CompTIA 220-1102 Exam Practice Questions (P. 1)
- Full Access (701 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
SIMULATION -
Ann, a CEO, has purchased a new consumer-class tablet for personal use, but she is unable to connect to the wireless network. Other users have reported that their personal devices are connecting without issues. She has asked you to assist with getting the device online without adjusting her home WiFi configuration.
INSTRUCTIONS -
Review the network diagrams and device configurations to determine the cause of the problem and resolve any discovered issues.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
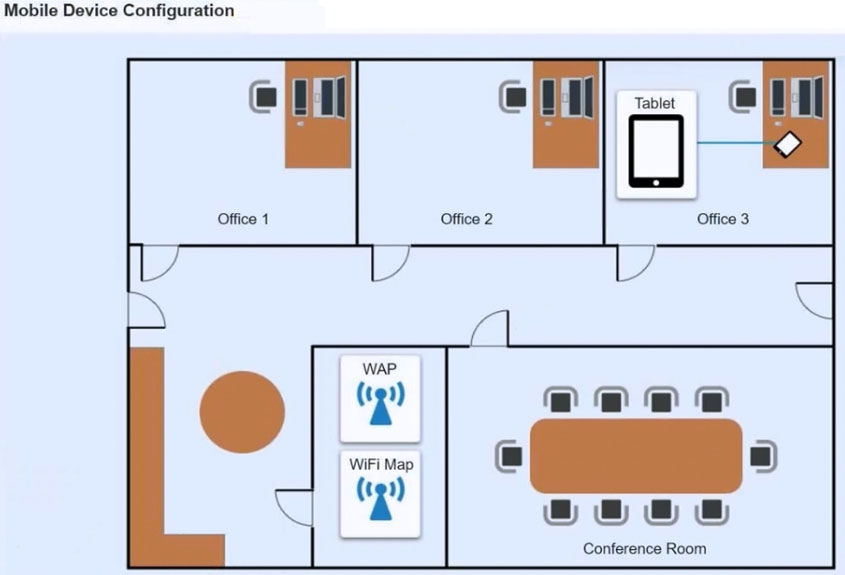
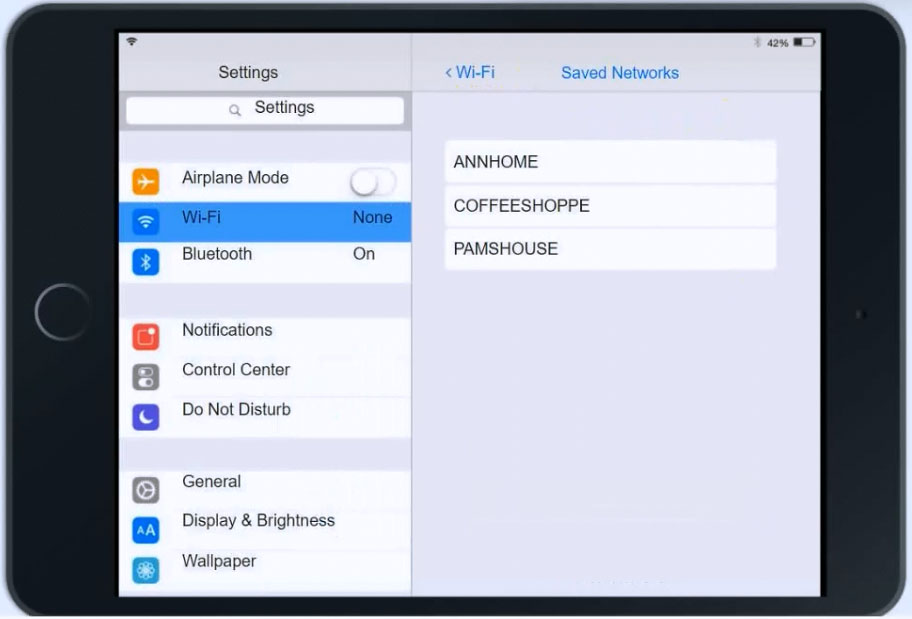
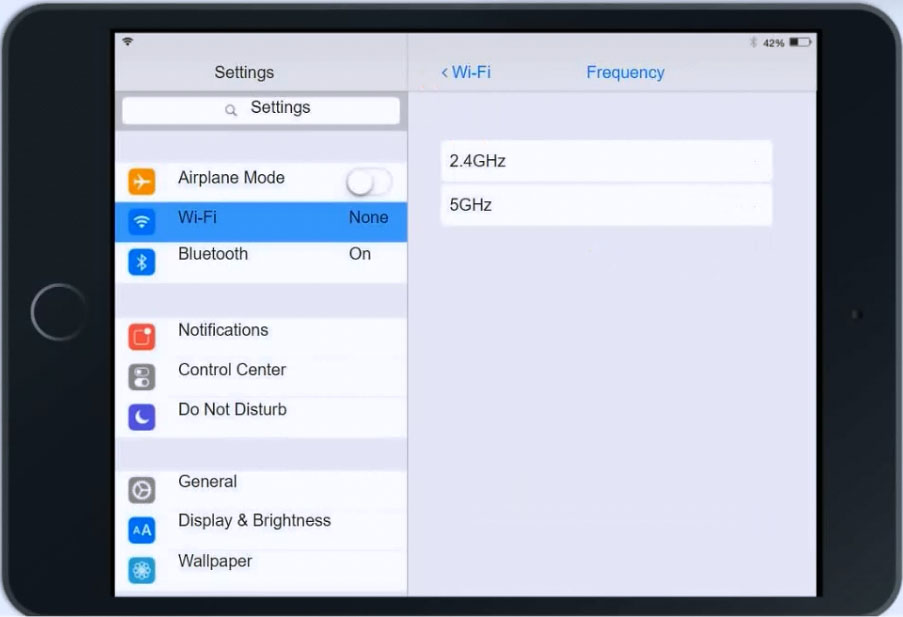
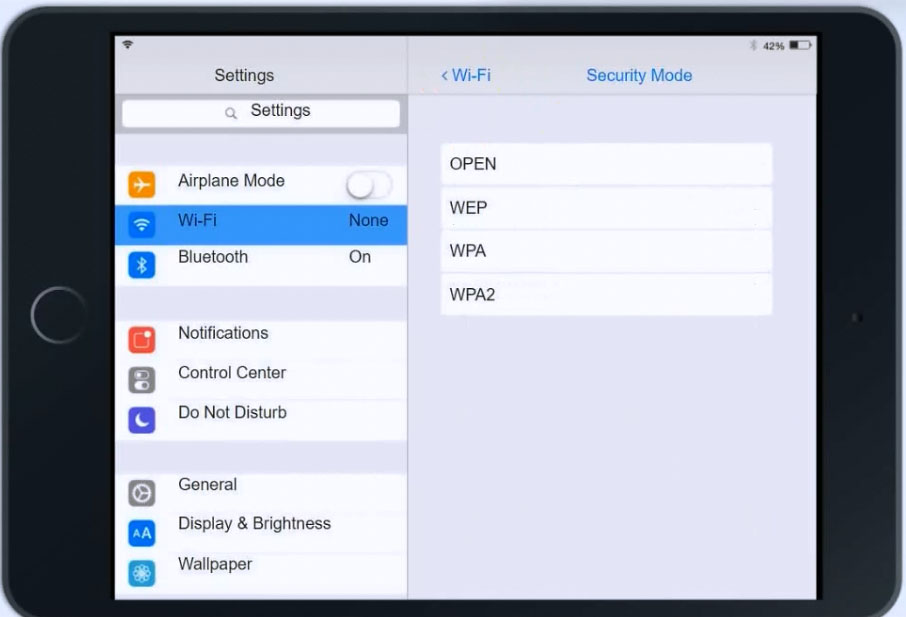
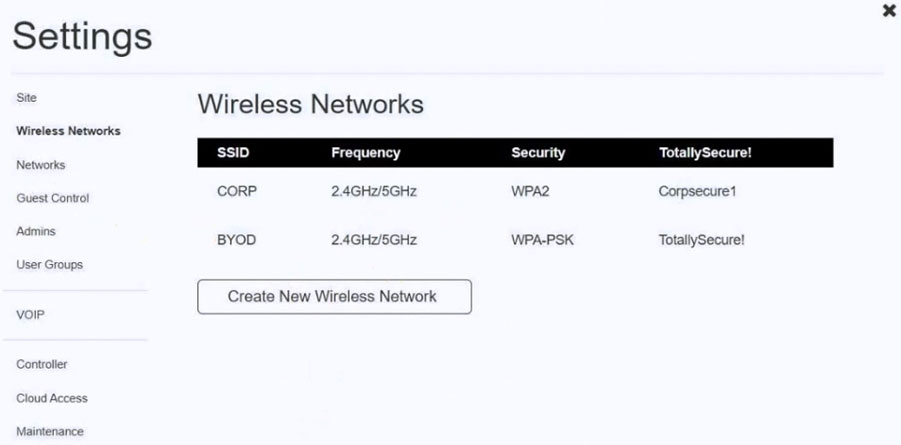
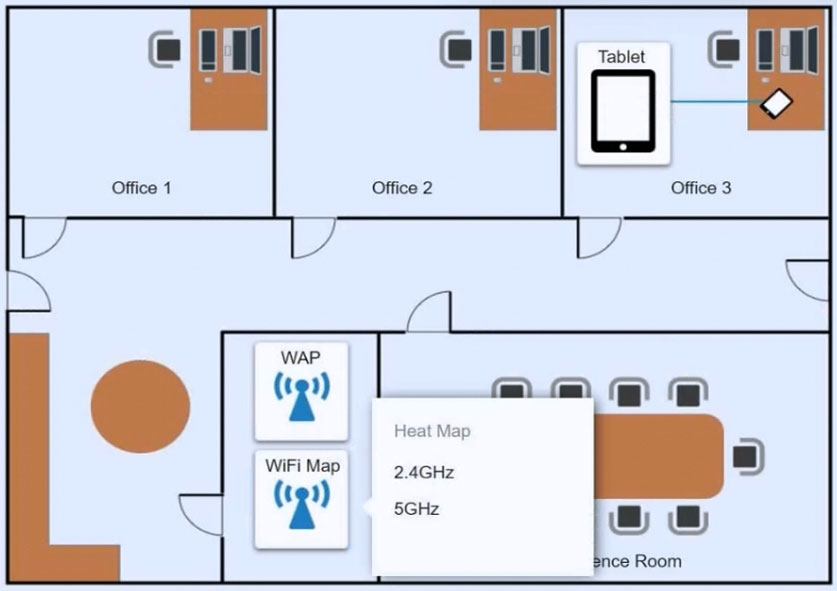
Ann, a CEO, has purchased a new consumer-class tablet for personal use, but she is unable to connect to the wireless network. Other users have reported that their personal devices are connecting without issues. She has asked you to assist with getting the device online without adjusting her home WiFi configuration.
INSTRUCTIONS -
Review the network diagrams and device configurations to determine the cause of the problem and resolve any discovered issues.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.









Correct Answer:
See explanation below.
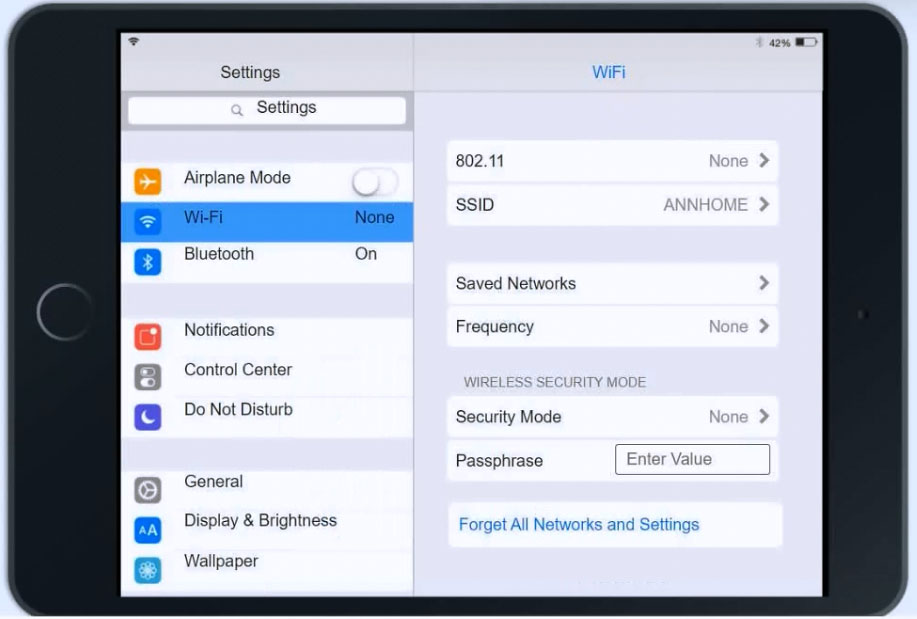
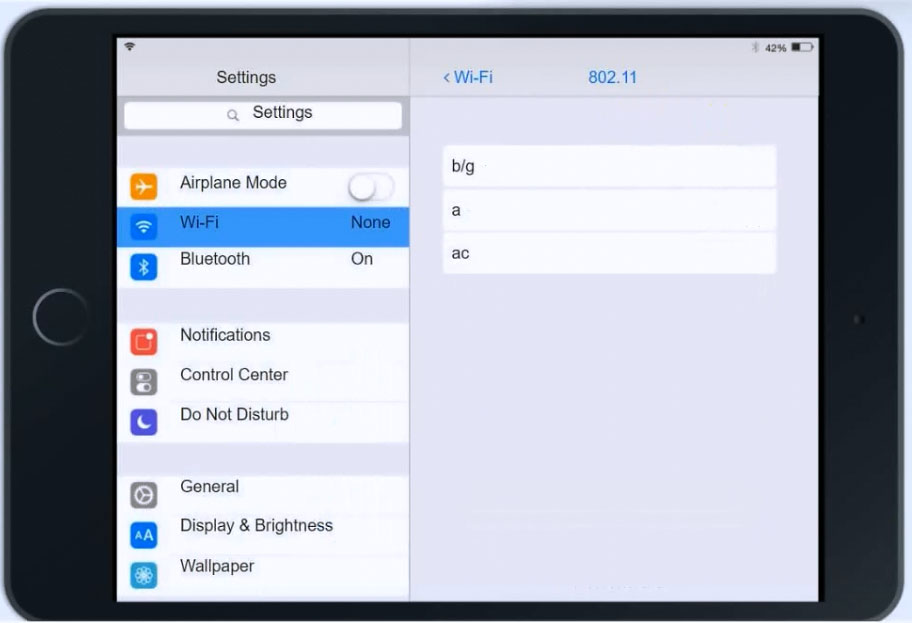
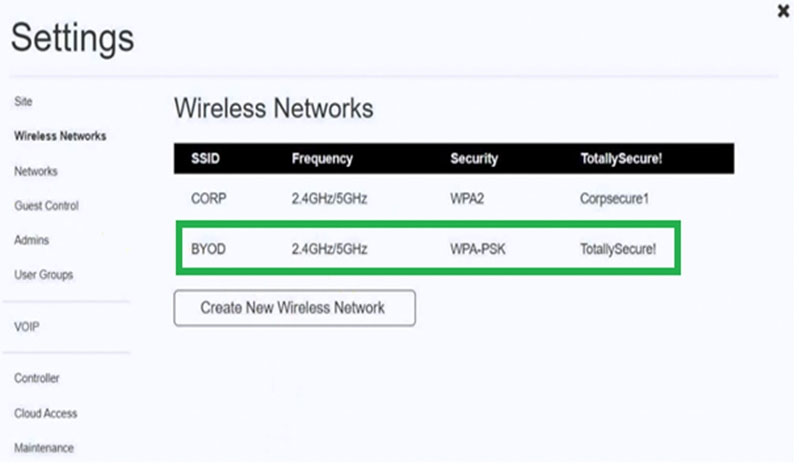
Click on 802.11 and Select ac -
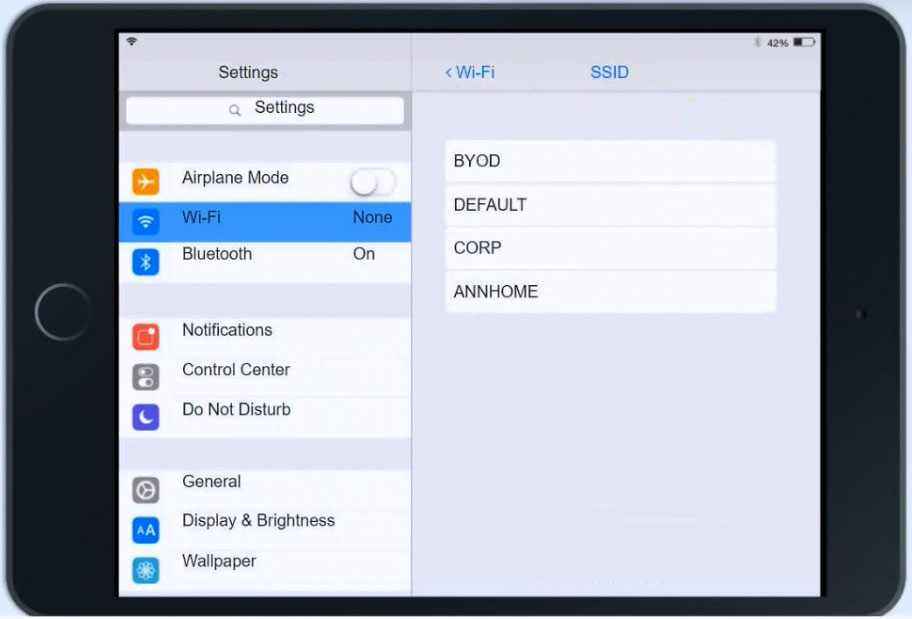
Click on SSID and select BYOD -
Click on Frequency and select 5GHz
At Wireless Security Mode, Click on Security Mode
Select the WPA and the password should be set to TotallySecure!
See explanation below.
Click on 802.11 and Select ac -
Click on SSID and select BYOD -
Click on Frequency and select 5GHz
At Wireless Security Mode, Click on Security Mode
Select the WPA and the password should be set to TotallySecure!

send
light_mode
delete
Question #2
A help desk team lead contacts a systems administrator because the technicians are unable to log in to a Linux server that is used to access tools. When the administrator tries to use remote desktop to log in to the server, the administrator sees the GUI is crashing. Which of the following methods can the administrator use to troubleshoot the server effectively?
- ASFTP
- BSSHMost Voted
- CVNC
- DMSRA
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
SSH is the appropriate choice for troubleshooting the server in this scenario. This method allows administrators to access the server via a command line interface, bypassing the problematic GUI entirely. Using SSH is particularly beneficial when the server's graphical interface is crashing, as it ensures continued access without requiring GUI functionality. This approach is not only secure but also efficient for addressing server issues directly at the command line level.
send
light_mode
delete
Question #3
A company wants to remove information from past users' hard drives in order to reuse the hard drives. Which of the following is the MOST secure method?
- AReinstalling Windows
- BPerforming a quick format
- CUsing disk-wiping softwareMost Voted
- DDeleting all files from command-line interface:
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
The most secure method to ensure all past user data is irrevocably removed from a hard drive is using disk-wiping software. This software is explicitly designed to thoroughly overwrite all locations on the drive with random data, in contrast to quick formatting or merely deleting files, which leave data recoverable. Reinstalling Windows doesn’t address the underlying data remnants, making disk-wiping the superior option for security before reusing drives.
send
light_mode
delete
Question #4
A user is having phone issues after installing a new application that claims to optimize performance. The user downloaded the application directly from the vendor's website and is now experiencing high network utilization and is receiving repeated security warnings. Which of the following should the technician perform FIRST to mitigate the issue?
- AReset the phone to factory settings.
- BUninstall the fraudulent application.Most Voted
- CIncrease the data plan limits.
- DDisable the mobile hotspot.
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Resetting the phone to factory settings may seem like a comprehensive solution to deal with potential malware. However, this method should only be considered when simpler, less disruptive measures fail to resolve the issue. As the user's phone is experiencing problems immediately after installing a new application, it's prudent to first remove the suspicious app. This step is less invasive and directly addresses the source of the problem—particularly when the download has already resulted in excessive network utilization and repeated security warnings. Uninstalling the app is the logical first response to mitigate immediate risks to the device’s security and functionality.
send
light_mode
delete
Question #5
A change advisory board just approved a change request. Which of the following is the MOST likely next step in the change process?
- AEnd user acceptanceMost Voted
- BPerform risk analysis
- CCommunicate to stakeholders
- DSandbox testing
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
The correct sequence after a change advisory board approval typically involves risk analysis, followed by testing and implementation, and concluding with end-user acceptance, as highlighted in CompTIA’s materials. This methodology ensures proper vetting for potential risks after board approvals, allowing for modifications or additional precautions before the wider release or implementation phase. This systematic risk assessment is crucial for maintaining the integrity and security of the IT environment while minimizing disruptive impacts.
send
light_mode
delete
Question #6
A user calls the help desk to report that none of the files on a PC will open. The user also indicates a program on the desktop is requesting payment in exchange for file access. A technician verifies the user's PC is infected with ransomware. Which of the following should the technician do FIRST?
- AScan and remove the malware.
- BSchedule automated malware scans.
- CQuarantine the system.Most Voted
- DDisable System Restore.
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
Quarantining the infected system is indeed the correct first step once ransomware is verified. This process prevents further contamination to other systems and limits the impact of the malware. It's critical to isolate the system immediately to control the spread of the ransomware and mitigate any potential additional damage. Following this, other steps in the malware removal process can take place, like disabling System Restore and performing a thorough scan and removal of the malware.
send
light_mode
delete
Question #7
A company is issuing smartphone to employees and needs to ensure data is secure if the devices are lost or stolen. Which of the following provides the BEST solution?
- AAnti-malware
- BRemote wipeMost Voted
- CLocator applications
- DScreen lock
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Remote wipe effectively addresses the issue of keeping data secure if smartphones are lost or stolen by enabling the deletion of all sensitive information remotely. This ensures that even if the device falls into the wrong hands, the data contained within it cannot be accessed or misused. Screen locks, while basic security features, can often be bypassed and do not offer the same level of data protection as the ability to entirely erase the device's data. This makes remote wipe the best choice for securing data on company-issued smartphones in such scenarios.
send
light_mode
delete
Question #8
A user reports seeing random, seemingly non-malicious advertisement notifications in the Windows 10 Action Center. The notifications indicate the advertisements are coming from a web browser. Which of the following is the BEST solution for a technician to implement?
- ADisable the browser from sending notifications to the Action Center.
- BRun a full antivirus scan on the computer.
- CDisable all Action Center notifications.
- DMove specific site notifications from Allowed to Block.Most Voted
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Running a full antivirus scan as a first response to random browser-generated advertisements might seem extensive, especially if these notifications aren't inherently malicious. Often, such ads are due to site permissions rather than malware. Adjusting browser settings to block specific site notifications directly addresses the issue without the broader impact of disabling all notifications or unnecessary system scans. This approach ensures that only unwanted ads are stopped while preserving useful functionality of both the web browser and the Action Center, making it not only more precise but also more aligned with typical user needs.
send
light_mode
delete
Question #9
After clicking on a link in an email, a Chief Financial Officer (CFO) received the following error:
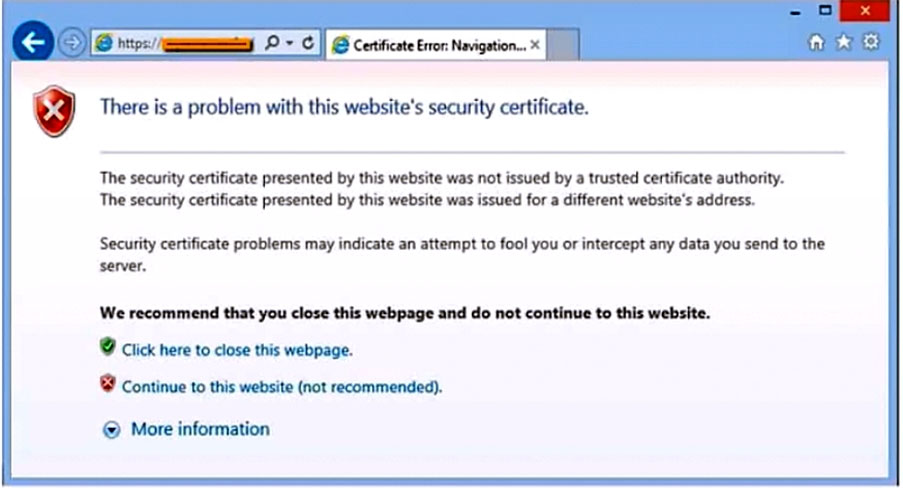
The CFO then reported the incident to a technician. The link is purportedly to the organization's bank. Which of the following should the technician perform FIRST?

The CFO then reported the incident to a technician. The link is purportedly to the organization's bank. Which of the following should the technician perform FIRST?
- AUpdate the browser's CRLs.
- BFile a trouble ticket with the bank.
- CContact the ISP to report the CFO's concern.
- DInstruct the CFO to exit the browser.Most Voted
Correct Answer:
D
D
send
light_mode
delete
Question #10
A help desk technician is troubleshooting a workstation in a SOHO environment that is running above normal system baselines. The technician discovers an unknown executable with a random string name running on the system. The technician terminates the process, and the system returns to normal operation. The technician thinks the issue was an infected file, but the antivirus is not detecting a threat. The technician is concerned other machines may be infected with this unknown virus. Which of the following is the MOST effective way to check other machines on the network for this unknown threat?
- ARun a startup script that removes files by name.
- BProvide a sample to the antivirus vendor.Most Voted
- CManually check each machine.
- DMonitor outbound network traffic.
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Providing a sample of the suspected malware to the antivirus vendor is the most effective approach because it allows the vendor to analyze the threat and potentially update their signature database. This update can then be automatically distributed to all systems using that antivirus, ensuring comprehensive detection and removal of the threat across all machines on the network. This is more efficient and reliable than manually checking each machine, especially when considering the potential for human error and the labor-intensive nature of manual checks.
send
light_mode
delete
All Pages
