CompTIA N10-008 Exam Practice Questions (P. 5)
- Full Access (877 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
Which of the following service models would MOST likely be used to replace on-premises servers with a cloud solution?
send
light_mode
delete
Question #42
Which of the following factors should be considered when evaluating a firewall to protect a datacenter's east-west traffic?
- AReplication traffic between an on-premises server and a remote backup facilityMost Voted
- BTraffic between VMs running on different hosts
- CConcurrent connections generated by Internet DDoS attacks
- DVPN traffic from remote offices to the datacenter's VMs
Correct Answer:
A
A
send
light_mode
delete
Question #43
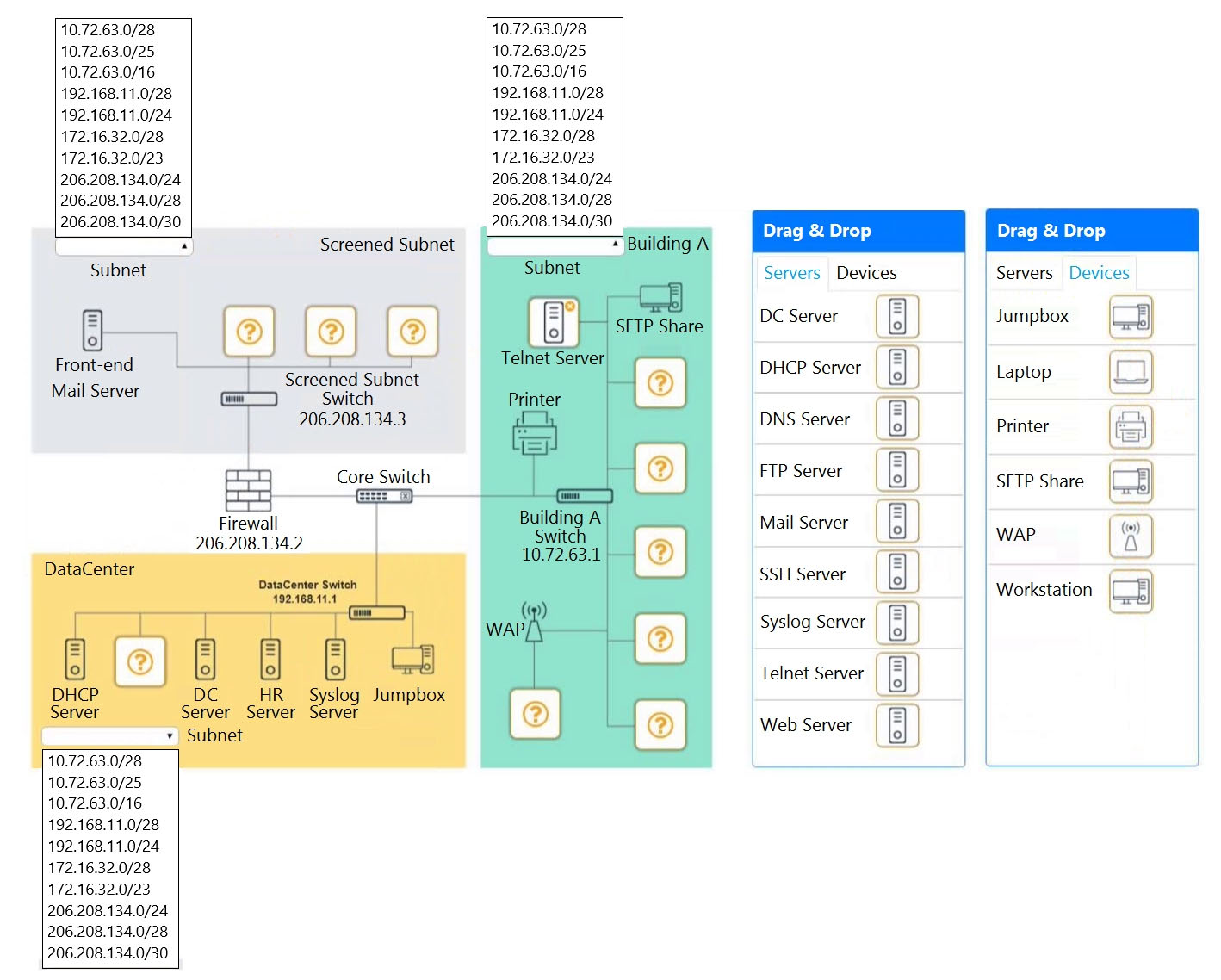
SIMULATION -
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
✑ Datacenter
- Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
- Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic
✑ Building A
- Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
- Provide devices to support 5 additional different office users
- Add an additional mobile user
- Replace the Telnet server with a more secure solution
✑ Screened subnet
- Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
- Provide a server to handle external 80/443 traffic
- Provide a server to handle port 20/21 traffic
INSTRUCTIONS -
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag & Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
✑ Datacenter
- Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
- Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic
✑ Building A
- Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
- Provide devices to support 5 additional different office users
- Add an additional mobile user
- Replace the Telnet server with a more secure solution
✑ Screened subnet
- Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
- Provide a server to handle external 80/443 traffic
- Provide a server to handle port 20/21 traffic
INSTRUCTIONS -
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag & Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Correct Answer:
See explanation below.
Top left subnet ג€" 206.208.134.0/28
Top right subnet ג€" 10.72.63.0/28
Bottom subnet ג€" 192.168.11.0/28
Screened Subnet devices ג€" Web server, FTP server
Building A devices ג€" SSH server top left, workstations on all 5 on the right, laptop on bottom left
DataCenter devices ג€" DNS server.
See explanation below.
Top left subnet ג€" 206.208.134.0/28
Top right subnet ג€" 10.72.63.0/28
Bottom subnet ג€" 192.168.11.0/28
Screened Subnet devices ג€" Web server, FTP server
Building A devices ג€" SSH server top left, workstations on all 5 on the right, laptop on bottom left
DataCenter devices ג€" DNS server.
send
light_mode
delete
Question #44
Which of the following is used to prioritize Internet usage per application and per user on the network?
- ABandwidth managementMost Voted
- BLoad balance routing
- CBorder Gateway Protocol
- DAdministrative distance
Correct Answer:
A
A
send
light_mode
delete
Question #45
A network administrator needs to query the NSs for a remote application. Which of the following commands would BEST help the administrator accomplish this task?
send
light_mode
delete
Question #46
Which of the following would MOST likely be used to review previous upgrades to a system?
- ABusiness continuity plan
- BChange managementMost Voted
- CSystem life cycle
- DStandard operating procedures
Correct Answer:
B
B
send
light_mode
delete
Question #47
A technician is deploying a new switch model and would like to add it to the existing network monitoring software. The technician wants to know what metrics can be gathered from a given switch. Which of the following should the technician utilize for the switch?
send
light_mode
delete
Question #48
A network device is configured to send critical events to a syslog server; however, the following alerts are not being received:
Severity 5 LINK-UPDOWN: Interface 1/1, changed state to down
Severity 5 LINK-UPDOWN: Interface 1/3, changed state to down
Which of the following describes the reason why the events are not being received?
Severity 5 LINK-UPDOWN: Interface 1/1, changed state to down
Severity 5 LINK-UPDOWN: Interface 1/3, changed state to down
Which of the following describes the reason why the events are not being received?
- AThe network device is not configured to log that level to the syslog serverMost Voted
- BThe network device was down and could not send the event
- CThe syslog server is not compatible with the network device
- DThe syslog server did not have the correct MIB loaded to receive the message
Correct Answer:
A
A
send
light_mode
delete
Question #49
A network administrator is implementing OSPF on all of a company's network devices. Which of the following will MOST likely replace all the company's hubs?
- AA Layer 3 switchMost Voted
- BA proxy server
- CA NGFW
- DA WLAN controller
Correct Answer:
A
A
send
light_mode
delete
Question #50
A network administrator discovers that users in an adjacent building are connecting to the company's guest wireless network to download inappropriate material.
Which of the following can the administrator do to MOST easily mitigate this issue?
Which of the following can the administrator do to MOST easily mitigate this issue?
- AReduce the wireless power levelsMost Voted
- BAdjust the wireless channels
- CEnable wireless client isolation
- DEnable wireless port security
Correct Answer:
A
A
send
light_mode
delete
All Pages
