CompTIA CAS-004 Exam Practice Questions (P. 2)
- Full Access (645 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #11
Which of the following allows computation and analysis of data within a ciphertext without knowledge of the plaintext?
- ALattice-based cryptography
- BQuantum computing
- CAsymmetric cryptography
- DHomomorphic encryptionMost Voted
Correct Answer:
D
Reference:
https://searchsecurity.techtarget.com/definition/cryptanalysis
D
Reference:
https://searchsecurity.techtarget.com/definition/cryptanalysis
send
light_mode
delete
Question #12
A company is looking to fortify its cybersecurity defenses and is focusing on its network infrastructure. The solution cannot affect the availability of the company's services to ensure false positives do not drop legitimate traffic.
Which of the following would satisfy the requirement?
Which of the following would satisfy the requirement?
- ANIDSMost Voted
- BNIPS
- CWAF
- DReverse proxy
Correct Answer:
B
Reference:
https://subscription.packtpub.com/book/networking-and-servers/9781782174905/5/ch05lvl1sec38/differentiating-between-nids-and-nips
B
Reference:
https://subscription.packtpub.com/book/networking-and-servers/9781782174905/5/ch05lvl1sec38/differentiating-between-nids-and-nips
send
light_mode
delete
Question #13
A disaster recovery team learned of several mistakes that were made during the last disaster recovery parallel test. Computational resources ran out at 70% of restoration of critical services.
Which of the following should be modified to prevent the issue from reoccurring?
Which of the following should be modified to prevent the issue from reoccurring?
- ARecovery point objective
- BRecovery time objective
- CMission-essential functions
- DRecovery service levelMost Voted
Correct Answer:
D
Reference:
https://www.nakivo.com/blog/disaster-recovery-in-cloud-computing/

D
Reference:
https://www.nakivo.com/blog/disaster-recovery-in-cloud-computing/

send
light_mode
delete
Question #14
A technician is reviewing the logs and notices a large number of files were transferred to remote sites over the course of three months. This activity then stopped.
The files were transferred via TLS-protected HTTP sessions from systems that do not send traffic to those sites.
The technician will define this threat as:
The files were transferred via TLS-protected HTTP sessions from systems that do not send traffic to those sites.
The technician will define this threat as:
- Aa decrypting RSA using obsolete and weakened encryption attack.
- Ba zero-day attack.
- Can advanced persistent threat.Most Voted
- Dan on-path attack.
Correct Answer:
A
Reference:
https://www.internetsociety.org/deploy360/tls/basics/
A
Reference:
https://www.internetsociety.org/deploy360/tls/basics/
send
light_mode
delete
Question #15
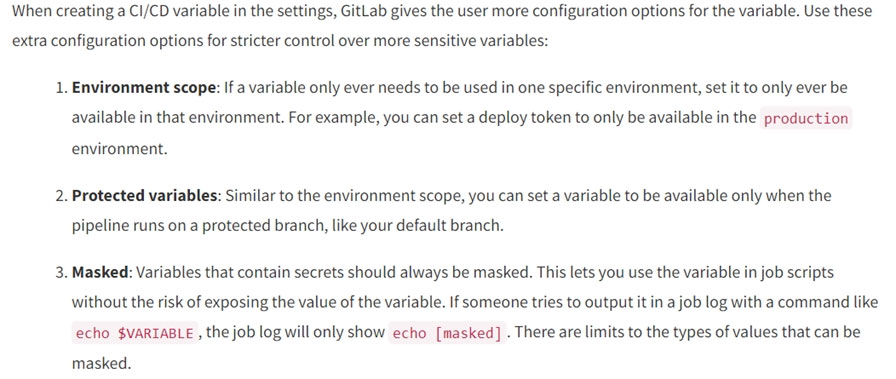
A security engineer thinks the development team has been hard-coding sensitive environment variables in its code.
Which of the following would BEST secure the company's CI/CD pipeline?
Which of the following would BEST secure the company's CI/CD pipeline?
- AUtilizing a trusted secrets managerMost Voted
- BPerforming DAST on a weekly basis
- CIntroducing the use of container orchestration
- DDeploying instance tagging
Correct Answer:
A
Reference:
https://about.gitlab.com/blog/2021/04/09/demystifying-ci-cd-variables/
A
Reference:
https://about.gitlab.com/blog/2021/04/09/demystifying-ci-cd-variables/

send
light_mode
delete
Question #16
A small company recently developed prototype technology for a military program. The company's security engineer is concerned about potential theft of the newly developed, proprietary information.
Which of the following should the security engineer do to BEST manage the threats proactively?
Which of the following should the security engineer do to BEST manage the threats proactively?
- AJoin an information-sharing community that is relevant to the company.
- BLeverage the MITRE ATT&CK framework to map the TTP.
- CUse OSINT techniques to evaluate and analyze the threats.
- DUpdate security awareness training to address new threats, such as best practices for data security.Most Voted
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Leveraging the MITRE ATT&CK framework to map Tactics, Techniques, and Procedures (TTP) is the most effective measure for managing threats proactively in this scenario, especially given the proprietary nature of the information involved. The framework provides a structured approach to understanding and preparing against potential attack vectors specific to the technology and industry, which is indispensable when direct threats have not yet been distinctly identified. This approach aids in creating more targeted security strategies before any actual incident occurs, ensuring a higher level of preparedness.
send
light_mode
delete
Question #17
A security engineer has been asked to close all non-secure connections from the corporate network. The engineer is attempting to understand why the corporate
UTM will not allow users to download email via IMAPS. The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead. The network comprises three VLANs:

The security engineer looks at the UTM firewall rules and finds the following:
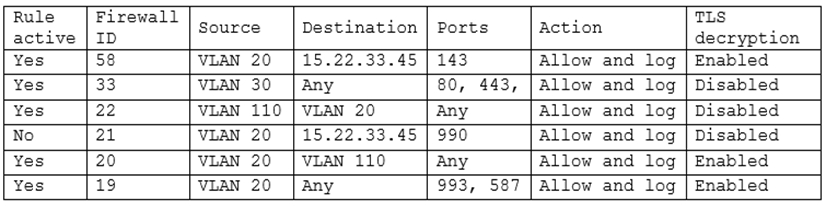
Which of the following should the security engineer do to ensure IMAPS functions properly on the corporate user network?
UTM will not allow users to download email via IMAPS. The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead. The network comprises three VLANs:

The security engineer looks at the UTM firewall rules and finds the following:

Which of the following should the security engineer do to ensure IMAPS functions properly on the corporate user network?
- AContact the email service provider and ask if the company IP is blocked.
- BConfirm the email server certificate is installed on the corporate computers.Most Voted
- CMake sure the UTM certificate is imported on the corporate computers.
- DCreate an IMAPS firewall rule to ensure email is allowed.
Correct Answer:
B
B
send
light_mode
delete
Question #18
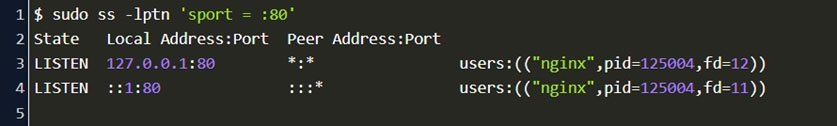
A security analyst is reviewing network connectivity on a Linux workstation and examining the active TCP connections using the command line.
Which of the following commands would be the BEST to run to view only active Internet connections?
Which of the following commands would be the BEST to run to view only active Internet connections?
- Asudo netstat -antu | grep ג€LISTENג€ | awk '{print$5}'
- Bsudo netstat -nlt -p | grep ג€ESTABLISHEDג€
- Csudo netstat -plntu | grep -v ג€Foreign Addressג€
- Dsudo netstat -pnut -w | column -t -s $'\w'
- Esudo netstat -pnut | grep -P ^tcpMost Voted
Correct Answer:
B
Reference:
https://www.codegrepper.com/code-examples/shell/netstat+find+port
B
Reference:
https://www.codegrepper.com/code-examples/shell/netstat+find+port

send
light_mode
delete
Question #19
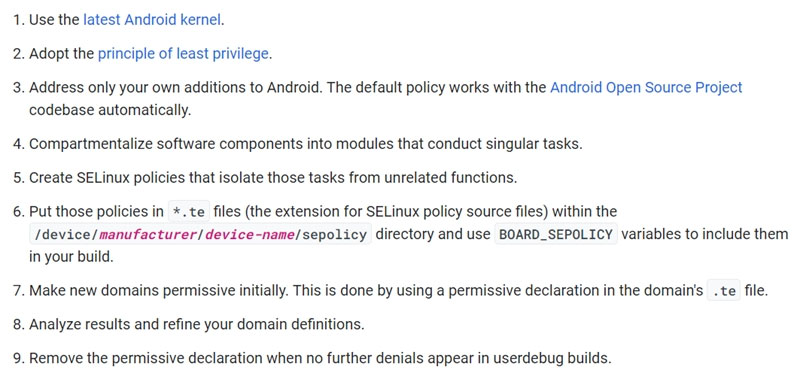
A shipping company that is trying to eliminate entire classes of threats is developing an SELinux policy to ensure its custom Android devices are used exclusively for package tracking.
After compiling and implementing the policy, in which of the following modes must the company ensure the devices are configured to run?
After compiling and implementing the policy, in which of the following modes must the company ensure the devices are configured to run?
- AProtecting
- BPermissive
- CEnforcingMost Voted
- DMandatory
Correct Answer:
B
Reference:
https://source.android.com/security/selinux/customize
B
Reference:
https://source.android.com/security/selinux/customize

send
light_mode
delete
Question #20
A security analyst receives an alert from the SIEM regarding unusual activity on an authorized public SSH jump server. To further investigate, the analyst pulls the event logs directly from /var/log/auth.log: graphic.ssh_auth_log.
Which of the following actions would BEST address the potential risks posed by the activity in the logs?
Which of the following actions would BEST address the potential risks posed by the activity in the logs?
- AAltering the misconfigured service account password
- BModifying the AllowUsers configuration directive
- CRestricting external port 22 accessMost Voted
- DImplementing host-key preferences
Correct Answer:
C
Reference:
https://www.rapid7.com/blog/post/2017/10/04/how-to-secure-ssh-server-using-port-knocking-on-ubuntu-linux/
C
Reference:
https://www.rapid7.com/blog/post/2017/10/04/how-to-secure-ssh-server-using-port-knocking-on-ubuntu-linux/
send
light_mode
delete
All Pages
