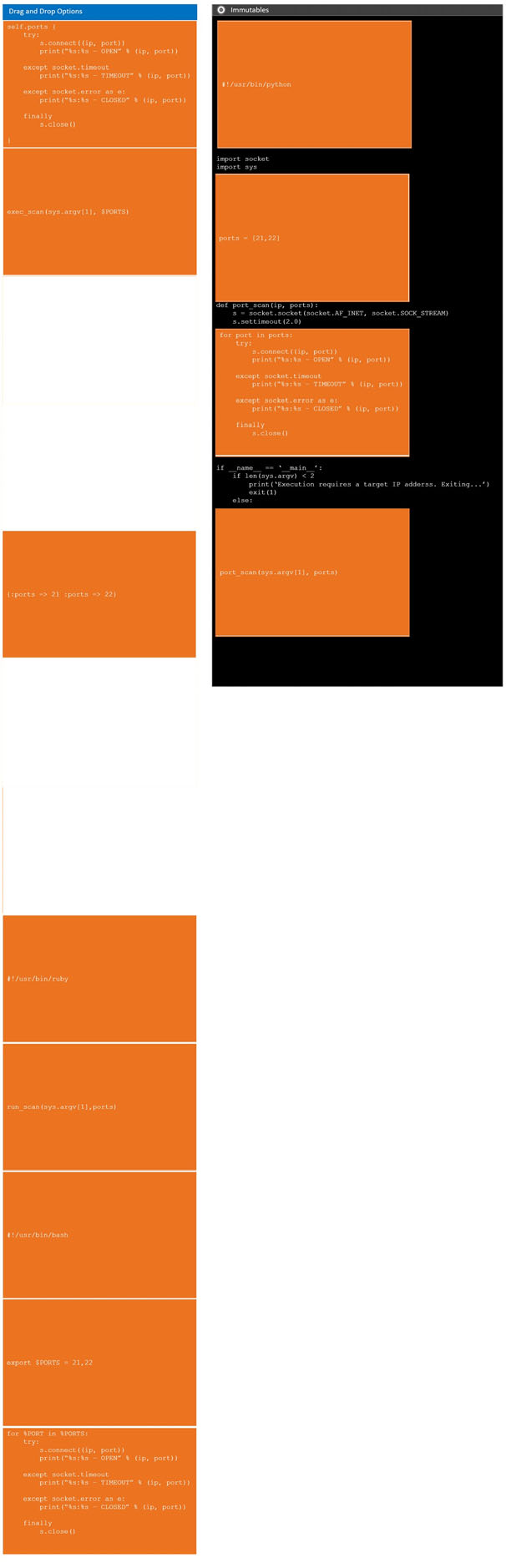
A penetration tester has been given an assignment to attack a series of targets in the 192.168.1.0/24 range, triggering as few alarms and countermeasures as possible.
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
- Anmap -sT -vvv -O 192.168.1.2/24 -PO
- Bnmap -sV 192.168.1.2/24 -PO
- Cnmap -sA -v -O 192.168.1.2/24
- Dnmap -sS -O 192.168.1.2/24 -T1Most Voted
Correct Answer:
D
Reference:
https://nmap.org/book/man-port-scanning-techniques.html
D
Reference:
https://nmap.org/book/man-port-scanning-techniques.html

send
light_mode
delete
Question #42
A penetration tester has gained access to a network device that has a previously unknown IP range on an interface. Further research determines this is an always-on VPN tunnel to a third-party supplier.
Which of the following is the BEST action for the penetration tester to take?
Which of the following is the BEST action for the penetration tester to take?
- AUtilize the tunnel as a means of pivoting to other internal devices.
- BDisregard the IP range, as it is out of scope.
- CStop the assessment and inform the emergency contact.Most Voted
- DScan the IP range for additional systems to exploit.
Correct Answer:
D
D
send
light_mode
delete
Question #43
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee's birthday, the tester gave the employee an external hard drive as a gift.
Which of the following social-engineering attacks was the tester utilizing?
Which of the following social-engineering attacks was the tester utilizing?
- APhishing
- BTailgating
- CBaitingMost Voted
- DShoulder surfing
Correct Answer:
C
Reference:
https://phoenixnap.com/blog/what-is-social-engineering-types-of-threats
C
Reference:
https://phoenixnap.com/blog/what-is-social-engineering-types-of-threats

send
light_mode
delete
Question #44
A security company has been contracted to perform a scoped insider-threat assessment to try to gain access to the human resources server that houses PII and salary data. The penetration testers have been given an internal network starting position.
Which of the following actions, if performed, would be ethical within the scope of the assessment?
Which of the following actions, if performed, would be ethical within the scope of the assessment?
- AExploiting a configuration weakness in the SQL databaseMost Voted
- BIntercepting outbound TLS traffic
- CGaining access to hosts by injecting malware into the enterprise-wide update server
- DLeveraging a vulnerability on the internal CA to issue fraudulent client certificates
- EEstablishing and maintaining persistence on the domain controller
Correct Answer:
B
B
send
light_mode
delete
Question #45
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server.
Which of the following can be done with the pcap to gain access to the server?
Which of the following can be done with the pcap to gain access to the server?
- APerform vertical privilege escalation.
- BReplay the captured traffic to the server to recreate the session.
- CUse John the Ripper to crack the password.
- DUtilize a pass-the-hash attack.Most Voted
Correct Answer:
D
D
send
light_mode
delete
Question #46
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?
send
light_mode
delete
Question #47
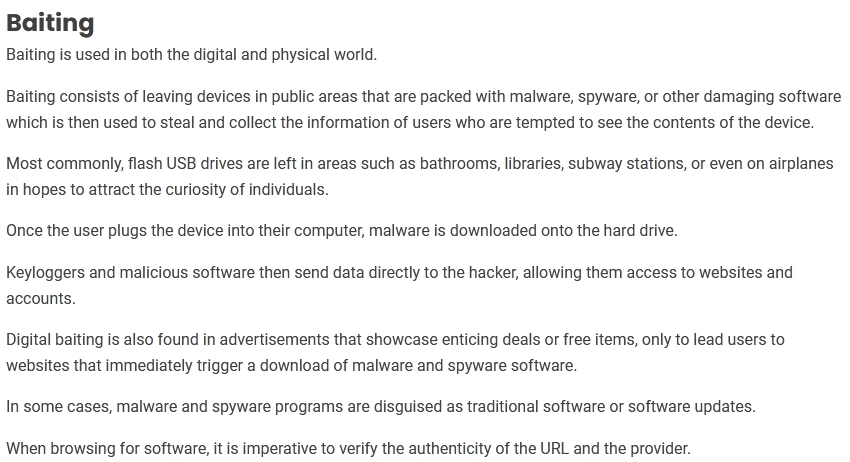
A penetration tester is exploring a client's website. The tester performs a curl command and obtains the following:
Which of the following tools would be BEST for the penetration tester to use to explore this site further?

Which of the following tools would be BEST for the penetration tester to use to explore this site further?
send
light_mode
delete
Question #48
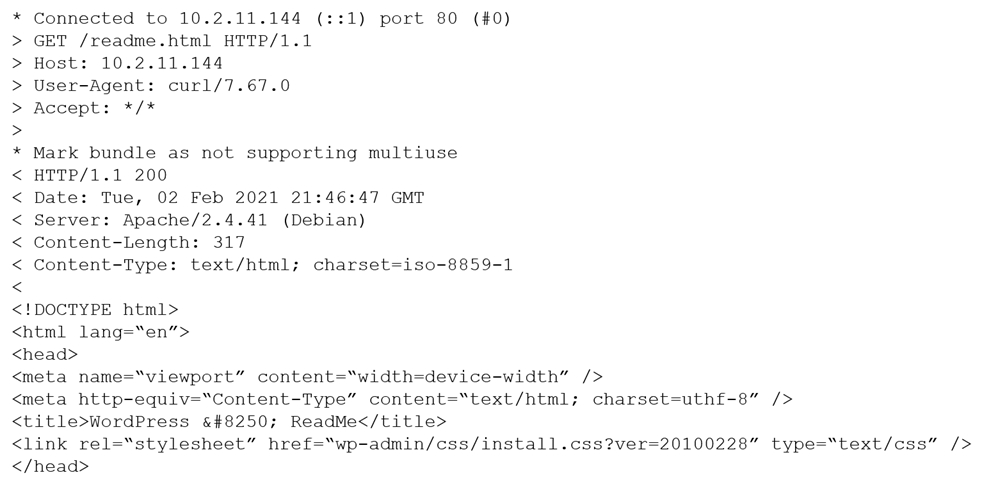
DRAG DROP -
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS -
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:

During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS -
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:

send
light_mode
delete
Question #49
In an unprotected network file repository, a penetration tester discovers a text file containing usernames and passwords in cleartext and a spreadsheet containing data for 50 employees, including full names, roles, and serial numbers. The tester realizes some of the passwords in the text file follow the format: <name- serial_number>.
Which of the following would be the best action for the tester to take NEXT with this information?
Which of the following would be the best action for the tester to take NEXT with this information?
- ACreate a custom password dictionary as preparation for password spray testing.
- BRecommend using a password manager/vault instead of text files to store passwords securely.
- CRecommend configuring password complexity rules in all the systems and applications.
- DDocument the unprotected file repository as a finding in the penetration-testing report.Most Voted
Correct Answer:
D
D
send
light_mode
delete
Question #50
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified.
Which of the following character combinations should be used on the first line of the script to accomplish this goal?
Which of the following character combinations should be used on the first line of the script to accomplish this goal?
- A<#
- B<$
- C##
- D#$
- E#!Most Voted
Correct Answer:
E
Reference:
https://linuxconfig.org/bash-scripting-tutorial-for-beginners
E
Reference:
https://linuxconfig.org/bash-scripting-tutorial-for-beginners

send
light_mode
delete
All Pages