CompTIA CA1-005 Exam Practice Questions (P. 1)
- Full Access (115 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
A company plans to implement a research facility with intellectual property data that should be protected. The following is the security diagram proposed by the security architect:
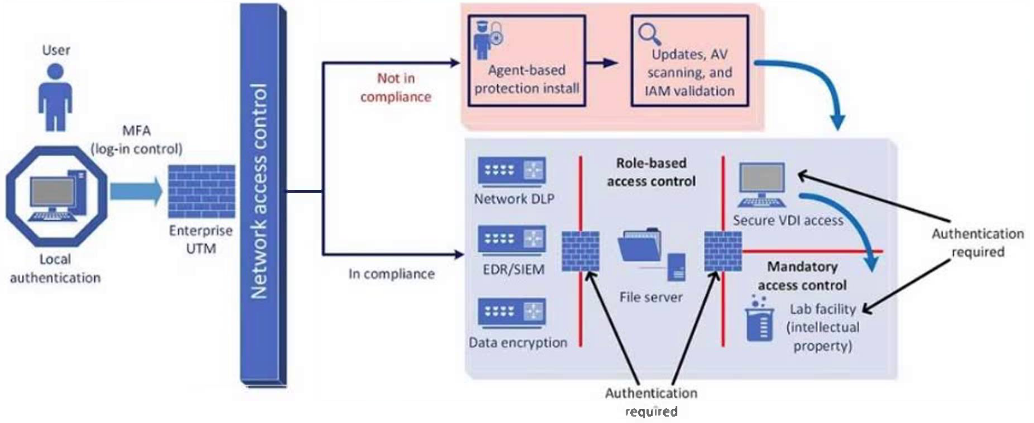
Which of the following security architect models is illustrated by the diagram?

Which of the following security architect models is illustrated by the diagram?
- AIdentity and access management model
- BAgent-based security model
- CPerimeter protection security model
- DZero Trust security model
send
light_mode
delete
Question #2
A financial technology firm works collaboratively with business partners in the industry to share threat intelligence within a central platform. This collaboration gives partner organizations the ability to obtain and share data associated with emerging threats from a variety of adversaries. Which of the following should the organization most likely leverage to facilitate this activity? (Choose two.)
send
light_mode
delete
Question #3
During a gap assessment, an organization notes that BYOD usage is a significant risk. The organization implemented administrative policies prohibiting BYOD usage. However, the organization has not implemented technical controls to prevent the unauthorized use of BYOD assets when accessing the organization's resources. Which of the following solutions should the organization implement to best reduce the risk of BYOD devices? (Choose two.)
- ACloud IAM, to enforce the use of token-based MFA
- BConditional access, to enforce user-to-device binding
- CNAC, to enforce device configuration requirements
- DPAM, to enforce local password policies
- ESD-WAN, to enforce web content filtering through external proxies
- FDLP, to enforce data protection capabilities
send
light_mode
delete
Question #4
A security administrator is performing a gap assessment against a specific OS benchmark. The benchmark requires the following configurations be applied to endpoints:
• Full disk encryption
• Host-based firewall
• Time synchronization
• Password policies
• Application allow listing
• Zero Trust application access
Which of the following solutions best addresses the requirements? (Choose two.)
• Full disk encryption
• Host-based firewall
• Time synchronization
• Password policies
• Application allow listing
• Zero Trust application access
Which of the following solutions best addresses the requirements? (Choose two.)
send
light_mode
delete
Question #5
A global organization is reviewing potential vendors to outsource a critical payroll function. Each vendor's plan includes using local resources in multiple regions to ensure compliance with all regulations. The organization's Chief Information Security Officer is conducting a risk assessment on the potential outsourcing vendors' subprocessors. Which of the following best explains the need for this risk assessment?
- ARisk mitigations must be more comprehensive than the existing payroll provider.
- BDue care must be exercised during all procurement activities.
- CThe responsibility of protecting PII remains with the organization.
- DSpecific regulatory requirements must be met in each jurisdiction.
send
light_mode
delete
All Pages
