CompTIA PT0-001 Exam Practice Questions (P. 1)
- Full Access (196 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
DRAG DROP -
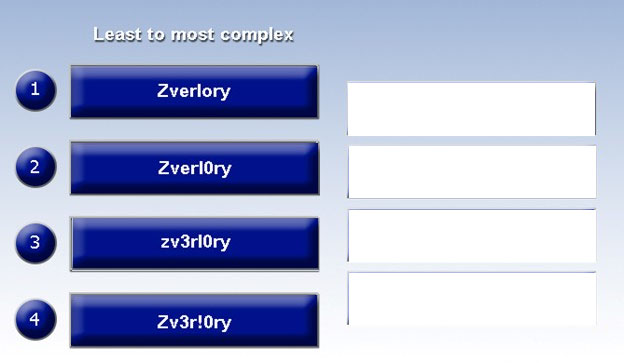
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented. Each password may be used only once.
Select and Place:
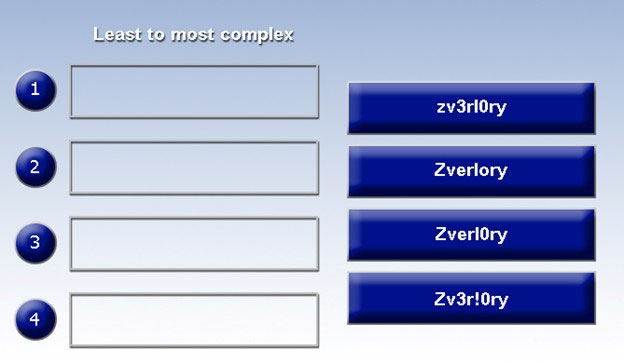
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented. Each password may be used only once.
Select and Place:

send
light_mode
delete
Question #2
DRAG DROP -
A manager calls upon a tester to assist with diagnosing an issue within the following Python script:
#!/usr/bin/python
s = `Administrator`
The tester suspects it is an issue with string slicing and manipulation. Analyze the following code segment and drag and drop the correct output for each string manipulation to its corresponding code segment. Options may be used once or not at all.
Select and Place:

A manager calls upon a tester to assist with diagnosing an issue within the following Python script:
#!/usr/bin/python
s = `Administrator`
The tester suspects it is an issue with string slicing and manipulation. Analyze the following code segment and drag and drop the correct output for each string manipulation to its corresponding code segment. Options may be used once or not at all.
Select and Place:

send
light_mode
delete
Question #3
A penetration tester has compromised a Windows server and is attempting to achieve persistence. Which of the following would achieve that goal?
- Aschtasks.exe /create/tr ג€powershell.exeג€ Sv.ps1 /runMost Voted
- Bnet session server | dsquery -user | net use c$
- Cpowershell && set-executionpolicy unrestricted
- Dreg save HKLM\System\CurrentControlSet\Services\Sv.reg
Correct Answer:
D
D
send
light_mode
delete
Question #4
A client has scheduled a wireless penetration test. Which of the following describes the scoping target information MOST likely needed before testing can begin?
- AThe physical location and network ESSIDs to be testedMost Voted
- BThe number of wireless devices owned by the client
- CThe client's preferred wireless access point vendor
- DThe bands and frequencies used by the client's devices
Correct Answer:
D
D
send
light_mode
delete
Question #5
Which of the following BEST describes some significant security weaknesses with an ICS, such as those used in electrical utility facilities, natural gas facilities, dams, and nuclear facilities?
- AICS vendors are slow to implement adequate security controls.Most Voted
- BICS staff are not adequately trained to perform basic duties.
- CThere is a scarcity of replacement equipment for critical devices.
- DThere is a lack of compliance for ICS facilities.
Correct Answer:
B
B
send
light_mode
delete
All Pages