CompTIA CAS-004 Exam Practice Questions (P. 1)
- Full Access (645 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
An organization is referencing NIST best practices for BCP creation while reviewing current internal organizational processes for mission-essential items.
Which of the following phases establishes the identification and prioritization of critical systems and functions?
Which of the following phases establishes the identification and prioritization of critical systems and functions?
- AReview a recent gap analysis.
- BPerform a cost-benefit analysis.
- CConduct a business impact analysis.Most Voted
- DDevelop an exposure factor matrix.
Correct Answer:
A
Reference:
https://itsm.ucsf.edu/business-impact-analysis-bia-0

A
Reference:
https://itsm.ucsf.edu/business-impact-analysis-bia-0

send
light_mode
delete
Question #2
An organization is preparing to migrate its production environment systems from an on-premises environment to a cloud service. The lead security architect is concerned that the organization's current methods for addressing risk may not be possible in the cloud environment.
Which of the following BEST describes the reason why traditional methods of addressing risk may not be possible in the cloud?
Which of the following BEST describes the reason why traditional methods of addressing risk may not be possible in the cloud?
- AMigrating operations assumes the acceptance of all risk.
- BCloud providers are unable to avoid risk.
- CSpecific risks cannot be transferred to the cloud provider.Most Voted
- DRisks to data in the cloud cannot be mitigated.
Correct Answer:
C
Reference:
https://arxiv.org/ftp/arxiv/papers/1303/1303.4814.pdf
C
Reference:
https://arxiv.org/ftp/arxiv/papers/1303/1303.4814.pdf
send
light_mode
delete
Question #3
A company created an external application for its customers. A security researcher now reports that the application has a serious LDAP injection vulnerability that could be leveraged to bypass authentication and authorization.
Which of the following actions would BEST resolve the issue? (Choose two.)
Which of the following actions would BEST resolve the issue? (Choose two.)
- AConduct input sanitization.Most Voted
- BDeploy a SIEM.
- CUse containers.
- DPatch the OS
- EDeploy a WAF.Most Voted
- FDeploy a reverse proxy
- GDeploy an IDS.
Correct Answer:
EF
EF
 GPT-4o - Answer
GPT-4o - Answer
Deploying a Web Application Firewall (WAF) and a reverse proxy are effective strategies in addressing LDAP injection vulnerabilities. The WAF operates by monitoring and filtering HTTP traffic to and from a web application, effectively blocking malicious data that can exploit LDAP injections. It follows defined security policies to identify and prevent potentially dangerous requests. Concurrently, a reverse proxy can serve as an additional layer of abstraction and control to ensure that inbound connections do not directly interact with the backend server, providing another tier of defense against injection attacks. Together, these tools play pivotal roles in enhancing security by managing and segregating traffic to protect against such vulnerabilities.
send
light_mode
delete
Question #4
In preparation for the holiday season, a company redesigned the system that manages retail sales and moved it to a cloud service provider. The new infrastructure did not meet the company's availability requirements. During a postmortem analysis, the following issues were highlighted:
1. International users reported latency when images on the web page were initially loading.
2. During times of report processing, users reported issues with inventory when attempting to place orders.
3. Despite the fact that ten new API servers were added, the load across servers was heavy at peak times.
Which of the following infrastructure design changes would be BEST for the organization to implement to avoid these issues in the future?
1. International users reported latency when images on the web page were initially loading.
2. During times of report processing, users reported issues with inventory when attempting to place orders.
3. Despite the fact that ten new API servers were added, the load across servers was heavy at peak times.
Which of the following infrastructure design changes would be BEST for the organization to implement to avoid these issues in the future?
- AServe static content via distributed CDNs, create a read replica of the central database and pull reports from there, and auto-scale API servers based on performance.Most Voted
- BIncrease the bandwidth for the server that delivers images, use a CDN, change the database to a non-relational database, and split the ten API servers across two load balancers.
- CServe images from an object storage bucket with infrequent read times, replicate the database across different regions, and dynamically create API servers based on load.
- DServe static-content object storage across different regions, increase the instance size on the managed relational database, and distribute the ten API servers across multiple regions.
Correct Answer:
A
A
 GPT-4o - Answer
GPT-4o - Answer
For optimal future infrastructure, it is essential to implement a design that addresses all core issues noted during peak times. Distributing static content via CDNs mitigates latency by leveraging proximity to the user. Establishing a read replica for the database dedicated to report queries frees up resources on the primary database, ensuring smoother inventory management. Finally, implementing auto-scaling for API servers is crucial; this allows the system to adjust resources dynamically, maintaining performance during varying loads and avoiding bottlenecks even when demands spike. This comprehensive approach ensures each component contributes efficiently to overall system resilience and responsiveness.
send
light_mode
delete
Question #5
During a remodel, a company's computer equipment was moved to a secure storage room with cameras positioned on both sides of the door. The door is locked using a card reader issued by the security team, and only the security team and department managers have access to the room. The company wants to be able to identify any unauthorized individuals who enter the storage room by following an authorized employee.
Which of the following processes would BEST satisfy this requirement?
Which of the following processes would BEST satisfy this requirement?
- AMonitor camera footage corresponding to a valid access request.Most Voted
- BRequire both security and management to open the door.
- CRequire department managers to review denied-access requests.
- DIssue new entry badges on a weekly basis.
Correct Answer:
A
Reference:
https://www.getkisi.com/access-control
A
Reference:
https://www.getkisi.com/access-control
send
light_mode
delete
Question #6
A company is preparing to deploy a global service.
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
- AInform users regarding what data is stored.Most Voted
- BProvide opt-in/out for marketing messages.
- CProvide data deletion capabilities.Most Voted
- DProvide optional data encryption.
- EGrant data access to third parties.
- FProvide alternative authentication techniques.
Correct Answer:
AC
Reference:
https://gdpr.eu/compliance-checklist-us-companies/

AC
Reference:
https://gdpr.eu/compliance-checklist-us-companies/

send
light_mode
delete
Question #7
A SOC analyst is reviewing malicious activity on an external, exposed web server. During the investigation, the analyst determines specific traffic is not being logged, and there is no visibility from the WAF for the web application.
Which of the following is the MOST likely cause?
Which of the following is the MOST likely cause?
- AThe user agent client is not compatible with the WAF.
- BA certificate on the WAF is expired.
- CHTTP traffic is not forwarding to HTTPS to decrypt.Most Voted
- DOld, vulnerable cipher suites are still being used.
Correct Answer:
B
Reference:
https://aws.amazon.com/premiumsupport/knowledge-center/waf-block-http-requests-no-user-agent/
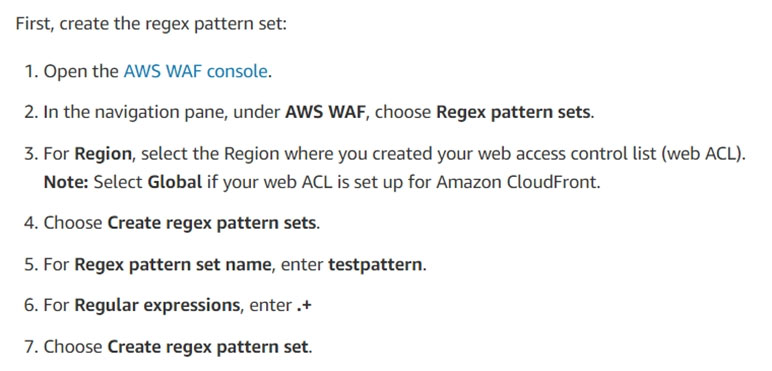
B
Reference:
https://aws.amazon.com/premiumsupport/knowledge-center/waf-block-http-requests-no-user-agent/

send
light_mode
delete
Question #8
A security analyst is reviewing the following output:
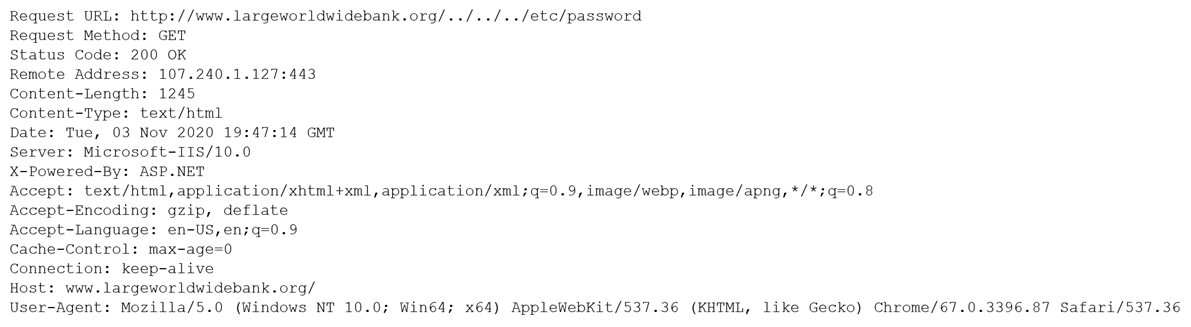
Which of the following would BEST mitigate this type of attack?

Which of the following would BEST mitigate this type of attack?
- AInstalling a network firewall
- BPlacing a WAF inlineMost Voted
- CImplementing an IDS
- DDeploying a honeypot
Correct Answer:
B
B
send
light_mode
delete
Question #9
Which of the following terms refers to the delivery of encryption keys to a CASB or a third-party entity?
- AKey sharing
- BKey distributionMost Voted
- CKey recovery
- DKey escrow
Correct Answer:
D
Reference:
https://www.open.edu/openlearn/ocw/mod/oucontent/view.php?id=48322§ion=1.3
D
Reference:
https://www.open.edu/openlearn/ocw/mod/oucontent/view.php?id=48322§ion=1.3
send
light_mode
delete
Question #10
An organization is implementing a new identity and access management architecture with the following objectives:
✑ Supporting MFA against on-premises infrastructure
✑ Improving the user experience by integrating with SaaS applications
✑ Applying risk-based policies based on location
✑ Performing just-in-time provisioning
Which of the following authentication protocols should the organization implement to support these requirements?
✑ Supporting MFA against on-premises infrastructure
✑ Improving the user experience by integrating with SaaS applications
✑ Applying risk-based policies based on location
✑ Performing just-in-time provisioning
Which of the following authentication protocols should the organization implement to support these requirements?
- AKerberos and TACACS
- BSAML and RADIUS
- COAuth and OpenIDMost Voted
- DOTP and 802.1X
Correct Answer:
D
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/migrate-application-authentication-to-azure-active-directory

D
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/migrate-application-authentication-to-azure-active-directory

send
light_mode
delete
All Pages
