CompTIA CV0-003 Exam Practice Questions (P. 2)
- Full Access (386 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
A company developed a product using a cloud provider's PaaS platform and many of the platform-based components within the application environment. Which of the following would the company MOST likely be concerned about when utilizing a multicloud strategy or migrating to another cloud provider?
- ALicensing
- BAuthentication providers
- CService-level agreement
- DVendor lock-inMost Voted
Correct Answer:
D
D
 GPT-4o - Answer
GPT-4o - Answer
Vendor lock-in is a significant concern for companies using a specific cloud provider's PaaS platform, especially when developed features are tightly integrated with the provider's unique tools and services. This dependency can create challenges in migrating to a different cloud provider or adopting a multicloud strategy, as it may limit flexibility and increase transition costs due to the need to adapt or redesign the application to fit another environment. Keep in mind, vendor lock-in doesn't just affect operational flexibility but also strategic IT decisions.
send
light_mode
delete
Question #12
A systems administrator is trying to establish an RDP session from a desktop to a server in the cloud. However, the connection appears to be refused even through the VM is responding to ICMP echo requests. Which of the following should the administrator check FIRST?
- AThe firewallMost Voted
- BThe subnet
- CThe gateway
- DThe services
Correct Answer:
D
D
 GPT-4o - Answer
GPT-4o - Answer
While it's valuable to make sure the server's RDP service is up and running, a refused RDP connection usually hints at firewall settings first. Since ICMP responses confirm the server is reachable, the refusal of the RDP session often results from the firewall blocking it. Always check if the firewall allows traffic on TCP port 3389, the default port for RDP, as this is a frequent oversight in network troubleshooting.
send
light_mode
delete
Question #13
Which of the following would be the BEST option for discussion of what individuals should do in an incident response or disaster recovery scenario?
- AA business continuity plan
- BIncident response/disaster recovery documentation
- CA tabletop exerciseMost Voted
- DA root cause analysis
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
A tabletop exercise is undoubtedly the best choice when it comes to discussing individual roles and actions in incident response or disaster recovery situations. Through these exercises, team members can interactively simulate various disaster scenarios. This interactive environment helps them pinpoint potential issues, understand their specific roles, and refine response strategies in a realistic yet controlled setting. More importantly, it ensures all participants are aligned and clear on what actions to take during actual incidents, making it more practical than simply referring to documentation or plans.
send
light_mode
delete
Question #14
A systems administrator has migrated an internal application to a public cloud. The new web server is running under a TLS connection and has the same TLS certificate as the internal application that is deployed. However, the IT department reports that only internal users who are using new versions of the OSs are able to load the application home page. Which of the following is the MOST likely cause of the issue?
- AThe local firewall from older OSs is not allowing outbound connections.
- BThe local firewall from older OSs is not allowing inbound connections.
- CThe cloud web server is using a self-signed certificate that is not supported by older browsers.
- DThe cloud web server is using strong ciphers that are not supported by older browsers.Most Voted
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
The issue described likely stems from the use of a self-signed certificate for the TLS connection of the cloud web server. Generally, when applications are migrated to a public cloud and retain the same security configurations used internally, issues can arise if those configurations, such as self-signed certificates, are not universally trusted. Older operating systems may have stricter or outdated trust stores that do not recognize self-signed certificates, preventing these systems from establishing a secure connection to the server. Transitioning to a certificate issued by a recognized public certificate authority would be a recommended step to ensure broader compatibility and trust.
send
light_mode
delete
Question #15
A systems administrator is configuring RAID for a new server. This server will host files for users and replicate to an identical server. While redundancy is necessary, the most important need is to maximize storage. Which of the following RAID types should the administrator choose?
- A5Most Voted
- B6
- C10
- D50
Correct Answer:
A
A
 GPT-4o - Answer
GPT-4o - Answer
RAID 5 is indeed the optimal choice when the priority is to maximize storage capacity while maintaining necessary redundancy. Its storage efficiency is due to the use of a single disk's worth of space for parity, allowing (N-1)X storage capacity where N represents total disks, and X is the individual disk capacity. This configuration strikes a good balance by using less space for parity compared to RAID 6 or RAID 50, and more storage capacity compared to RAID 10, which dedicates half the total disk space to redundancy. Thus, for situations where redundancy is also handled by replication elsewhere, RAID 5 maximizes usable storage space.
send
light_mode
delete
Question #16
A cloud architect is designing the VPCs for a new hybrid cloud deployment. The business requires the following:
✑ High availability
✑ Horizontal auto-scaling
✑ 60 nodes peak capacity per region
✑ Five reserved network IP addresses per subnet
✑ /24 range
Which of the following would BEST meet the above requirements?
✑ High availability
✑ Horizontal auto-scaling
✑ 60 nodes peak capacity per region
✑ Five reserved network IP addresses per subnet
✑ /24 range
Which of the following would BEST meet the above requirements?
- ACreate two /25 subnets in different regions.Most Voted
- BCreate three /25 subnets in different regions.
- CCreate two /26 subnets in different regions.
- DCreate three /26 subnets in different regions.
- ECreate two /27 subnets in different regions.
- FCreate three /27 subnets in different regions.
Correct Answer:
A
A
 GPT-4o - Answer
GPT-4o - Answer
The correct choice, option A, ensures high availability and horizontal scaling across regions and effectively utilizes the IP address space. Each /25 subnet provides 128 addresses; however, for usability in strict networking terms, only 126 are typically used because of network and broadcast addresses. Deducting five reserved IPs per subnet, we still comfortably exceed the necessary 60 nodes per region, thus meeting all given requirements efficiently without any IP wastage. Furthermore, the segmentation into two /25 subnets aligns perfectly within the confines of the /24 network range, logically subdividing the space without any overlaps or waste.
send
light_mode
delete
Question #17
A company recently experienced a power outage that lasted 30 minutes. During this time, a whole rack of servers was inaccessible, even though the servers did not lose power. Which of the following should be investigated FIRST?
- AServer power
- BRack power
- CSwitch powerMost Voted
- DSAN power
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
Investigating switch power first makes the most sense here. Since the servers were up and running without power issues but were still inaccessible, this points us toward a connectivity problem, likely at the switch level. It's vital to ensure that the switches maintaining network connections for these servers are consistently powered and functioning correctly to avoid such downtime. This approach immediately addresses the potential point of failure highlighted by the scenario.
send
light_mode
delete
Question #18
A cloud provider wants to make sure consumers are utilizing its IaaS platform but prevent them from installing a hypervisor on the server. Which of the following will help the cloud provider secure the environment and limit consumers' activity?
- APatch management
- BHardeningMost Voted
- CScaling
- DLog and event monitoring
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Hardening is indeed the best option when a cloud provider wants to secure their IaaS environment by restricting capabilities such as installing a hypervisor. Hardening encompasses strategies aimed at tightening security measures, ensuring that deployments follow the principle of least privilege. This focused approach ensures users have only the access they require, effectively preventing unauthorized configurations and installations, such as adding a non-sanctioned hypervisor.
send
light_mode
delete
Question #19
A resource pool in a cloud tenant has 90 GB of memory and 120 cores. The cloud administrator needs to maintain a 30% buffer for resources for optimal performance of the hypervisor. Which of the following would allow for the maximum number of two-core machines with equal memory?
- A30 VMs, 3GB of memory
- B40 VMs, 1,5GB of memoryMost Voted
- C45 VMs, 2 GB of memory
- D60 VMs, 1 GB of memory
Correct Answer:
D
D
 GPT-4o - Answer
GPT-4o - Answer
When configuring a cloud tenant, retaining a 30% resource buffer for hypervisor performance is crucial, translating to 63GB of memory and 84 cores being available. While answer D appears to utilize all resources without accounting for this necessary buffer, answer B, which proposes 40 VMs, each with 1.5GB of memory (totaling 60GB) and consuming 80 cores, efficiently uses the resources and maintains the buffer. Thus, for maximum efficiency while adhering to the buffer constraint, option B would also be highly suitable. Ensure your calculations consider both memory and cores to optimize cloud resource allocation effectively.
send
light_mode
delete
Question #20
A company that utilizes an IaaS service provider has contracted with a vendor to perform a penetration test on its environment. The vendor is able to exploit the virtualization layer and obtain access to other instances within the cloud provider's environment that do not belong to the company. Which of the following BEST describes this attack?
- AVM escapeMost Voted
- BDirectory traversal
- CBuffer overflow
- DHeap spraying
Correct Answer:
A
Reference:
https://whatis.techtarget.com/definition/virtual-machine-escape
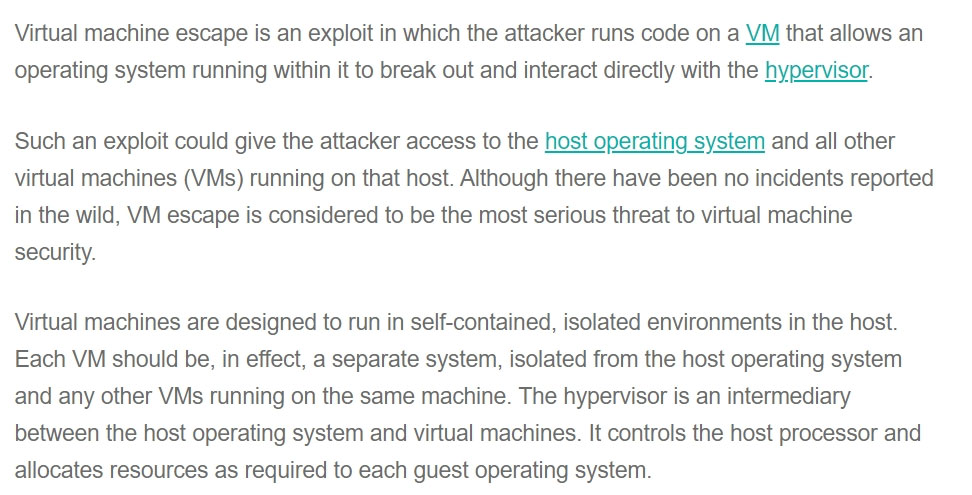
A
Reference:
https://whatis.techtarget.com/definition/virtual-machine-escape

send
light_mode
delete
All Pages
